Engineering and product leaders often face challenges in maintaining secure and accessible software. When dealing with the complexities of managing in-house or legacy systems, they may neglect a silent adversary: fraud and account abuse.
This issue is becoming more serious as fraudsters exploit weaknesses and use advanced techniques to hide their activities, leading to significant losses, reputational damage, and negative impacts on key performance indicators (KPIs) for businesses. While the financial impact of fraud is relatively easy to measure, it's also crucial to consider how abusive activities can influence other KPIs.
For example, a high incidence of fraud could lead to increased customer complaints, thereby negatively affecting customer satisfaction scores. On the other hand, effective fraud prevention measures can positively influence KPIs, such as enhancing trust and loyalty among users, which in turn can boost user retention rates.
In this post, I'll give an overview of device intelligence and how it works, along with some common challenges in fraud prevention and how device intelligence can help overcome them.
What is device intelligence?
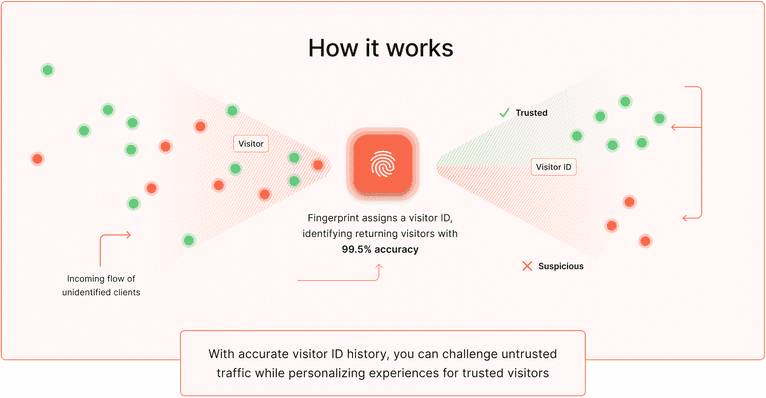
Device intelligence is a method that identifies users by utilizing device fingerprinting as the foundational technique, supplemented by additional methods like VPN detection, incognito mode detection, and IP geolocation. This approach aids those aiming to tackle fraud prevention and detection challenges in their existing technical setups.
This method generates a unique identifier for each visitor, regardless of browser, location, or device type. This visitor identifier remains consistent over time, ensuring a highly accurate visitor ID history. With a comprehensive visitor identifier database, you can scrutinize untrusted traffic while providing a more tailored experience for trusted visitors.
How does device intelligence work?
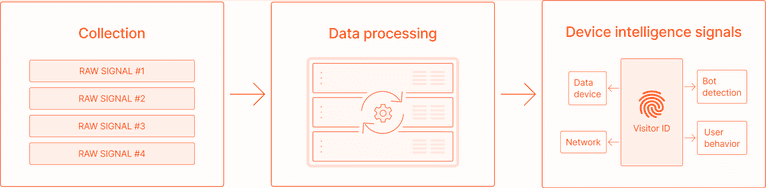
The process begins with the collection of all available raw device information, signals, and attributes. This information is then processed to produce a unique device identifier. Ideally, this identifier should remain stable over months and account for all visits from a specific user, even if some of the device signals or attributes—such as browser type or IP address—change.
Let's explore a few specific signals that form part of a comprehensive device intelligence solution like Fingerprint. We will categorize these into three groups: user behavior signals, network signals, and bot detection signals.
User behavior signals
- Incognito mode detection: Detects if a user is trying to hide their identity or history.
- Browser tamper detection: Identifies browser spoofing incidents and suspicious browser signature anomalies.
- Android tamper detection: Ensures a safe Android mobile application environment by detecting rooted devices.
Network signals
- IP geolocation: Accurately determines the location of the actual IP address.
- VPN detection: Determines if a user is leveraging a VPN to conceal their identity by validating that their IP time zone matches their browser time zone.
- IP blocklist matching: Sees when an IP address matches a known database of malicious actors and spammers.
Bot detection signals
- Browser bot detection: Identifies automated tools, friendly search bots, and other sophisticated threats in real time.
- Android emulator detection: Prevents spam and protects against nefarious Android emulator farms by ensuring the request is coming from a physical device.
Common fraud prevention challenges
Inaccurate data in fraud prevention
Two significant issues arise from inaccuracies in current fraud prevention processes and the data it collects:
- The failure to identify repeat fraudsters
- The inability to differentiate automated threats from humans
For instance, consider a scenario where a fraudster makes multiple purchases using information from different stolen credit cards. Without accurate fraud prevention, the system fails to recognize that these transactions originate from the same device. As a result, each fraudulent transaction is treated as an isolated incident, allowing the fraudster to continue their illegal shopping spree undetected.
Similarly, it becomes challenging to differentiate between automated bots and genuine human users without precise device identification, leading to false positives, where legitimate transactions are flagged as fraudulent, which negatively impacts customer experience and potentially leads to loss of business.
Increased prevalence of bad bots and botnets
Fraudsters program automated threats to mimic human-like device characteristics and behavior, making them incredibly difficult to detect. These bots and botnets masquerade as genuine users, often bypassing security measures and causing significant damage. This type of fraud is also becoming increasingly common, with 15% of Cloudflare customers reporting that they were a target of an HTTP DDoS attack accompanied by a threat or ransom note in 2022.
Automated threats can wreak havoc on websites, leading to distributed denial-of-service (DDoS) attacks, brute-force attacks, and credential stuffing. For instance, the infamous Mirai botnet attack in 2016 utilized a network of infected IoT devices to launch a massive DDoS attack, disrupting major websites worldwide.
Common problems solved by device intelligence
- Payment Fraud: Use Fingerprint for accurate user identification to prevent all forms of payment fraud. It helps keep chargebacks to a minimum, safeguarding your profits and seller reputation.
- Paywall: Fingerprint aids media companies, subscription services, and content creators in monetizing more effectively. It provides accurate visitor identification to address leaky paywall issues.
- Improve Conversion Rates: Fingerprint accurately identifies users, enabling businesses to customize websites by offering targeted promotions or content based on user profiles. It also enhances user experience by reducing the necessity for 2FA/MFA.
- Account Takeover: Fingerprint offers robust account takeover protection for any web application. It ensures customer account security by accurately identifying threats before they become problematic—in fact, Fingerprint is the industry leader in visitor identification accuracy.
- New Account Fraud: Fingerprint helps reduce revenue loss by preventing users from creating multiple or trial accounts. It also assists in preventing users from generating multiple or false reviews.
Top benefits and features of device intelligence
- Improve fraud capabilities: Feed your fraud and risk engines with high-quality data. Leave the “junk in, junk out” scenario behind.
- Streamline trusted visitors: Reducing fraud means a better experience for trusted visitors and returning customers.
- Reduce fraud costs: Detect and prevent instances of fraud costing your business and its customers money.
- Identify visitors intent on carrying out fraud: Identify key characteristics about a visitor, like mismatched time zones, making bad actors easier to identify and manage.
- Increase strength of detection: Surface more data that indicates a bad actor might be trying to hide their IP address or tampered with their device or browser settings.
- Incorporate more data into existing fraud and risk engines: Add to the signals you’re already collecting and fortify your decision engine to make detecting possible instances of fraud easier and more accurate.
Set up time to talk to our team and learn more about how device intelligence can solve your fraud challenges.