Being constantly online exposes businesses to a myriad of cybersecurity threats. One such threat is online fraud on their websites, which can tarnish a business’s reputation and result in substantial financial losses.
This article discusses IP blocklist matching, its benefits and challenges, and how to protect your website from blocked IP addresses.
What is an IP blocklist, and what is IP blocklist matching?
IP blocklist matching is an online security measure that identifies potential fraudsters who attempt to access your website. It works by comparing the IP address of every visitor to a list of IP addresses previously associated with fraudulent activities, known as an IP blocklist or IP blacklist. (Read why blocklist is now the appropriate term instead of blacklist from Vice.)
When an IP address matches one on the known blocklist, you can automatically restrict access, preventing potential fraudsters from committing fraud on your website and conducting malicious activities. This cybersecurity strategy effectively identifies and blocks threats before they can cause costly effects on a website.
An IP blocklist is generally more dynamic and frequently updated based on real-time data and analysis. It includes IP addresses temporarily blocked due to suspicious activities and can be removed from the list once they’re deemed safe.
How do IPs land on these lists?
IP addresses usually land on these lists due to engagement in suspicious activities such as spamming, hacking attempts, or DDoS attacks. The decision to add an IP address to a blocklist hinges on the severity and frequency of these activities.
Fraud prevention solutions identify web traffic and flag unusual behavior. For instance, multiple failed login attempts, rapid-fire form submissions, or high-volume email sending may suggest a bot or fraudster at work. The system adds a particular IP address to the list when it detects such activity.
There are many blocklist and services available; you can learn more about the specific types of lists available, which have been around since about 1997, in addition to how to remove yourself from a blocklist should your IP be mistakenly listed.
Benefits of IP blocklist matching as a fraud prevention tactic
Implementing IP blocklist matching comes with several benefits. We’ve included a few of them below:
- An additional layer of website security: Blocking access to suspicious IPs significantly reduces the risk of data breaches and fraudulent transactions.
- Protecting your website reputation: Instances of fraud erode customer trust significantly if a customer’s data is compromised. Proactively safeguarding your website demonstrates a commitment to customer privacy and security, maintaining your reputation, and fostering customer loyalty.
- Save time and money: Fraudsters will use several different tactics to remain undetected on a website, including using specific IP addresses that may be already on a blocklist. Avoid unnecessary costs and time spent after a fraudulent attack by using IP blocklist matching as part of your fraud prevention strategy.
How IP blocklist matching works
Associating an IP address with a unique users can be completed utilizing various data points to enhance effectiveness and accuracy to blocking the IP address. Here are some of them:
- IP address: The most basic data point is the IP address itself. Any visitor’s IP address is compared against the blocklist to check for any match.
- Geolocation details: This involves determining the physical location of an IP address on a global scale. Certain geographical areas might be associated with higher levels of fraudulent activity, so this information can help further risk assessment.
- Historical data: If an IP address has a history of suspicious activity, add a critical data point for consideration. Past behavior often predicts future actions, so historical data can be instrumental in identifying potential threats.
- Time stamps: The date and time when an IP address tries to access your website can provide vital clues about its intent. For instance, multiple attempts to access your site in quick succession from the same IP address could indicate malicious intent.
- Behavioral patterns: This includes data points related to the user’s actions on the website. For example, an unusually high number of transactions from an IP address or abnormal browsing patterns can serve as red flags.
IP blocklist matching challenges
While IP blocklist matching is a powerful tool in your cybersecurity arsenal, it isn’t without its challenges:
- False positives: One of the critical issues with IP blocklist matching is the potential for false positives, which occurs when legitimate users share an IP address with a previously identified fraudster, leading to the unintentional blocking of legitimate users.
- Dynamic IP addresses: Internet service providers (ISPs) often allocate dynamic IP addresses to their users, which change periodically. A fraudster might use one IP address for malicious activities and then move on to another, leaving an innocent user with the blocked IP address.
- VPN and proxy services: Fraudsters often use VPNs or proxy services to hide their real IP addresses, making it harder to identify and block them accurately.
- Maintenance effort: Maintaining an up-to-date IP blocklist can be time-consuming. It requires constant monitoring and updating to ensure its effectiveness.
- Capacity limitations: Different platforms have different capacity limits for blocklists. For instance, PAN-OS 7.1.x and later can support a maximum of 30 external blocklists, each containing the maximum number of addresses kept by the platform. Similarly, Exchange Online Protection allows around 1,200-1,300 entries on their IP Allow or IP Block list.
- Management challenges: Managing a large IP blocklist can be challenging, especially when dealing with IP ranges and updating the list with new threats. Some platforms limit the number of clients to allow listing and blocking, like Cisco Meraki, which has a limit of 3,000 clients.
Despite these challenges, IP blocklist matching remains a valuable tool. We recommend finding a fraud prevention solution that does the actual blocklist matching and maintenance for you, such as a device intelligence solution.
Using device intelligence for IP blocklist matching
A device intelligence platform, like Fingerprint, can help you identify every device that visits your website or uses your software from visit to sign-up to checkout to return visits with industry-leading accuracy.
Device intelligence is a powerful tool businesses can harness for fraud detection and prevention. It involves analyzing and monitoring device attributes and behaviors to identify potential fraudulent activities. For instance, a company can use device intelligence to collect and analyze data like IP addresses, browser versions, screen resolutions, and dozens of additional attributes. When combined, these signals and attributes create a unique digital identifier for each user, which remains accurate and stable for upwards of months, helping businesses to recognize and block potential fraudsters.
One powerful example is if a user attempts to make a transaction or access sensitive information from a device that doesn’t match their usual profile, Fingerprint can help businesses flag this visit as suspicious. It could signify a fraudster trying to use stolen login credentials.
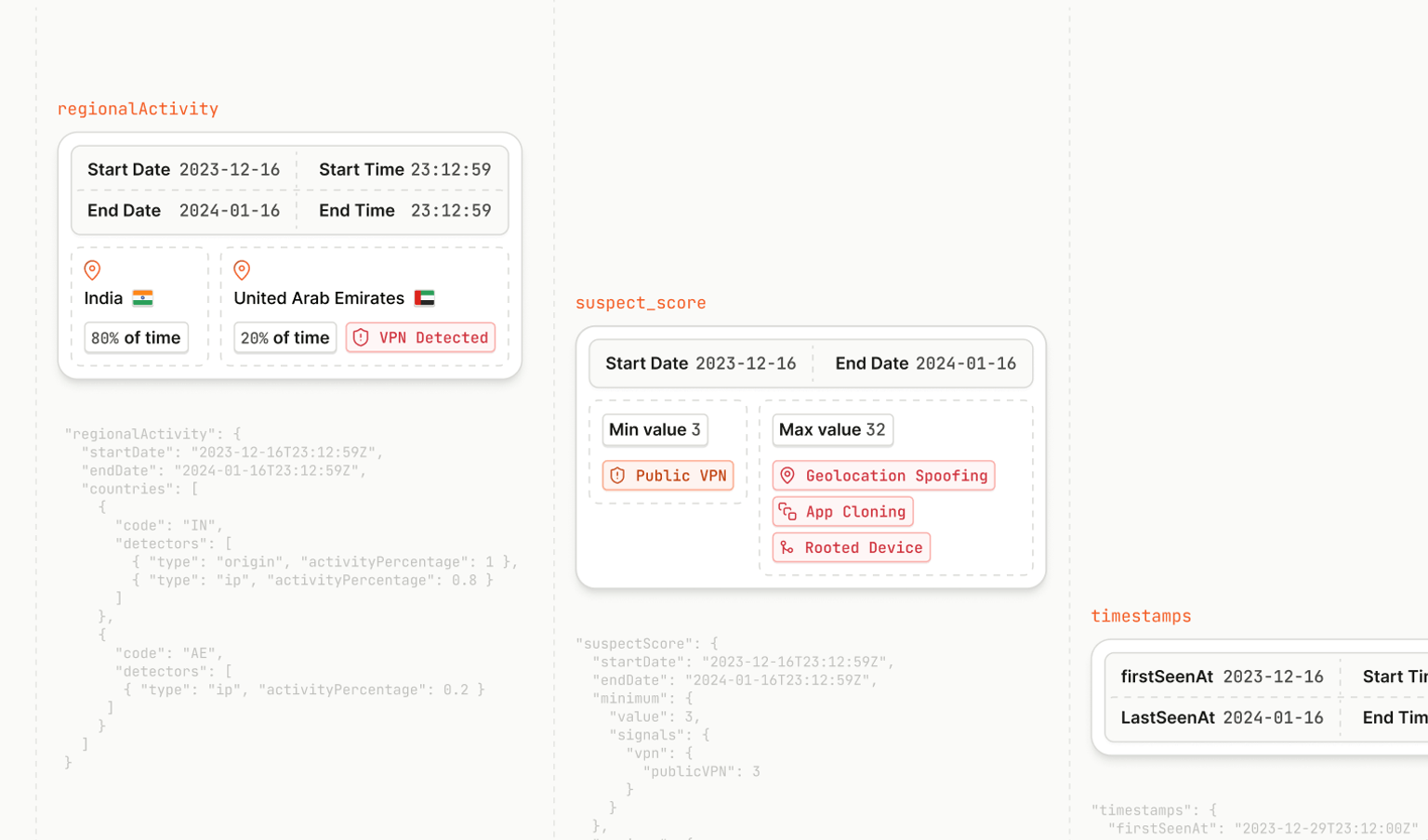
Fingerprint Smart Signals, a collection of identifiers that provides highly accurate and sustained device identifiers, including out-of-the-box IP blocklist matching. Here, you can learn more about the full suite of Smart Signals, including browser bot detection, VPN detection, rooted device detection, and more.