With millions of apps on the Google Play Store, fraudsters always seek new ways to exploit vulnerabilities, steal data, or generate illegitimate revenue from them through malicious means. One of the ways to prevent these attacks is by using Google's Play Integrity API, a powerful tool designed to help app developers detect and mitigate various types of fraud and suspicious activity.
Developers can request the Play Integrity API at important moments. Then, the Integrity API determines if the user actions come from your legitimate app installed by Google Play and a genuine Android device. These checks can help developers identify potential threats and protect their apps and users from abuse, unauthorized access, and attacks.
But is it enough? While the Play Integrity API does provide a good line of defense, it does not give a complete perspective of the users of your apps. To fight fraud effectively, you need a combination of additional signals to get the best information about a user.
In this article, we'll look at the Play Integrity API and explore the information it provides to aid in fraud detection. We'll also examine the limitations of relying solely on this API and discuss the importance of implementing a comprehensive security strategy to protect your app against fraudsters.
What is the Google Play Integrity API?
The Google Play Integrity API helps developers assess the integrity of an Android application and the device it's running on. It provides information on whether the app is running on a genuine Android device and whether it has been tampered with.
The API can help detect potentially harmful interactions from rooted devices, emulators, or modified apps. It's particularly useful for apps requiring high security and integrity, such as banking or gaming apps, to prevent cheating or fraud.
To access the API, a developer starts by enabling it within their Google Cloud Console for a specific project. This setup involves navigating to the API & Services section, finding the Play Integrity API, and activating it. Next, the app is prepared by adding the necessary Play Integrity API dependency in the app’s build.gradle file, ensuring the app is ready to interact with the API.
The developer then implements logic in the app to request an integrity token from the Integrity API and send it to the app's server. The server validates this token with the Integrity API to verify the app and device's integrity. The server can make informed decisions on handling requests to ensure a secure app environment based on this verification data.
What data does the Google Play Integrity API provide?
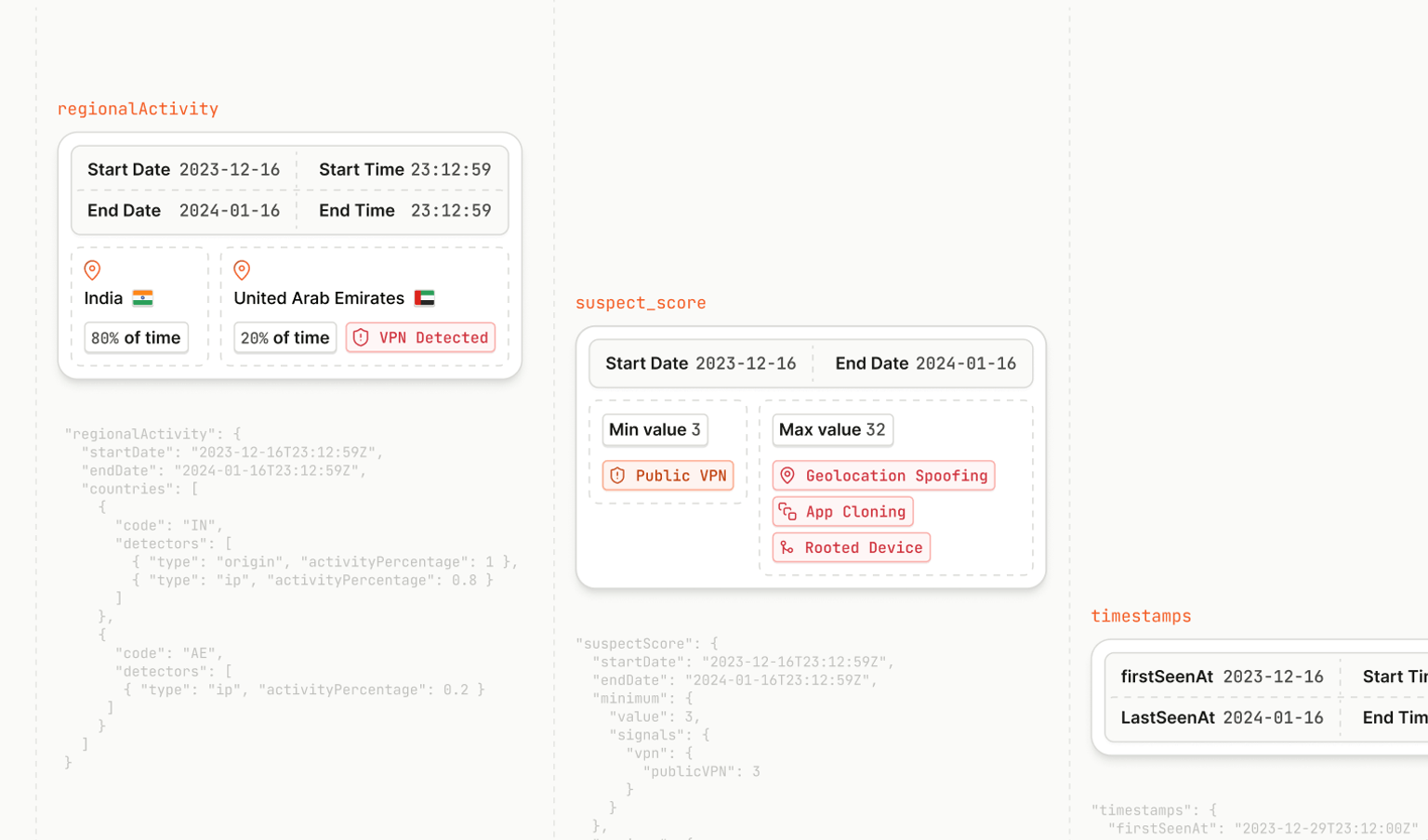
When requesting the integrity information, the API responds with an integrity verdict. This verdict is a plain-text JSON object with properties describing the validity of the device, app, and account making the requests to your server.
Let’s look at each of the properties returned from the API:
{
"requestDetails": { ... },
"appIntegrity": { ... },
"deviceIntegrity": { ... },
"accountDetails": { ... },
"environmentDetails": { ... }
}requestDetails
The first property provided contains information about the original Play Integrity API request. It includes information the developer provided, like the requestHash or nonce, and a timestamp for the request. Developers can use this data to verify the payload by ensuring the details match what the app sent in the original request.
appIntegrity
appIntegrity is the first of the app checks, or verdicts, from the Play Integrity API and contains package-related data. The most important property is the appRecognitionVerdict. This value can be either:
PLAY_RECOGNIZED: The app and certificate match what Google Play originally distributed from the developer.UNRECOGNIZED_VERSION: The certificate or package name doesn’t match what Google Play has in its records for the app.UNEVALUATED: The integrity of the app was not able to be evaluated. A missing requirement or detecting the device as untrustworthy might be causing this.
In essence, appIntegrity lets developers know if the app requesting their server is their genuine app, which they uploaded to the Play Store, instead of one cloned by users creating multiple instances of the same app on their device.
While legitimate reasons exist to clone an app, like separating work and personal accounts, fraudsters can also exploit app cloning for malicious activities. Fraudsters can modify the cloned app to take advantage of promotions or attempt to unauthorized access other user accounts. Detecting these illegitimate apps can significantly help to prevent actions from malicious clones.
deviceIntegrity
The following property returned from the Play Integrity API concerns the device. deviceIntegrity currently only has one value by default, the deviceRecognitionVerdict. This value is determined based on various possibilities, such as whether or not the device passes Google's system integrity checks and Android compatibility requirements.
The values vary depending on how the developer configures their setup and whether they published the app on Google Play or Google Play for PC. All the responses are similar, such as MEETS_DEVICE_INTEGRITY or MEETS_VIRTUAL_INTEGRITY. It lets the developer know if the app is running on an Android-powered device or Android-powered emulator with Google Play services and whether or not it passes basic system integrity checks.
If the API sends no value for the deviceRecognitionVerdict, the app is running on a device that is likely compromised or rooted or is using an emulator that doesn't pass integrity checks.
If the developer opts in, they can see an additional value, the recentDeviceActivity property, which is in beta when writing this article. This property provides a level from 0 to 4 that indicates how often your app requested an integrity token for a device within the last hour.
You can use this activity level to protect your app against unexpected, overly active devices that might be attempting an attack. Depending on the user actions the developer requests integrity verdicts for and the particular use case, certain levels may prompt blocking access to your app server.
accountDetails
The accountDetails property gives some additional information on the app licensing status. It contains appLicensingVerdict, which provides information on whether the user installed or purchased the app from Google Play or if the app was side-loaded.
The API returns either LICENSED, UNLICENSED, or UNEVALUATED. If any app misses requirements, such as an unknown app version or untrustworthy device, or if the user is not signed in to Google Play, it returns UNEVALUATED.
environmentDetails
Within the environmentDetails is an optional field playProtectVerdict which is returned if the developer has opted into the Play Protect verdict. It returns a range of values to indicate risk from NO_ISSUES when Play Protect is turned on to HIGH_RISK where it is off and dangerous has been installed on the device.
It may also return NO_DATA if Play Protect is turned but hasn’t yet performed a scan, or UNEVALUATED if the device is untrustworthy or the account is not licensed.
What’s missing in the Google Play Integrity API for preventing fraud
The Google Play Integrity API is designed to help protect Android apps from common threats, but it has a few gaps regarding comprehensive fraud prevention. These gaps come from the API's limited scope and the incomplete information needed for effectively preventing fraud.
One limitation is that the Google Play Integrity API operates solely within the Google Play ecosystem, limiting its visibility to only a subset of potential security threats. The API does not cover other aspects, like factory resets, VPN detection, or Frida detection.
Another limitation is that the Google Play Integrity API relies on users signing into Google Play to determine some of its verdicts. These verdicts cannot be relied upon and can create blind spots for activities outside traditional pathways.
Practices like rooting devices and cloning apps are common in the Android ecosystem, not just niche activities. While these actions can potentially enable fraudulent behavior, they also have legitimate use cases. The Google Play Integrity API lacks the additional data and insights to help developers understand the intent behind these actions and make informed decisions to prevent fraud effectively.
Expanding fraud detection with device intelligence
While a foundational tool, the Google Play Integrity API's scope in fraud prevention is limited. A broader, more inclusive approach is necessary to protect apps effectively.
Fingerprint’s Smart Signals address these gaps comprehensively, offering a richer, more nuanced approach to protecting mobile applications from fraud. Not only do we provide more information for developers to use to make decisions, but most of our signals are available on both Android and iOS devices.
In addition to Google’s Play Integrity APIs, leveraging Fingerprint’s mobile Smart Signals gives app developers access to:
Android Emulator Detection
Distinguish between genuine devices vs applications being run on an emulator. While emulator usage is common in development and testing phases, it can be exploited for fraud. This signal adds to the device integrity checks found in the Play Integrity API, focusing on distinguishing real users from potentially malicious systems operating on emulators.
Rooted Device Detection
Detect whether an Android device has been rooted and potentially has bypassed built-in security measures. Rooted devices pose a higher risk as they can undermine app security mechanisms, making them a tool for fraud. Our signal complements the Play Integrity API’s device integrity verdicts, enabling developers to make more informed decisions regarding the device’s trustworthiness.
Cloned App Detection
Cloned App Detection targets users who create multiple instances of the same app on their device. By identifying such clones, we support the app integrity goals shared with the Play Integrity API, ensuring that only genuine applications engage with your server.
Factory Reset Detection
Factory Reset Detection reveals the last time a device underwent a factory reset, a useful piece of information since frequent resets may suggest a device is involved in fraudulent activities. This signal provides unique information about device behavior that the Play Integrity API doesn’t cover, enriching the context for risk assessment and fraud prevention strategies.
Frida Detection
The presence of Frida, a tool commonly used for reverse-engineering applications, signals a sophisticated fraudster could be attempting to exploit your app. Detecting Frida goes beyond the capabilities of the Integrity API by detecting advanced and modification attempts, warning developers of potential security breaches.
IP Geolocation & Geolocation Spoofing Detection
A frequently used tactic in fraud schemes is manipulating GPS data to circumvent location-based controls or engage in location-specific malicious activities. Our geolocation spoofing detection signal fills a gap not addressed by the Integrity API. Detecting spoofing attempts and getting detailed insights into the geographical origin of a user's IP address helps developers ensure the geographical integrity of their apps.
IP Blocklist Matching
Our IP Blocklist Matching signal lets developers identify traffic from IP addresses associated with malicious activities. This detection can preemptively stop a range of threats and fraud attempts. This signal ensures known fraudsters are barred from interaction and is not found in the Google Play Integrity API.
VPN Detection
VPN Detection identifies users who use VPN services to hide their original IP addresses, which can potentially be a sign of fraudulent activity. This signal deepens the analysis of the user’s network integrity and authenticity in combination with other signals and adds additional layers of data not provided by the Integrity API.
High-Activity Device
The High-Activity Device signal flags devices exhibiting an unusual activity level based on an app's typical usage. This higher-than-normal activity could indicate automated scripts or bot usage. This goes hand-in-hand with the recent beta device activity checks of the Integrity API and aids in detecting automated fraud and abuse scenarios early.
Conclusion
Using Fingerprint's suite of mobile Smart Signals with insights from the Google Play Integrity API, developers gain a comprehensive toolkit for understanding user activity and preventing fraud. This combination enables a layered, nuanced approach, elevating app security and protecting apps and their users against various threats.
Fingerprint's Smart Signals bridge the gaps in the Play Integrity API, enriching it with deeper, more granular insights that empower developers to fortify their apps more effectively.
Fingerprint is easily accessible through user-friendly APIs, making it a seamless addition to any app development toolkit. Designed for efficiency, our low latency ensures enhanced security without compromising performance, allowing developers to create exceptional, secure apps.
If you want to learn more about how you can expand your app security with Fingerprint Smart Signals contact our team or start a free trial to test them out yourself!
FAQ
The Play Integrity API is a Google tool designed to help Android app developers assess the integrity of app requests and the devices they’re running on. It verifies whether the app is running on a genuine Android device, if it's been tampered with, or if it was installed from Google Play. This information helps developers detect fraudulent activities and secure apps against unauthorized use and abuse.
While helpful, the Google Play Integrity API doesn't cover aspects outside its ecosystem, like VPN detection or geolocation spoofing, which provide useful information for preventing fraud. Relying on it alone leaves gaps in detecting broader security threats.
Yes, Fingerprint’s Smart Signals offer comprehensive fraud detection that works on Android, iOS, and the web. We provide various signals for fraud detection, including VPN detection, geolocation spoofing detection, tamper detection, and more.