Creating reliable, user-friendly, and secure websites necessitates accurately identifying visitors to prevent malicious activities. With stringent browser privacy settings and the prevalent use of ad blockers, this can be challenging, particularly if relying on third-party cookies or loading scripts externally.
Fingerprint’s device intelligence platform provides advanced visitor identification APIs, outperforming older, less effective methods. However, fully integrating these APIs into your website is crucial to achieving optimal identification accuracy. If not, ad blockers, utilized by approximately 40% of online users, could interfere with your identification requests. Additionally, browsers are increasingly restricting third-party cookies, and a full integration additionally allows the setting of long-lasting first-party cookies for visitor identification.
We offer proxy integrations for major cloud providers such as Cloudflare and Azure Front Door to streamline the integration of Fingerprint’s Visitor Identification into your site. These proxies serve as intermediaries, handling identification and script requests between your site and our APIs through your cloud infrastructure.
This article overviews AWS CloudFront and Fingerprint’s APIs and explains how you can seamlessly integrate the two using our proxy integration for the most accurate visitor identification.
What is AWS CloudFront?
AWS CloudFront is a highly regarded content delivery network (CDN) service from Amazon Web Services aimed at improving web applications' speed, reliability, and security. With a network stretching across 550+ locations worldwide, it delivers content with low latency and high data transfer rates.
CloudFront's core mission is to accelerate content distribution, whether it's websites, streaming media, or API calls. It seamlessly integrates with other Amazon services, providing enhanced website security through traffic encryption and access controls. Additionally, CloudFront allows developers to execute code closer to their users using serverless edge computing. By leveraging CloudFront, developers can ensure that their applications are fast, secure, and highly performant, delivering an exceptional experience to end-users.
What is Fingerprint?
Fingerprint is a powerful device intelligence platform that helps businesses identify visitors on the web and mobile. Its primary purposes are preventing fraud, improving user experiences, and understanding website traffic.
Fingerprint visitor identification analyzes over 70 identification signals to generate highly accurate visitor identifiers. It can identify up to 99.5% of returning visitors using fingerprinting, fuzzy matching, and server-side techniques and assigns a unique visitor identifier that remains consistent for months or years.
In addition, Fingerprint’s Smart Signals provide real-time intelligence about visitors, including whether they are using a VPN, in incognito mode, or identified as a bot. This valuable data can create more intelligent workflows to secure websites.
The Benefits of Using a Proxy Integration
A proxy integration, such as the one provided by Fingerprint for CloudFront, solves the challenges of identifying visitors caused by strict browser privacy policies and ad blockers. It handles visitor identification requests directly from your site and offers additional advantages over loading the Fingerprint JavaScript agent from our CDN.
Enhanced Accuracy
Using the CloudFront proxy instead of the CDN version of Fingerprint improves precision and accuracy, particularly on browsers such as Safari or Firefox, known for their strict privacy features.
Cookie Longevity
Fingerprint does not solely rely on cookies; however, the user’s browser will now recognize any cookies used to identify your visitors as first-party, extending their lifespan and enhancing the longevity of visitor identifiers.
Ad Blocker Compatibility
Using the proxy enables the full functioning of the Fingerprint JS agent by allowing identification requests to come from the same site URL, making them resistant to most ad blockers.
Simplified Compliance
The integration script drops all the cookies sent from the origin website, removing unnecessary information. For additional insight and control, identification requests can be combined with AWS features like CloudWatch. Additionally, its open-source code ensures easy verification and auditing to align with compliance requirements.
Scalability
Enjoy the benefits of a first-party device intelligence integration while serving all your customers, regardless of scale, across multiple subdomains and paths.
The Components of the Fingerprint CloudFront Proxy Integration
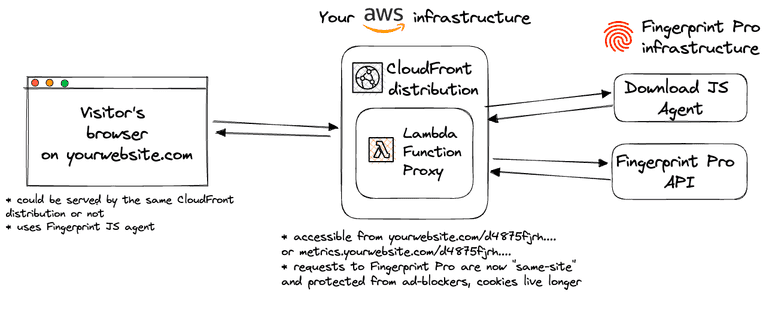
CloudFront Distribution: Regardless of whether your site runs on AWS CloudFront, a CloudFront distribution is necessary for the proxy integration. If your site already uses CloudFront, you can use the same distribution to maximize identification accuracy. If not, you can create a new CloudFront distribution specifically for proxy integration.
AWS Lambda Functions: The integration uses Lambda functions to proxy script loading and identification requests. Additionally, they will be used to update the integration, ensuring you have the latest fingerprinting client-side logic. The functions will be available on a specific path on your site, and the rest of your site will not be affected. There is also additional cache behavior that will enable the use of Lambda functions for proxying requests.
Fingerprint CloudFormation Template & Stack: The Lambda functions and corresponding settings, such as execution role and cache policy, are provided as a CloudFormation application. The entire CloudFormation stack and the Lambda functions' code are open-source and available on GitHub.
Setting Up the CloudFront Integration
There are a few prerequisites before you start setting up our CloudFront proxy integration.:
- To use AWS CloudFront, you must have an AWS account.
- Optional: An existing CloudFront distribution that serves your site’s content, configured to serve content on the same eTLD + 1 or any of its subdomains. If your application isn't run on CloudFront, you can create a new CloudFront distribution during the setup.
- A Fingerprint Enterprise account plan is required to use the CloudFront integration.
Setup Overview
Setting up the integration requires going through the following steps. We're providing a high-level view here, but please look at our documentation for the full step-by-step process.
- Issue a proxy secret in the Fingerprint Dashboard.
- Create path variables used by the AWS configuration and JavaScript agent configuration on your website.
- Install the CloudFormation application containing all the necessary resources for the integration.
- Configure the CloudFront distribution with the integration's Lambda function and cache behavior.
- Configure the Fingerprint JavaScript agent on your website or client application.
- Connect your integration to the Fingerprint Dashboard to enable automatic updates.
Once you've successfully set up the integration, the Fingerprint dashboard integration page will show Status: Connected, and Fingerprint will automatically keep your integration up to date. You will also be able to monitor and manage the integration from within the dashboard to ensure identification requests are coming through and catch errors.
Conclusion
Integrating CloudFront with Fingerprint significantly improves your ability to identify visitors on your website. With our integration, you can route Fingerprint API requests via a CloudFront proxy, ensuring that JavaScript agent requests and identification signals avoid possible blocks. With browsers enforcing stricter measures and increasing ad blocker usage, maintaining unobstructed visitor identification processes is crucial.
If identification requests or signals are blocked, you risk losing crucial data for identifying potential threats or delivering smooth user experiences. However, our proxy integration allows you to fully leverage Fingerprint Pro's ability to identify 99.5% of visitors. This ensures you gain the essential data necessary for providing your users with outstanding and secure experiences.
For additional details, check out our comprehensive guide on the CloudFront proxy integration or browse our full array of integrations for various cloud services. To understand how a proxy integration can enhance the accuracy of your visitor identification, feel free to reach out to our sales team.