To counteract cybercrime, identity theft, and data breaches, many internet users are adopting privacy-focused solutions such as virtual private networks (VPNs) and Tor.
VPNs and Tor both give anonymity by shielding the connected device's true IP address given by their internet service provider through encryption. This means that when the user browses websites or services that track device data, tracking tools are unable to pinpoint their actual IP. It not only fortifies privacy but also spares the user from hyper-targeted ads on social media and search engines.
While both tools aim for anonymity, they have different approaches. VPNs use specific servers to route the user's traffic through, while Tor relies on a peer-to-peer overlay network to route the user's connection over several randomly selected nodes before reaching the destination.
This article dives into how VPNs and Tor work, whether you're looking for the best solution to ensure your privacy or want to ensure the security and integrity of your applications. It also explains how browser fingerprinting can help differentiate legitimate users from cybercriminals even if they use VPNs and Tor.
What Are VPNs and How Are They Used?
VPNs are services designed to encrypt the user's internet traffic. They operate by routing their internet connection through a server of the user's choosing, which might be located anywhere in the world. This system not only hides the device's original IP address but also encrypts all the data being sent to and received from it.
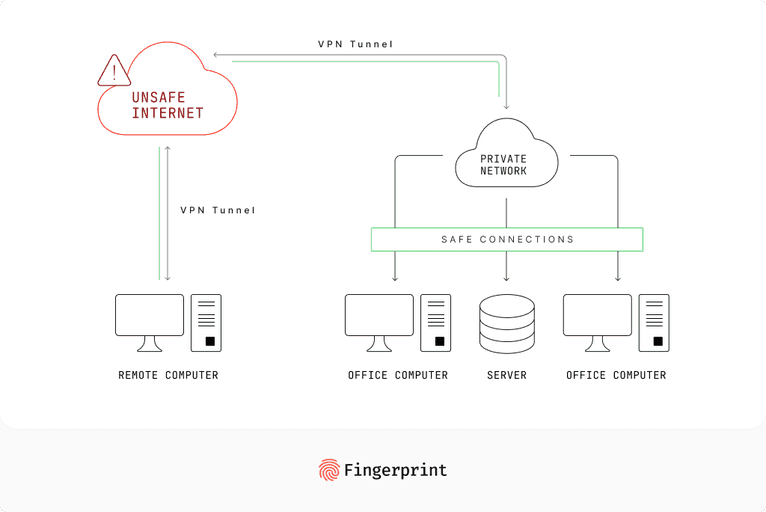
A vast array of VPN providers can be found on the market. Free or low-cost VPNs offer limited servers and slower speeds and might maintain logs. (The concern? If a VPN logs your activities, who's to say they won't sell your data?)
Users who value genuine privacy without compromising on speed rather opt for solutions like WireGuard or NordVPN with cutting-edge VPN tech, swift connections, and the ability to outsmart the geolocation barriers of platforms like Netflix and YouTube.
VPNs provide many benefits:
- Ensuring privacy and anonymity: VPNs mask the device's IP address, rendering it challenging for third parties, including the ISP, to track the user's online activities.
- Bypassing geo-restrictions: They allow access to content that may be restricted in the user's country of residence.
- Ensuring safety on public Wi-Fi: Using public Wi-Fi without a VPN can expose data to cybercriminals. VPNs ensure that the connection remains encrypted.
- Avoiding bandwidth throttling: Some ISPs intentionally slow down the provided connection when the user engages in bandwidth-heavy activities like streaming. A VPN can prevent this throttling.
While many VPN use cases are legitimate, VPNs can also provide cover for malicious actors using them for illegitimate purposes:
- Fraudulent activities: Cybercriminals can use a VPN to mask their real IP addresses while engaging in fraudulent schemes such as phishing, online scams, and financial fraud.
- Cyberattacks: VPNs can be used to launch cyberattacks, including distributed denial of service (DDoS) attacks that overload websites or networks with traffic to disrupt their functions, directly affecting their availability.
- Illegal content sharing: Individuals can use VPNs to bypass copyright restrictions and anonymously share copyrighted content such as movies, music, or software.
- Hacking and unauthorized access: Hackers can employ VPNs to hide their identities while attempting to gain unauthorized access to sensitive systems, networks, or accounts.
What Is Tor and How Does It Work?
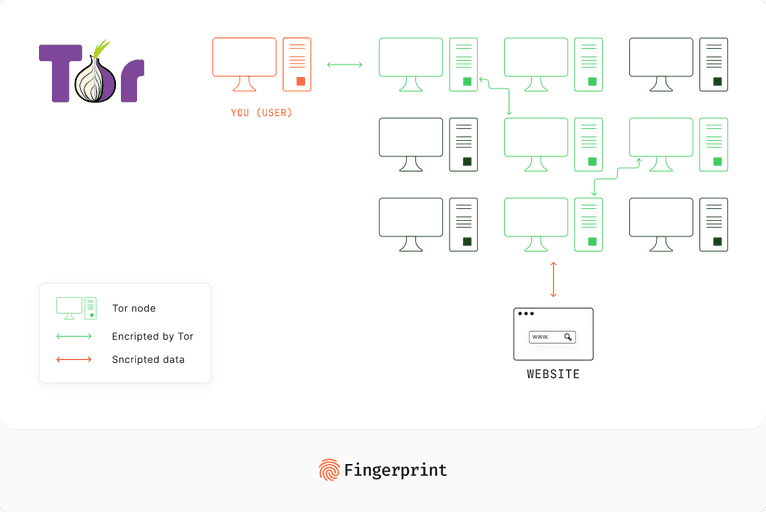
Unlike VPNs, Tor, short for The Onion Router, routes the connection through several randomly selected servers (or nodes) before it reaches its final destination. This routing method employs multiple layers of encryption to prevent both the source and the destination from accessing the user's data sent over the network, akin to the layers of an onion.
Tor's architecture is more complicated and harder to understand than VPNs because of how it works. Unlike VPNs, data does not travel through an encrypted "tunnel." Instead, it hops from node to node (nodes play the role of servers in a VPN scheme), and the system is designed in a way that no single node can know both the user's IP and their accessed content simultaneously.
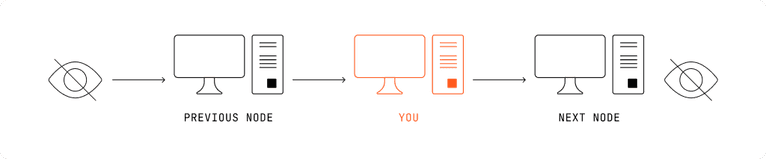
Tor operates in three stages:
- Entry relay: Once the data is encrypted, it first reaches an entry (or guard) relay. This relay can view the user's IP but remains unaware of the online activities they carry out.
- Middle relays: The data proceeds to a middle relay, which is blind to both the original source and the data's end destination. It only recognizes the previous relay and the subsequent one.
- Exit relay: In the final stage, the exit relay sheds the ultimate layer of encryption, channeling the user's raw data to its intended location. It can perceive the transmitted data (unless additionally encrypted, such as with HTTPS) but remains oblivious to the original sender.
Tor offers several benefits:
- Advanced anonymity: Tor offers heightened anonymity compared to VPNs due to its unique architecture. Unlike VPNs that often require you to provide personal information, such as email, username, password, and even payment details, Tor operates on a decentralized network where you don't need to divulge any personal data to access its services.
- Access to the deep web: Tor is the gateway to .onion websites, a part of the deep web not indexed by standard search engines.
- Avoid censorship: Many oppressive regimes censor parts of the internet. Tor allows users in these countries to access blocked content.
These benefits lend them to legitimate use cases like overcoming censorship, whistleblowing platforms, anonymous research, and sensitive communications by journalists and activists. However, just like with VPNs, these tools can also be exploited for illegitimate purposes such as evading law enforcement, conducting cyberattacks, trading illegal items, and facilitating unauthorized access to restricted systems.
It's also important to note that a user's encrypted data via Tor becomes accessible at the exit node, potentially exposing it to anyone controlling that node. While the deep web may lure curious users, more cautious, privacy-minded users tend to shy away from it.
How to Use VPNs and Tor Together
Some users even go to the extreme of using VPN and Tor together to boost privacy.
You can either use VPN through Tor or use Tor through VPN. The second scenario, where you'd first connect to a VPN and then route your traffic through Tor, is the most common. This setup ensures that the Tor entry node cannot see your actual IP address, which is especially useful for hiding your Tor usage from your Internet service provider (ISP). Many consider this the safest approach for combining the capabilities of both VPNs and Tor so that neither the VPN service nor Tor exit nodes can access your data.
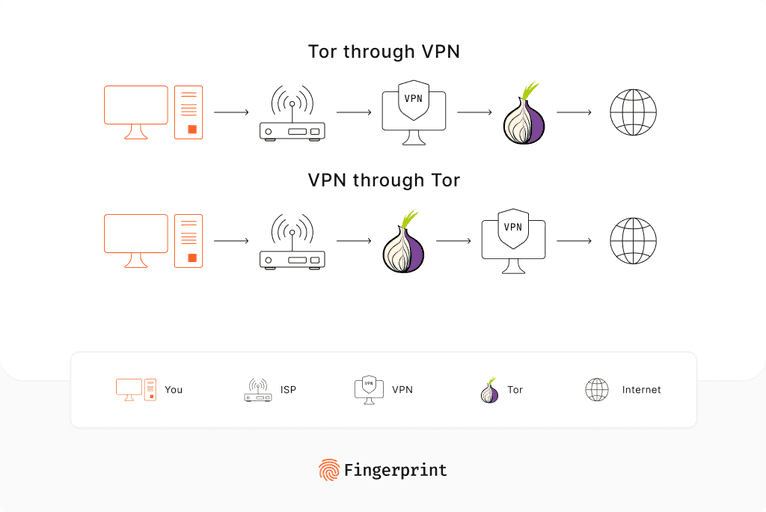
Double encryption means slower connection speeds and potential costs, though. Reliable VPNs that have .onion over VPN capabilities usually come at a price.
How Fingerprinting Identifies Bad Actors
While VPNs and Tor might hide your IP, they don't change your device's unique fingerprint. Your location might be masked, but fingerprinting solutions can still identify repeated visits from a device.
Instead of managing the risks of VPN and Tor users, fingerprinting identifies the user behind any IP address obfuscation and data encryption. Unlike cookies that store data on the user's device, fingerprinting analyzes information about the connected device—such as browser type, screen resolution, and installed fonts—to create a unique profile. Applications can then manage the risk of these profiles.
The good news for both users and developers is that fingerprinting also allows applications to accommodate people who use VPNs and Tor for legitimate reasons. Fingerprint Pro, for example, cross-references incoming IP addresses against a database of blacklisted IPs known for fraudulent activities. This feature, which is part of Fingerprint's Smart Signals security suite, offers a more nuanced approach to security that doesn't automatically flag all VPN or Tor users as suspicious.
Conclusion
VPNs and Tor are both well-known for offering online anonymity, but they use different mechanisms to cloak users' digital footprints. VPNs, with their direct encrypted pathways, offer speed and reliability, whereas Tor, with its relay-based approach, maximizes anonymity.
While VPNs and Tor lend themselves to illegitimate uses such as fraud, hacking, and cyberattacks, many people also use them for legitimate reasons, such as avoiding censorship or unwanted targeted ads.
While many sites still try to keep out bad actors by blocking all VPN or Tor users, the better option is to use a fingerprinting solution like Fingerprint Pro. It allows sites to identify and block malicious users behind all this obfuscation without affecting legitimate users of VPNs and Tor.