Summarize this article with
Fraudsters love shortcuts, and location spoofing is one of their favorites. Just ask the rideshare platform whose customers lost $40 million after over 800 fraudulent drivers used GPS spoofing apps to look as if they were in areas with surge pricing when they were not.
As more businesses rely on location for access controls, pricing, and compliance, the risks of fake location data are multiplying. If you still trust basic IP geolocation checks alone, you may as well be rolling out the red carpet for fraudsters.
Why location spoofing is a fraud headache
Location spoofing can be a full-blown threat to revenue, compliance, and trust. Fraudsters use it to bypass regional restrictions, scoop up cheaper deals, and sidestep bans or regulatory blocks. For fraud prevention teams, every missed spoofed location is a potential loss, whether that’s revenue leakage from regional pricing abuse, regulatory headaches from KYC evasion, or skewed analytics from click farm fraud.
What is location spoofing?
At its core, location spoofing is about faking where a device appears to be. Fraudsters have plenty of tricks up their sleeves:
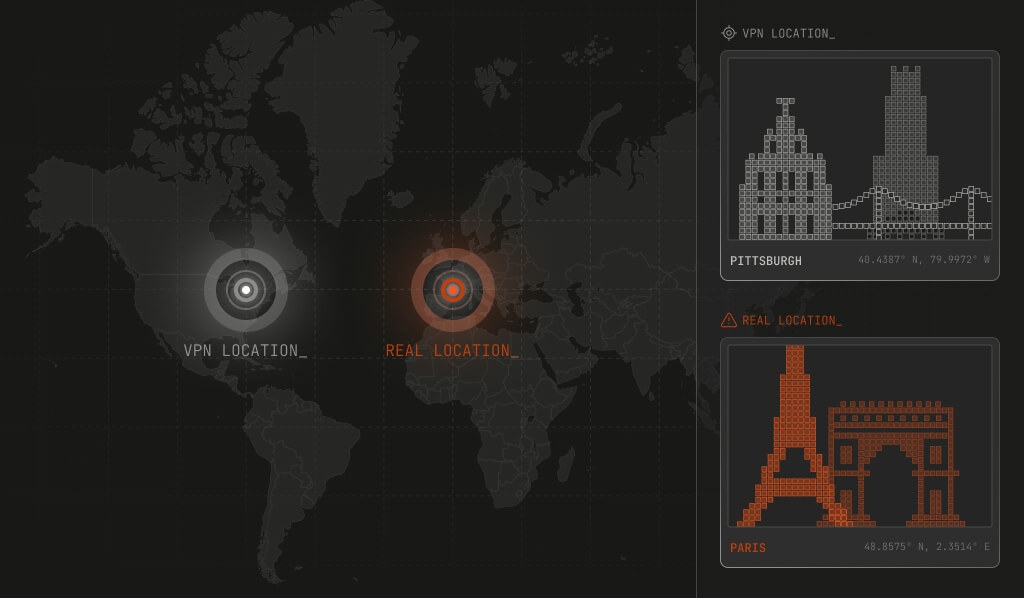
- GPS spoofing: Specialized apps or hardware feed fake GPS coordinates to a device, making it “appear” in Paris while the user is actually in Pittsburgh.
- IP geolocation spoofing: Virtual private networks (VPNs), proxy servers, and Tor networks mask a device’s real IP address, letting traffic look like it’s coming from almost anywhere.
- System-level spoofing: Tweaking device settings like timezone or language helps fraudsters build a more convincing false location.
These tactics are not just for tech wizards anymore. GPS spoofing apps with millions of downloads, easy-to-use VPNs, and emulators that can drop a device anywhere on the map have made location spoofing easily accessible.
Why fraudsters fake their location
Location spoofing is commonly used to unlock geo-restricted content like streaming services, games, and SaaS tools that are only available in certain countries. By faking their location, fraudsters gain access to features they shouldn’t be able to use. They also use spoofing to dodge bans and blocklists, especially if a platform restricts access based on region or has already flagged a user’s device.
Location spoofing also plays into regional pricing strategies. Many platforms adjust prices or run promotions based on local purchasing power. Fraudsters take advantage by posing as users from lower-cost regions, scoring discounts, or stacking free trials. In some cases, they even spoof their way into creating fake demand clusters, artificially inflating activity in a specific area to manipulate analytics or trick algorithms into thinking a product is gaining traction.
These tactics cost real money, pollute your data, and can expose your business to compliance risks.
How fraudsters pull off location spoofing
Here’s what’s in the average fraudster’s toolkit:
- VPNs and proxy servers: These mask the true IP address, making it look like the user is in a different city or even on a different continent.
- Residential proxy networks: These are harder to spot than data center proxies and can make traffic look even more “real” by hijacking legitimate users’ connections.
- GPS spoofing apps: Available on major app stores, these let users set their device’s location with a few taps.
- Emulators: Android emulators can simulate devices in any location, making them perfect for scaling up location fraud.
- System tweaks: Changing timezone, locale, or other device settings helps complete the illusion.
None of these tools requires advanced technical skills. If you can install an app or follow a YouTube tutorial, you can spoof your location. That’s why location-based fraud is such a persistent headache.
Techniques to detect fake locations
To fight back against location spoofing fraud, the key is to stop thinking in silos. Relying on a single signal like IP or GPS gives fraudsters a single point to attack. However, when you collect and analyze multiple signals like location, timezone, network details, and device behavior, inconsistencies become much harder to hide. The key is to stack signals and look for patterns that don’t line up.
Some techniques that work well:
- Compare IP and GPS locations: If the IP says Texas and the GPS says Tokyo, something doesn’t add up.
- Check timezone and locale settings: A device claiming to be in France but set to Pacific Time and English suggests location spoofing.
- Track movement for impossible travel: If a user “travels” from New York to Dubai in five minutes, they are not being honest.
- Monitor for session-level jumps: Sudden location changes mid-session are a common sign of real-time spoofing.
- Look at device fingerprint consistency: If an identified device stays the same across sessions but the location keeps changing, it is likely a spoof.
- Analyze network-level signals: Details like TLS fingerprints or network routing paths often reveal the true origin, even when the IP and GPS are masked.
The bottom line: The more signals you compare, the harder it is for fraudsters to cover their tracks.
How device intelligence sharpens location-based fraud prevention
Device intelligence takes a deeper approach by analyzing dozens of signals across the device, network, and user behavior to uncover the inconsistencies that spoofers can’t easily mask.
One of the core advantages is persistent identification. Instead of relying on unstable identifiers like IP addresses, device intelligence builds a unique, stable profile of each device. This makes it possible to recognize when the same device is pretending to be in multiple locations or suddenly changes its identity to evade detection. It also enables cross-signal analysis, comparing inputs like IP, GPS, timezone, and locale settings to detect mismatches that would go unnoticed in a single-point system.
Behavioral data adds another layer. By looking at how a device behaves over time, you can catch suspicious activity like frequent location switching, impossible travel distances, or usage patterns that don’t match human behavior. This kind of layered analysis makes it far harder for fraudsters to spoof their location without raising red flags.
How Fingerprint stops location spoofing in its tracks
Fingerprint works directly on your website or mobile app, analyzing over 100 browser, device, and network signals to generate stable, highly accurate visitor identifiers. These identifiers persist for months, even if users go incognito, clear cookies, or route through VPNs. This level of consistency makes it easy to identify devices that try to spoof their way into different regions.
In addition to device and browser recognition, Fingerprint’s Smart Signals give you a deeper look at each visitor. You’ll get advanced insights that flag VPN usage, location manipulation, and browser tampering. That context helps you block fraud attempts like location spoofing and gives you reliable, real-time data to inform user-facing decisions. Some examples of how these Smart Signals work:
- IP Geolocation: Accurately determines the physical location of the originating IP address, even when VPNs or proxies are involved, and uses multiple techniques to cut through anonymizing tools.
- VPN Detection: Flags VPN usage by analyzing connections to known VPN providers and looking for signs like mismatched time zones or system settings.
- Geolocation Spoofing Detection: Specifically detects when mobile GPS coordinates have been tampered with, so you can catch location manipulation at the source.
- Android Emulator Detection: Spots when requests come from emulators, which are often used for mass location spoofing or automated abuse.
- Replay Detection: Identifies when requests to Fingerprint’s servers have been modified, a common tactic in advanced spoofing schemes.
- Persistent visitor ID: This unique identifier sticks with a device across sessions, even if fraudsters clear cookies or change IP addresses. If the same device keeps trying to reinvent itself in new locations, you’ll see the pattern.
The power isn’t in any one signal. It’s how Fingerprint combines them to build a complete and persistent picture of every device. You know you're likely dealing with a high-risk device when VPN usage, GPS spoofing, and emulator activity show up together.
Keep fraudsters guessing with smarter detection
Fraudsters will keep finding new ways to fake their whereabouts, but you don’t have to make it easy for them. By layering persistent identification and Fingerprint’s Smart Signals, you can spot even the most sophisticated location-based fraud without interfering with your user experience.
If you want to see these Smart Signals in action, start a free trial and test location spoofing detection for yourself. Or if you want to explore how this fits into your fraud strategy, reach out to our team for a deeper dive.
Ready to solve your biggest fraud challenges?
Install our JS agent on your website to uniquely identify the browsers that visit it.
FAQ
Location spoofing is the act of faking a device's true location using VPNs, proxies, GPS manipulation, or browser-based tools.
Using advanced device intelligence and fingerprinting tools, you can spot mismatched signals (e.g., IP vs. GPS data), detect proxy/VPN use, and identify anomalies in user behavior.



