Direct communication with an executive at your organization can be an excellent opportunity to ask important questions, get visibility about your work, and learn more about your organization’s future. However, there’s a threat lurking in some digital communication from executives in the last few years. This threat is known as “whale phishing” or “CEO fraud.”
Whale phishing is a significantly deceptive type of phishing that can cause substantial damage because those targeting individuals through whale phishing intentionally create communications such as email, text messages, and even voice messages to look and sound like an employee’s CEO or other high-profile executives.
Any employee or organization with a corporate email address or system is susceptible to a whale phishing attack, sometimes called whaling.
In this article, we’ll discuss what whale phishing is, how it happens, how it differs from other phishing attacks, and some red flags to watch out for. Additionally, we’ll discuss some well-known examples of whaling attacks and how individuals and organizations can prevent whale phishing attacks from causing damage and being successful.
How Whale Phishing Works
The Whale Phishing Process
Whale phishing involves impersonating and targeting individuals who know the impersonated person, so it takes quite a bit more effort than generic phishing schemes, such as generic email phishing.
Whale phishing follows a more sophisticated process than generic phishing due to the high-profile nature of its targets. The attackers research their target, studying their communication style, interests, and professional habits. They then craft a personalized, convincing email that appears to come from a trusted source.
For example, a sample text message could look like this:
Hi (Employee Name),
I have an urgent request. Please let me know if you are free.
Thanks, (Executive Name)
Targeted emails may ask for a previous employee’s payroll information, participate in a wire transfer, or reveal sensitive information about the company or employees. It will try to look like a genuine form of communication. Its general messaging is usually an “urgent” request to transfer money to the executive through wire transfer, providing payroll information, or other financial details such as credit card information.
Let’s take a closer look at the three main types of phishing to better understand how whale phishing differs from the other types.
Whale Phishing vs. Spear Phishing vs. Phishing
Phishing
Generic phishing casts a wide net and aims to affect the most people in the quickest and most harmful ways. Phishing can take shape in a few different ways, and some of the most common methods are email phishing, text messaging, and social media.
The general idea is to be contacted either by a stranger or by someone you know whose account has been hacked with a message and a website URL that may look like a more legitimate site (think a bank or an ecommerce site) asking you to provide sensitive information such as your credit card number and details.
We’ve previously written about some of the common signs of an email phishing scam, and knowing just a few can save many headaches.
Spear Phishing
Spear phishing targets a specific set of individuals within a targeted organization or a certain set of characteristics. They’ll employ similar tactics to phishing, including fake or spoofed emails made to look legitimate. Spear phishing generally involves much research and preparation, but the consequences could be quite costly if it succeeds with a couple of the targeted individuals.
Whale Phishing
Whale phishing differs from the other two types in that while the tactics are the same, the sender is made to be impersonating an executive or other high-ranking employee at a company. This distinguishes whale phishing from generic phishing. While the latter uses a broad net to trap any unsuspecting user, the former involves a targeted approach, focusing on a specific individual with a tailored attack strategy.
The Top Red Flags of Whale Phishing
There are several red flags to look out for in whale phishing. Some of the most common ones include:
- Unknown Numbers or Emails: Whale phishing attacks send unexpected emails and text messages from unknown numbers or email domains that closely mimic legitimate ones but have subtle discrepancies.
- Poorly Written, Urgent Messages: Those messages are generally poorly written and in a voice that does not sound like the executive and requests sensitive information or financial transactions with a note that it is “urgent.”
- The CEO is contacting you: This may seem ordinary, but if you don’t regularly receive communication from your organization’s CEO or through a specific form of communication, text message, for example. You should exercise extreme caution and get confirmation that the message is legitimate. This particular type of whaling is sometimes also referred to as CEO Fraud.
Real-Life Examples of Whale Phishing
Whale phishing has become an all too common occurrence in corporate communication settings. We’ve included real-life examples from recent years of apparent whale phishing attacks below.
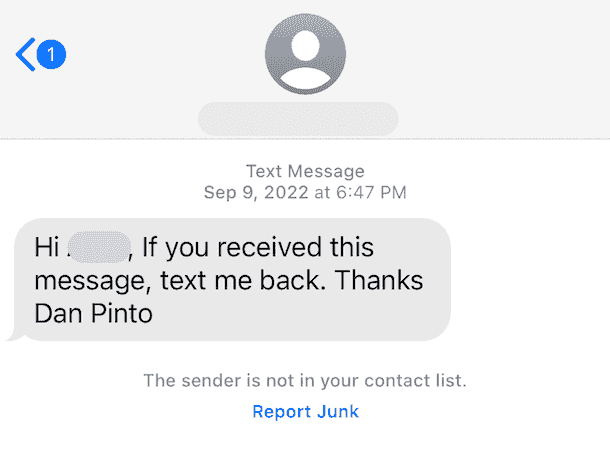
A text message example from a Fingerprint employee of a CEO fraud whale phishing attempt.
Snap
Snap suffered a data breach back in 2016 because of a whaling attack. The hackers targeted Snap’s Human Resources employees while posing as Snap CEO Evan Spiegel through email exchanges to gain access to payroll information. This is an example of whale phishing, where the ultimate goal is not monetary funds but personal and sensitive employee information.
ZScaler
CEO Fraud can be particularly damaging for an organization if it’s successful. ZScaler recently explained how hackers created an AI-generated deep fake of their CEO’s voice through publicly available digital media, such as conference appearances and media interviews. With that fake voice, the hackers targeted ZScaler employees through WhatsApp voice messages with similar messages that were once only through written messages.
This tactic is newer for phishing attacks and may see a rise in the coming years with the growing popularity and applications of artificial intelligence. We’ll discuss how to spot these attacks before they cause damage next.
How to Prevent Successful Whale Phishing Attacks
Preventing whale phishing requires vigilance from organizations and their employees alike. While it’s tough to avoid emails or text messages from being sent to employees, organizations can implement a few simple but highly effective strategies to help prevent those messages from being successful.
Increase Awareness and Offer Phishing Education
Most importantly, awareness and education are the best and most effective methods of phishing prevention. High-profile targets, such as executives and their teams, should be trained to recognize potential phishing attempts, which can be accomplished through ongoing training, usually as part of standard security training. Bringing to light the many ways companies can be targeted helps employees understand the importance of remaining vigilant.
Implement Verification and Approval Processes
There should be well-established verification processes for requests involving accessing sensitive information or initiating large financial transactions and steps that trigger extra verifications or approvals to prevent unauthorized actions. These processes should be well documented, and employees should be well-trained on them.
Additionally, with the risk of attackers gaining access to sensitive information of employees or sometimes users, having a strong and secure user identification strategy with multi-step authentication, identifying every visiting device through device intelligence, and additional checks when needed can help ensure that if unauthorized visitors are trying to access information through account takeover attacks are stopped before being able to do so.
Use Secure Email Software
Reputable email providers like Google and Microsoft can help detect and block phishing attempts. These tools can analyze emails for signs of phishing, such as suspicious attachments, URLs, and behavioral patterns. Google, for example, will alert recipients if an email is from outside the organization and to exercise caution before taking action with the email.
In conclusion, while whale phishing is a significant threat, understanding how it works and implementing awareness and prevention measures can go a long way in mitigating its potential damage.
FAQ
To help employees better detect and avoid falling for whale phishing attempts, organizations should implement comprehensive security awareness training. This training can include information about what whale phishing is, how it works, and the common signs of a phishing email.
For example, employees should be taught to look for things like poor grammar, requests for sensitive information, and email addresses that don’t match the company’s official domain. They can also be trained to use secure methods for verifying and reporting suspicious emails.
While any company can be a target of whale phishing, those with more publicly available information about their executives may be more susceptible. This is because whale phishing relies on impersonating high-ranking individuals, and the more information an attacker has, the more convincing they can be. Therefore, industries such as finance, healthcare, and technology, where executive profiles are often readily available, could potentially be at greater risk.
If an organization identifies a whale phishing attempt, it should immediately alert all employees to the threat, especially those who might be targeted. It’s also crucial to report the incident to the appropriate authorities or regulatory bodies. The organization may also need to review its security protocols to understand how the attempt was made and to strengthen defenses against future attacks.
In cases where a phishing attempt is successful, the organization should investigate to determine what information was compromised and take steps to mitigate any potential damage.