Summarize this article with
Fraud prevention teams face constant pressure. Attackers evolve rapidly, user expectations remain high, and new threats or regulations seem to appear every week. Behind the scenes, however, digital fingerprints have become one of the most effective tools for staying ahead by quietly identifying risky behavior, stopping fraud in its tracks, and allowing legitimate users to proceed seamlessly.
There are many types of digital fingerprints, each playing a unique role in fraud prevention. In this article, we'll take a closer look at how they work and why they matter.
Why digital fingerprints matter
Digital fingerprints analyze subtle details of a visitor's device, browser, and network environment to generate a unique profile. Unlike cookies or login credentials, these identifiers persist across sessions and are difficult to spoof or erase.
For fraud teams in industries like financial services, e-commerce, online gaming, SaaS, and digital marketplaces, this translates to the ability to:
- Detect returning fraudsters even if they’ve cleared cookies or changed IPs.
- Spot behavioral anomalies that indicate automation that is often used for account takeover or credential stuffing.
- Reduce friction for legitimate users with recognized fingerprints.
Not all fingerprints are created equal. Understanding the strengths of each fingerprinting method helps teams tailor defenses to their threat landscape and respond faster when something looks off.
9 types of fingerprinting for fraud prevention
1. Device fingerprinting
Device fingerprinting gathers hardware and software data like OS, time zone, screen resolution, and CPU details to generate a stable identifier for the device being used. It aims to maintain identification even when different browsers are used or when non-browser interactions are performed, such as with mobile apps.
2. Browser fingerprinting
Browser fingerprinting focuses on identifying individual browsers by looking at traits such as user agent, font list, plugins, and rendering behavior. While browser fingerprinting is limited to a single browser instance, even a collection of related browser fingerprints can put an end to various types of fraud.
3. TLS fingerprinting
TLS fingerprinting examines the parameters exchanged during the TLS handshake, like cipher suites, extensions, and supported versions, to create a unique fingerprint of the client. Techniques like JA3 and JA4 can reveal inconsistencies in bot traffic, automation tools, or spoofed clients.
4. Canvas fingerprinting
Canvas fingerprinting uses the HTML5 canvas element to draw hidden graphics and measure how the device renders them. Differences in GPU and graphics drivers create a unique, hard-to-replicate signature.
5. WebGL fingerprinting
WebGL fingerprinting builds on canvas fingerprinting by using 3D rendering via WebGL, exposing even deeper GPU-level attributes that help distinguish real devices from virtual machines or emulators.
6. Audio fingerprinting
Audio fingerprinting measures how a device plays and processes sound to produce a unique audio signature. Subtle differences in drivers and hardware add another layer of identity.
7. Behavioral fingerprinting
Behavioral fingerprinting monitors real-time user behavior — typing speed, mouse movement, scrolling patterns — to differentiate between humans and bots. Especially powerful for detecting automation or replay attacks.
8. Network fingerprinting
Network fingerprinting identifies devices based on how they interact with the network stack, analyzing attributes like TCP/IP packet structure, timing, and header values. These low-level behaviors are difficult to fake and can reveal the operating system, network configuration, or signs of emulation and spoofing.
9. Media device fingerprinting
Media device fingerprinting identifies connected peripherals like cameras and microphones, helping flag device changes or virtual environments often used in fraud attempts.
Why combining fingerprinting methods works best
Sophisticated fraudsters use virtual machines, automation frameworks, and anti-detection tools to mimic legitimate behavior. Relying on a single fingerprinting method isn’t enough.
Fingerprint’s device intelligence platform combines over 100 signals across device, browser, network, and behavioral layers to generate a stable, unique visitor ID. This ID persists even when users clear cookies, use incognito mode, or rotate IP addresses. Additionally, Fingerprint offers 20+ Smart Signals for actionable insights, such as:
- Bot Detection: Flags headless browsers and automation tools like Puppeteer or Selenium
- VPN Detection: Identifies IP obfuscation, VPN use, and location masking
- Browser Tampering Detection: Detects anti-detect browsers and custom spoofing attempts
- Developer Tools Detection: Reveals inspection or reverse-engineering behavior (such as is common in tech support scams)
These signals work together in real time to surface high-risk traffic, without requiring frustrating CAPTCHAs or adding additional friction for trusted users.
Real-world applications
Digital fingerprints are actively used to prevent:
- Account Takeover (ATO): Recognize when an unfamiliar device is trying to access an account and raise the requirements to gain access
- Payment Fraud: Detect suspicious transactions based on device and behavioral anomalies such as virtual machine or emulator use or tampering
- Bot Attacks: Differentiate real users from scripts and bots mimicking human behavior
- Multi-Accounting Abuse: Identify the original devices creating multiple fraudulent accounts to prevent promo abuse, incentive abuse, ban evasion, and more
By combining device intelligence with internal data, fraud teams can act faster and smarter, reducing manual reviews while keeping the user experience intact.
Privacy and compliance considerations
At Fingerprint, we focus on privacy-safe data collection and compliance with regulations like GDPR and CCPA. Our platform does not track users across the web or collect personally identifiable information. We provide clear documentation and guidance on how to use fingerprinting responsibly.
Conclusion
Digital fingerprinting is one of the most powerful tools in the fraud prevention toolkit. It operates invisibly to stop threats, protect revenue, and safeguard real users. When multiple fingerprinting methods are combined, the result is a holistic fingerprint that’s precise, resilient, and future-proof.
Ready to solve your biggest fraud challenges?
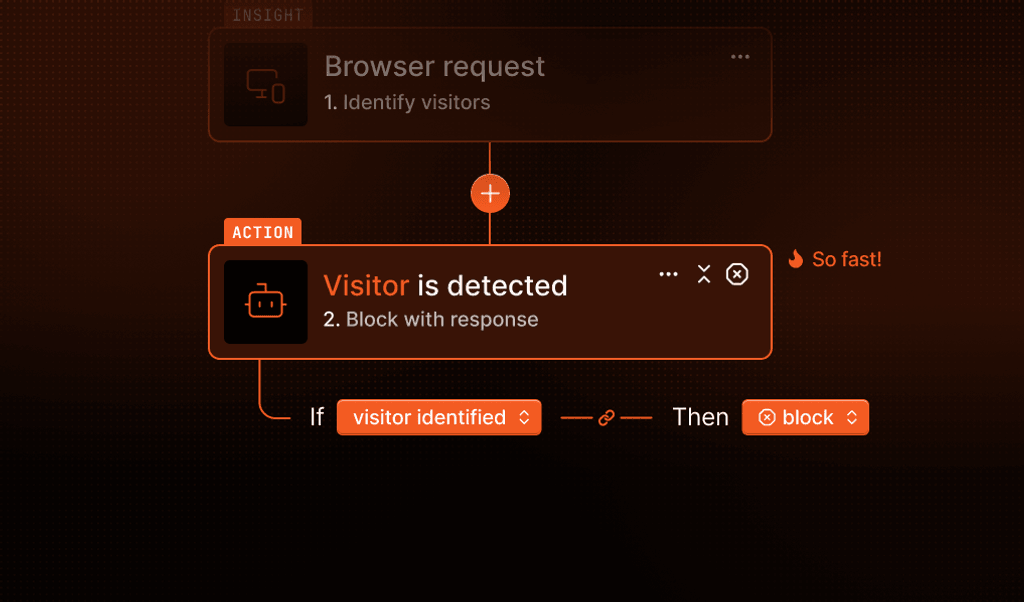
Install our JS agent on your website to uniquely identify the browsers that visit it.
FAQ
When used responsibly, particularly for cybersecurity and fraud prevention, digital fingerprinting is generally permitted under most privacy regulations.