![[Tutorial] What Is SMS Fraud? How to Detect and Prevent SMS Pumping Fraud [Tutorial] What Is SMS Fraud? How to Detect and Prevent SMS Pumping Fraud](/static/3bcefa86adfb1f403f6a5d349047275b/9e18a/blog_sms_fraud_tutorial.png)
Summarize this article with
Text messaging has become a crucial communication channel for businesses to reach customers regarding account information, updates, and content. However, as the popularity of Short Message Services (SMS) increases, so does the risk of SMS fraud. Fraudsters are finding new ways to exploit SMS to steal money or sensitive information from organizations. In the business world, this fraud usually focuses on compromising security measures like SMS-based one-time passwords (OTP) used for authentication.
In this article, we will explore the issue of SMS fraud from a business perspective. What exactly is SMS fraud, and how does it impact companies? We will cover the most common types of SMS fraud businesses must be aware of to identify risks and abnormalities in SMS use. Most importantly, we will discuss measures companies can take to detect and prevent SMS fraud.
What is SMS fraud?
SMS fraud refers to illegal activities conducted through text messaging services. This form of fraud manipulates SMS, a widely used communication channel, to achieve various nefarious objectives. The methods range from sending deceptive messages to users to orchestrating complex schemes that exploit business processes. The common goal across these methods is to gain unauthorized access to resources, steal personal information, or incur financial losses for victims.
Common types of SMS fraud
Some of the most common types of SMS fraud that businesses should be aware of include:
SMS Pumping Fraud
SMS pumping fraud involves sending massive volumes of messages, often automated, from a single device. A typical scenario is a fraudster setting up a system to incessantly send messages to premium-rate numbers they control, thereby generating substantial charges. For businesses, this can lead to inflated SMS costs and depleted resources. Fraudsters pursue this for monetary gain, exploiting the pay-per-message billing structure often used in SMS services.
Subscriber Identity Module (SIM) Swapping
In SIM swapping, fraudsters deceive telecom operators to reassign a victim's phone number to a new SIM card, usually in their control. Once successfully controlled, they can intercept text messages, including OTPs for banking and other secure services. By accessing these OTPs, they can bypass security measures and access sensitive accounts, leading to identity theft or financial fraud.
Phishing via SMS (Smishing)
While a more personal attack, smishing uses deceptive texts that mimic legitimate entities, urging recipients to reveal personal data or click on malicious links. An example is a message posing as a bank, asking users to confirm account details or view an urgent notice via a provided link. The objective here is typically identity theft or the installation of malware for further exploitation.
The impact of SMS fraud on businesses
SMS fraud has significant consequences beyond the immediate financial losses victims suffer. It is not solely about safeguarding financial assets but also about preserving the integrity of personal and corporate digital identities. Businesses and individuals face numerous risks when it comes to fraudulent SMS activities, including:
- Financial Losses: Businesses face inflated SMS costs due to SMS pumping, reimbursement expenses for affected customers, and potential fines for security breaches. For individuals, SMS fraud can lead to unauthorized charges, drained bank accounts, or stolen credit card information. These financial burdens can be substantial, affecting the bottom line of companies and the personal finances of individuals.
- Trust Erosion: Trust is a fundamental element in the relationship between businesses and customers. When customers fall victim to SMS fraud through a company's communication channels, it can erode this trust. Recovering from such reputational damage often requires significant time and resources.
- Compromised Security and Privacy: SMS fraud tactics like SIM swapping and smishing directly target the privacy and security of individuals, leading to identity theft and unauthorized access to sensitive information. For businesses, these breaches can mean exposure of customer data, violation of privacy laws, and loss of intellectual property.
- Operational Disruptions: Dealing with the aftermath of an SMS fraud attack can disrupt regular business operations. Companies must redirect resources to address security breaches, handle customer complaints, and upgrade security measures. This shift in focus can detract from a business's core operations and growth.
- Regulatory and Legal Consequences: Businesses may face legal challenges and regulatory scrutiny following an incident of SMS fraud, especially if customer data is compromised. Compliance with data protection laws means firms are obligated to safeguard customer information. Failing to do so can lead to hefty penalties.
Detecting and Preventing SMS Fraud
Understanding and mitigating SMS fraud is vital to safeguarding individuals and businesses from its harmful effects. A well-rounded approach, which includes the use of technology, increased awareness, and ongoing diligence, can significantly reduce susceptibility to such deceptive activities. Battling SMS fraud requires varied approaches using suitable tools and best practices to build a strong defense against these threats.
Some measures businesses can implement include:
SMS Message Limits
Set limits on the number of SMS messages sent to a single device within a specific timeframe to prevent SMS pumping fraud. Companies can deter fraudsters while maintaining a balance that does not impact genuine users by requiring additional verification methods when visitors exceed this limit. We will explore this further in the tutorial below.
OTP Cool Downs
Implement a cooling-off period for SMS verifications, like OTPs, using device identifiers and attributes to differentiate between new, returning, and suspicious devices. Businesses can bypass SMS verification for known users with a recent history of safe interactions identified through their consistent device identifiers. For new devices, send SMS messages as usual; for suspicious devices, add additional verification forms. This approach not only streamlines the user experience for regular users but also protects against fraudulent access attempts, all while cutting down SMS costs and the potential for SMS fraud. We will explore this further in the tutorial below.
Account Linking
Assign a unique device identifier to each visitor and monitor which devices access multiple accounts. Accessing numerous accounts from a single device is common in SMS pumping fraud or account takeover schemes. By detecting and analyzing account access patterns linked to a single device, businesses can flag suspicious activities and initiate additional security checks or block access when necessary to prevent SMS fraud.
Bot Detection
Check if humans or bots are initiating SMS requests from your service. By only allowing human-based requests within your SMS-related services, businesses can prevent using automated bots, often behind large-scale SMS fraud attempts like SMS pumping. Once a bot is detected, the system can either completely block SMS services to that visitor or impose throttling measures, significantly reducing the SMS request rate. We will explore this further in the tutorial below.
Risk Analysis
Evaluate the potential risk of visitors by analyzing device attributes, including whether they are using a virtual machine, a privacy-oriented browser like Tor, or accessing your site from a location you do not operate in. Certain attribute combinations and signals can indicate potentially malicious intent. With this risk profile, businesses can tailor their response to SMS requests, from requiring additional verification steps for high-risk profiles to allowing seamless access for low-risk visitors.
Monitoring and Analytics
Monitor and track your SMS request traffic to find patterns or unusual behavior. When anomalies are detected, like sudden spikes in SMS requests from a single device, it's a potential red flag for SMS pumping or spamming. From there, you can investigate the source, pinpointing whether it's a specific number or location, and block SMS requests from that device if deemed suspicious.
User Education
Educate users on recognizing and responding to suspicious messages, the risks of smishing, and the importance of not clicking on unknown links or sharing personal information via SMS. Regular training sessions or informational emails can keep users informed, making them a strong line of defense against SMS fraud.
Leveraging Fingerprint to combat SMS fraud
One of the top components in preventing SMS fraud is identifying the devices making the requests. Whether it's OTP messages or links to download your app, you only want to send these to legitimate users and prevent fraudsters from abusing them. Fingerprint's Device Intelligence Platform helps businesses identify devices by analyzing over 70 identification signals and accurately identifying returning visitors.
These visitor identifiers remain stable over months, allowing businesses to monitor long-term user behavior and identify unusual activity patterns. For instance, a single visitor identifier associated with multiple SMS verification requests from different numbers could indicate fraudulent activity, such as SMS pumping or account hijacking.
In addition to highly accurate visitor identifiers, Fingerprint Smart Signals provide additional information about visitor devices that can allow businesses to craft security rules and risk profiles. Real-time detection features, like browser tampering detection, bot detection, and geolocation spoofing, easily integrate into existing systems and allow for the creation of more secure authentication workflows.
Combining Fingerprint's visitor identifier with Smart Signals enables businesses to proactively protect against SMS fraud attempts, saving time and resources while providing a seamless user experience for legitimate visitors. Jumia, a leading African eCommerce platform, addressed over $40k in costs from SMS fraud by using Fingerprint to identify repeat visitors and prevent them from abusing their SMS verification system.
Tutorial: How to slow down SMS pumping with Fingerprint
Fingerprint's ability to accurately identify returning visitors allows for less reliance on SMS OTPs, streamlining the verification process for genuine users while preventing fraud. Additionally, businesses can use Fingerprint's stable visitor identifiers to count how many SMS requests come from a single device.
This tutorial will tackle a specific challenge: SMS pumping fraud. This type of fraud involves sending a high volume of OTP requests from a single device, often intending to exploit and overwhelm SMS verification systems. Let's dive into the steps to build a system to throttle SMS pumping fraud.
You can try the live final result on our website. The example uses Next.js, but the same principles apply to any web application. The code snippets in the article are simplified for readability, but you can find the full source code on GitHub.
1. Identify visitors requesting OTP codes
When a visitor attempts an action that would send an OTP, request a Fingerprint visitor identifier, transmit it to your application server, and store it along with a record of the activity. With this data, you can determine if the visitor has recently submitted an OTP request and apply logic rules for identifying and preventing SMS pumping attacks.
To begin, sign up for a Fingerprint account and install the Fingerprint JavaScript agent on your webpage. If you are using a frontend framework like React, Angular, or Vue, you can use one of our frontend libraries which have caching and other useful features built in. This setup lets you obtain the visitorId, which you can use to count the number of SMS requests from a specific browser.
// Initialize the agent.
const fpPromise = import("https://metrics.yourdomain.com/web/v3/<your-public-api-key>").then(
(FingerprintJS) =>
FingerprintJS.load({
endpoint: "https://metrics.yourdomain.com",
})
);Note: We recommend routing requests to Fingerprint CDN and API through your domain for production deployments using the endpoint parameter. This prevents disruption from ad blockers and improves accuracy. You can learn multiple ways to do this in our guide on protecting your JavaScript agent from ad blockers.
Let's use an account creation screen as an example:
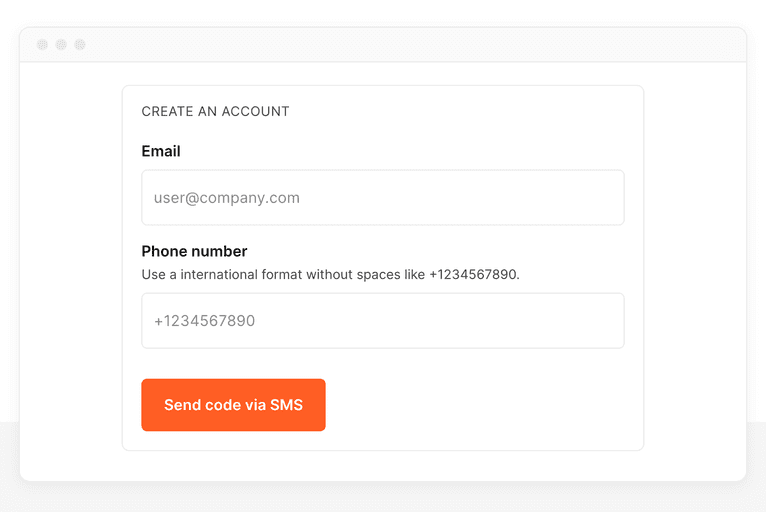
When a user requests an OTP, make a visitor identification request and send the requestId along with the SMS request details to your server.
async function sendMessage({ phoneNumber, email }) {
// Collect browser signals and request visitor identification
// from the Fingerprint API. The response contains a `requestId`.
const { requestId } = await (await fpPromise).get();
// Pass the `requestId` to your server alongside the visitor data
const response = await fetch(`/api/send-verification-sms`, {
method: 'POST',
headers: {
'Content-Type': 'application/json',
},
body: JSON.stringify({
email,
phoneNumber,
requestId,
}),
});
}2. Retrieve and validate identification results
On the server, use the requestId to get the full identification results from Fingerprint Pro Server API and validate its authenticity. If the requestId is not found or some of its data is inconsistent, return an error instead of sending the OTP code.
export default async function sendVerificationSMS(req: NextApiRequest, res: NextApiResponse) {
const { phoneNumber: phone, email, requestId, disableBotDetection } = req.body as SendSMSPayload;
// Get the full identification Fingerprint Server API and check its authenticity
const fingerprintResult = await getAndValidateFingerprintResult(requestId, req);
if (!fingerprintResult.okay) {
res.status(403).send({ severity: 'error', message: fingerprintResult.error });
return;
}
// ...
}You can call the Server API REST endpoint directly or use one of our Server SDKs.
Note: You can also use Webhooks or Sealed results (Enterprise plan only) instead of Server API to process and validate identification results in a server environment.
Here is an example using the Server API via the Node.js SDK:
import { EventResponse, FingerprintJsServerApiClient, isEventError } from '@fingerprintjs/fingerprintjs-pro-server-api';
export const getAndValidateFingerprintResult = async (
requestId: string,
request: NextApiRequest,
): Promise<{ okay: boolean; data?: EventResponse, error?: string }> => {
// The Server API must contain information about this specific identification request.
let identificationEvent: EventResponse;
try {
const client = new FingerprintJsServerApiClient({ apiKey: SERVER_API_KEY });
identificationEvent = await client.getEvent(requestId);
} catch (error) {
if (isEventError(error) && error.status === 404) {
return { okay: false, error: 'Request ID not found, potential spoofing attack.' };
}
return { okay: false, error: String(error) };
}
const identification = identificationEvent.products?.identification?.data;
// More checks below...
return { okay: true, data: identificationEvent}
}
An attacker might have acquired a valid request ID via phishing. Check the freshness of the identification request to prevent replay attacks.
// Fingerprinting event must be a maximum of 3 seconds old
if (Date.now() - Number(new Date(identification.time)) > 3000) {
return { okay: false, error: 'Old identification request, potential replay attack.' };
}Make sure the identification request comes from the same IP address as the OTP request.
// This is an example of obtaining the client's IP address.
// In most cases, it's a good idea to look for the right-most
// external IP address in the list to prevent spoofing.
if (request.headers["x-forwarded-for"].split(",")[0] !== identification.ip) {
return { okay: false, error: 'Identification IP does not match request IP, potential spoofing attack.' };
}The Fingerprint API request should always originate from a trusted production website. Check the origin in the response to ensure it is coming from your website.
const ourOrigins = ["https://yourdomain.com"];
const visitorDataOrigin = new URL(identification.url).origin;
// Confirm that the request is from a known origin.
if (
visitorDataOrigin !== request.headers["origin"] ||
!ourOrigins.includes(visitorDataOrigin) ||
!ourOrigins.includes(request.headers["origin"])
) {
return { okay: false, error: 'Visit origin does not match request origin, potential spoofing attack.' };
}Using one of many Fingerprint Smart Signals, detect if a bot initiated the OTP request. The botDetection result returned from the Server API tells you if Fingerprint detected a good bot (for example, a search engine crawler), a bad bot (an automated browser), or not a bot. If an automated bot is detected, reject the OTP request.
// Prevent bots for requesting OTP codes
if (identificationEvent.products?.botd?.data?.bot?.result === 'bad') {
return { okay: false, error: '🤖 Malicious bot detected, OTP code was not sent.' };
}3. Limit the number of OTP codes per visitor to prevent SMS pumping attacks
Having validated the authenticity of the identification event, check to see if the visitor is making too many requests within a specific timeframe. Your business logic and use case should determine the best time window and request frequency, but here is an example:
// Retrieve SMS verification requests made by the same browser today from the database, the most recent first
const smsVerificationRequests = await SmsVerificationDatabaseModel.findAll({
where: {
visitorId,
timestamp: {
[Op.gte]: midnightToday(),
},
},
order: [['timestamp', 'DESC']],
});
const requestsToday = smsVerificationRequests.length;
// If there have been too many requests, shut the visitor down for the day
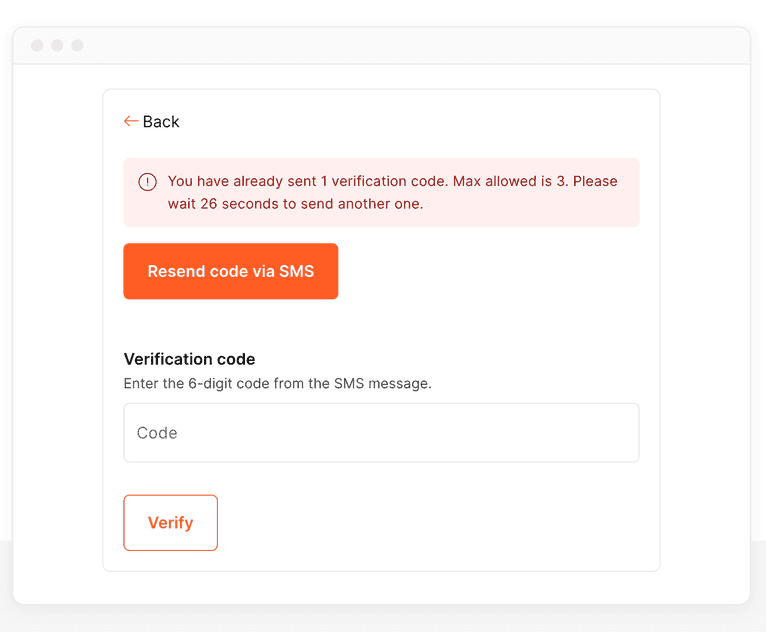
if (requestsToday >= MAX_SMS_ATTEMPTS) {
res.status(403).send({
severity: 'error',
message: `You have already received ${requestsToday} OTP codes today. Please try again tomorrow or contact our support team.`,
});
return;
}
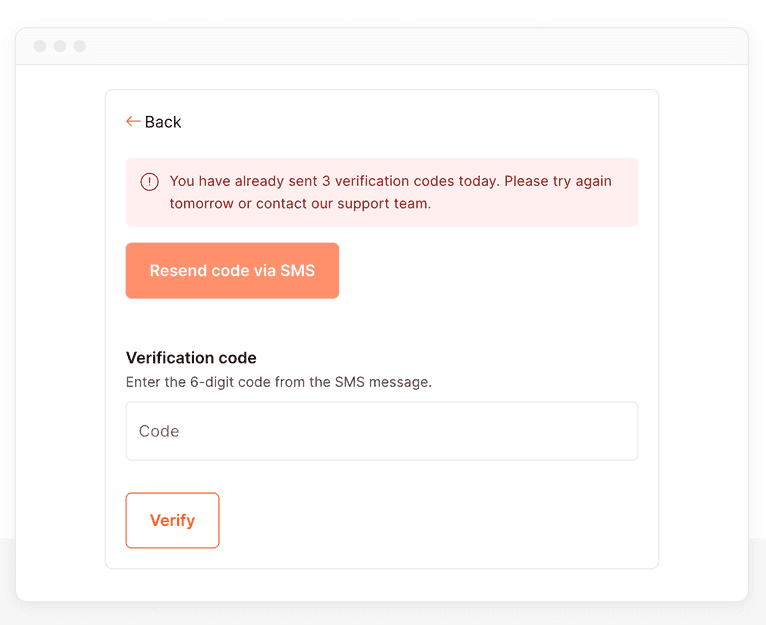
You can also apply increasingly longer cool-down periods between each OTP request.
// If the visitor has already sent some requests recently, apply the appropriate cool-down period
export const SMS_ATTEMPT_TIMEOUT_MAP = {
1: { timeout: 30 * 1000 },
2: { timeout: 60 * 1000 },
3: { timeout: 120 * 1000 },
};
if (requestsToday > 0) {
const lastRequestTimeAgoMs = new Date().getTime() - smsVerificationRequests[0].timestamp.getTime();
const timeOut = SMS_ATTEMPT_TIMEOUT_MAP[requestsToday].timeout;
if (millisecondsToSeconds(lastRequestTimeAgoMs) < millisecondsToSeconds(timeOut)) {
const waitFor = timeOut - lastRequestTimeAgoMs;
res.status(403).send({
severity: 'error',
message: `You have already received ${requestsToday} OTP codes today. Please wait ${readableMilliseconds(waitFor)} to send another one.`,
});
return;
}
}

If this is the visitor's first request, or the cool-down period has passed, send the SMS verification code and save the request to the database. The phone number is saved as a hash to preserve privacy.
const verificationCode = generateRandomSixDigitCode();
await sendSms(
phone,
`Your verification code for demo.fingerprint.com/sms-pumping is ${verificationCode}.`,
visitorId,
);
await SmsVerificationDatabaseModel.create({
visitorId: visitorId,
phoneNumberHash: hashString(phone),
email,
timestamp: new Date(),
code: verificationCode,
});
res.status(200).send({
severity: 'success',
message: `We sent a verification SMS message to ${phone}.`,
});
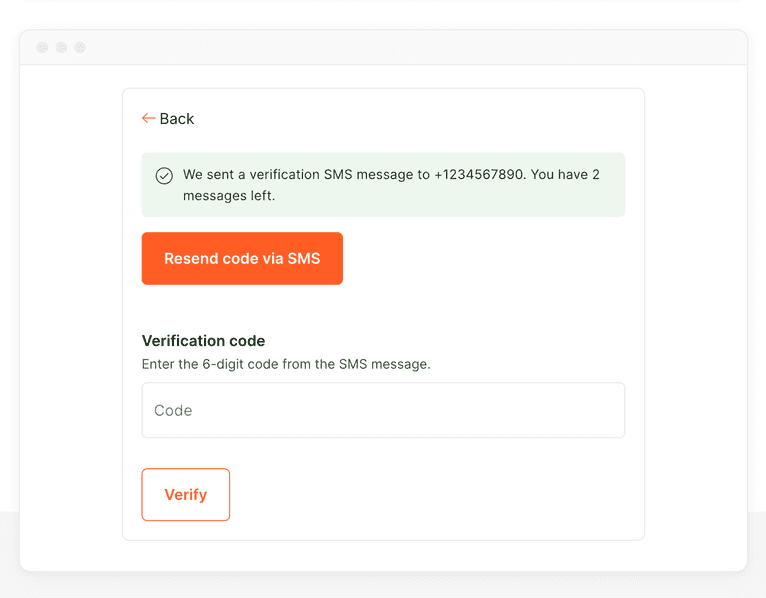
Explore Our SMS Fraud Prevention Demo
Visit the SMS Fraud Prevention Demo we built to demonstrate the concepts above. You can explore the open-source code on Github or run it in your browser with CodeSandbox. The core of the use case is implemented in this component and this endpoint.
Conclusion
As we've seen, Fingerprint's unique visitor identification and device intelligence platform provide additional data, allowing businesses to build robust security protocols. Fingerprint enables companies to make informed decisions about user verification and fraud prevention by accurately identifying returning visitors and offering real-time insights into user behavior.
If you want to enhance the security of your SMS verification process and reduce the risk of SMS fraud, we encourage you to sign up for a free trial to experience it firsthand. Our team can also provide tailored solutions to meet your security needs and help you fortify your services against SMS fraud.
FAQ
One example could be that fraudsters might send messages claiming to be from a bank or other reputable organization, asking for personal information or directing the recipient to a phishing website.
In other cases, they might send a text message stating that the recipient has won a prize, but needs to pay a fee to claim it.
If an individual or business becomes a victim of SMS fraud, they should report it to their mobile carrier and local law enforcement authorities. They can also file a complaint with the Federal Trade Commission in the United States. Businesses might also want to notify their customers, especially if the fraudulent messages appear to come from their organization.
There are indeed laws in place to protect consumers and businesses from SMS fraud. In the United States, for example, the Telephone Consumer Protection Act regulates all forms of telemarketing, including text message spam. Violations of this act can result in hefty fines. Additionally, many countries have data protection and privacy laws that offer some level of protection against SMS fraud.
SMS pumping fraud involves sending a large volume of unsolicited messages through a network, often to exploit billing inefficiencies or to engage in spam or phishing activities.
Businesses can set SMS message limits, link accounts to unique device identifiers, and use bot detection strategies to mitigate fraudulent activities, ensuring effective use of OTPs for verification.