Summarize this article with
Even the most sophisticated fraud prevention systems struggle when visibility breaks down. As anonymization technologies evolve, identifying who’s behind a transaction, or where they’re coming from, has become increasingly complex.
Virtual private networks (VPNs) are a key part of that challenge. Once limited to enterprise security use cases, VPNs now account for a growing share of everyday traffic. In Fingerprint’s 2024 Device Intelligence Report, 15.3% of observed sessions originated from a VPN connection, up nearly 40% from the previous year. Meanwhile, the global VPN market is projected to reach $116 billion by 2030, underscoring how ubiquitous encrypted and location-masked traffic has become.
For senior risk, fraud, and engineering leaders, this shift introduces blind spots in account verification, geolocation, and transaction risk modeling. That’s why VPN detection has emerged as a critical component of enterprise fraud prevention, providing the context needed to tell legitimate privacy from potential fraud or misuse.
In this article, we’ll explore the best VPN detection tools for fraud prevention in 2025, covering their capabilities, strengths, and considerations for selecting the right solution for your organization. But before comparing tools, it’s worth understanding the challenges VPNs create for modern fraud teams.
The challenges faced by fraud teams
As online anonymity becomes easier to achieve, the signals that fraud and risk teams once relied on, such as IP, location, and device identity, are now among the least trustworthy. VPNs and other privacy tools have reshaped how users connect, erasing geographic boundaries and, with them, much of the visibility needed to separate legitimate behavior from high-risk activity.
Anonymized network traffic
VPNs and proxies now account for a significant portion of online activity, concealing true user locations and disrupting IP-based controls. Alongside these tools, The Onion Router (Tor) introduces an additional challenge, routing traffic through a decentralized network of relays that hides both identity and geographic origin. While Tor is widely used for privacy and security, it’s also exploited by fraudsters to obscure activity, automate attacks, and simulate diverse user locations.
For fraud teams, this means reduced confidence in device correlation, geolocation, and behavioral baselines — critical factors in any fraud prevention program.
Rising false positives
Not every VPN session represents fraud. Remote employees, global customers, and privacy-conscious users all generate anonymized signals that may appear suspicious. Without deeper context, teams risk overcorrecting, introducing unnecessary friction, triggering false positives, and straining review capacity.
Multi-layer fraud tactics
VPNs are rarely used in isolation. Fraudsters often combine them with bots, emulators, and synthetic identities to mask intent and mimic legitimate user behavior. VPN detection often serves as the first signal of such multi-layered attacks, helping teams surface suspicious clusters before they escalate.
Compliance and geographic risk
For industries that operate under strict regulatory frameworks, such as fintech, iGaming, and crypto, accurate geolocation is essential. VPNs obscure that data, creating compliance exposure when transactions originate from prohibited or high-risk jurisdictions. One misstep can result in substantial penalties or even license revocation.
Gaps in legacy detection systems
Static IP reputation lists and proxy blocklists can’t keep pace with the dynamic nature of modern VPN services. Residential and mobile VPNs frequently rotate IPs, making traditional methods ineffective. Teams need adaptive detection that goes beyond IPs to analyze behavioral, network, and device-level signals in real time.
Fraudster use cases: VPNs as a tool for exploitation
Beyond masking user identity, VPNs are often used to carry out fraud schemes that directly affect revenue and compliance. Two common examples, regional pricing fraud and jurisdiction evasion, illustrate the broader challenge.
- Regional pricing fraud: Fraudsters spoof their location to exploit regional price differences, purchasing goods or subscriptions at lower rates intended for other markets. This undermines revenue models across sectors like SaaS, travel, and digital goods, often without triggering conventional risk alerts.
- Jurisdiction evasion: In regulated industries, VPNs are used to bypass geographic restrictions and conduct transactions from banned regions. This not only increases fraud exposure but can also result in severe regulatory penalties when unapproved activity goes undetected.
Together, these challenges highlight why VPN detection has become a core capability in modern fraud prevention. The following section examines leading VPN detection solutions that help teams recover lost visibility, improve model accuracy, and detect risk without compromising user trust.
Best VPN detection tools for fraud prevention
The market for VPN detection technology has evolved rapidly, reflecting the growing need for visibility into anonymized network traffic. The following tools represent some of the leading solutions available in 2025, each offering a distinct approach to identifying VPNs, proxies, and high-risk connections that can undermine fraud prevention systems.
1. Fingerprint
Fingerprint is best for enterprises and platforms that need privacy-compliant, context-rich VPN detection as part of a holistic fraud intelligence strategy.
Fingerprint offers VPN detection as part of its Smart Signals device intelligence suite, alongside other key signals such as IP blocklist matching and browser bot detection. Together, these tools help fraud and risk teams spot suspicious activity before it impacts security or revenue.
Smart Signals integrates with Fingerprint’s device intelligence platform, which analyzes over 100 browser, device, and network signals to generate a stable, persistent VisitorID. This layered approach provides deeper context around user intent, enabling teams to differentiate between legitimate privacy use and potential fraud or misuse while minimizing false positives.
Strengths:
- Industry-leading accuracy and persistent visitor identification
- Real-time anonymized connection detection (VPNs, proxies, and bots)
- SOC 2 Type II, GDPR, and CCPA compliant
- Integrates seamlessly with other Smart Signals for contextual risk analysis
Pricing: Free tier available; Pro Plus plan starts at $99/month for 20,000 API calls, with custom enterprise pricing available.
2. IPQualityScore
IPQuality Score is best for organizations seeking scalable IP intelligence to evaluate anonymized connections within larger fraud and risk management systems.
IPQualityScore (IPQS) provides a Proxy & VPN Detection API that identifies connections associated with VPNs, proxies, and Tor networks in real time. The service analyzes IP reputation, connection type, and network attributes to help organizations evaluate anonymized traffic and assess potential fraud risk.
Strengths:
- Real-time detection of VPNs, proxies, and Tor exit nodes
- Risk scoring to support adaptive fraud decisioning
- Continuously updated global IP intelligence database
Pricing: Free tier with 1,000 lookups/month; paid plans start around $499 per month, with enterprise options available.
3. Spur
Spur is best for organizations in regulated or security-sensitive industries that require deep IP intelligence for fraud prevention, compliance monitoring, or threat investigation.
Spur offers enterprise-grade IP intelligence for detecting VPNs, proxies, and automated/obfuscated traffic via real-time API calls or on-prem datasets. The platform enriches each IP with geolocation, autonomous system (ASN), proxy/VPN status, and other network-reputation attributes to deliver actionable risk context for fraud and security teams.
Strengths:
- High-accuracy detection of VPNs, residential proxies, and anonymized traffic
- Real-time IP enrichment for fraud, compliance, and network defense use cases
- Enterprise-ready datasets and APIs with flexible deployment models
Pricing: Free UI tier with up to 5,000 monthly lookups; API plans start at $99/month, with Enterprise API options from $40K/year.
4. MaxMind
MaxMind is best for enterprises that require established IP-intelligence capabilities for fraud detection, geolocation verification, or risk management.
MaxMind’s GeoIP2 Anonymous IP database and associated web services help detect users connecting via VPNs, Tor, public proxies, or hosting/data-center IPs. They classify anonymizer types, such as data center, hosting provider, or known VPN endpoint, and provide detailed metadata, including ISP, ASN, and anonymizer confidence ratings.
Strengths:
- Mature, globally-recognized IP datasets and anonymizer classifications
- Broad coverage for IPv4 & IPv6, with daily updates and strong data quality
- API and database access models that support fraud, geolocation, and risk workflows
Pricing: Web service queries start at $0.005 per query, with database subscriptions and commercial licenses available on request.
5. Greip.io
Greip.io is best for mid-to-high volume digital platforms that need a cost-effective, scalable solution for anonymized traffic detection integrated into fraud and risk workflows.
Greip offers a VPN/Proxy Detection API designed to identify connections from VPNs, proxies, and TOR networks in real time, helping organizations mitigate risks tied to masked IPs and suspicious network behavior.
Strengths:
- Detects anonymizing infrastructure like VPNs and proxies with a REST API interface
- Supports multiple fraud-oriented use cases (fraud detection, fake accounts, SMS fraud)
- Developer-friendly interface and scalable implementation options
Pricing: Free tier with 2,000 requests/month; paid tiers starting at US $29/month for 170,000 requests/month and US $89/month for 400,000 requests/month; pay-as-you-go enterprise pricing available.
6. IPGeolocation.io
IPGeolocation.io is best for companies that need transparent anonymized-traffic insight and IP threat intelligence integrated into their fraud or risk systems.
IPGeolocation.io offers a Threat Detection/Security API that identifies VPNs, proxies, Tor exit nodes, bots, and cloud-provider IPs in real time, enabling fraud, risk, and threat teams to assess anonymized traffic with a calculated threat score. The API also returns detailed metadata, including connection type, ASN, ISP, proxy type, and provider, enabling smarter risk decisions across fraud prevention workflows.
Strengths:
- Real-time detection of anonymizing infrastructure (VPNs, proxies, Tor) with metadata and threat scoring
- Broad IP-intelligence dataset covering IPv4 and IPv6, including connection type and cloud provider attribution
- Developer-friendly API with global coverage and usage tiers suited for fraud teams
Pricing: Plans start at US $99/month for 150K requests (Security tier); higher-volume and enterprise plans available.
7. Fraudlogix
Fraudlogix is best for organizations in advertising, affiliate marketing, e-commerce, or other high-velocity environments that need fast detection of anonymized traffic to maintain traffic integrity and reduce fraud risk.
Fraudlogix offers a real-time VPN & proxy detection API that identifies connections routed through VPNs, proxies, or Tor exit nodes, a key input for fraud, traffic-quality, and ad-tech risk workflows. The service uses layered signals, including IP reputation, network metadata, and behavioral patterns, to classify anonymized traffic.
Strengths:
- Real-time detection of anonymizing infrastructure (VPNs, proxies, Tor) via API
- Multi-signal analysis combining IP history, network behavior, and anonymizer status
- Developer-friendly integration with risk, fraud, and traffic-quality platforms
Pricing: Free lookup tool available; API and enterprise pricing available on request.
8. IPinfo
IPinfo is best for risk teams needing scalable IP intelligence and anonymizer detection to enrich existing fraud models or threat workflows.
IPinfo’s Privacy Detection API flags IPs associated with VPNs, proxies, and hosting providers. It also provides IP reputation scoring, autonomous system data, and hosting classifications, allowing fraud systems to assess risk dynamically.
Strengths:
- Real-time detection of VPNs, proxies, Tor, and hosting IPs with detailed metadata
- Developer-friendly API with global coverage and high uptime
- Rich threat and privacy data for integration into risk or fraud workflows
Pricing: Plans start at $49/month for the Core tier, with enterprise and high-volume plans available.
9. IP2Location (IP2Proxy)
IP2Location is best for enterprises and risk teams that prefer direct database integration and control over IP intelligence for fraud prevention, compliance, or security monitoring.
IP2Location’s IP2Proxy™ Database identifies VPNs, web proxies, Tor exit nodes, data-center ranges, and hosting provider IPs. It’s available as both a downloadable database and a web-service API, offering flexible deployment for batch analysis or real-time detection.
Strengths:
- Large, frequently updated database with multiple packages for proxy/VPN detection
- Supports both on-premise database licenses and API/web-service access
- Detailed metadata, including proxy type, last seen date, provider, ASN, and usage type
Pricing: Database packages start at $399/year for standard licenses; premium proxy-detection database packages begin at $1,199/year; site licenses start at $7,980/year or more.
10. ProxyDetect
ProxyDetect is best for platforms handling high-frequency transactions, rapid account creation, or streaming/payment flows where real-time anonymization detection is critical.
ProxyDetect focuses on real-time detection of VPN, data-center, and residential proxy traffic. Built for horizontal scalability and optimized for platforms that process large volumes of concurrent connections.
Strengths:
- Scalable detection of VPNs and proxies optimized for high-traffic sites
- Designed for horizontal scale, capable of supporting large web and transaction volumes with low latency
- Works even with JavaScript disabled, enabling broader deployment contexts
Pricing: Free tier available (up to 1,000 daily API requests for startup use); enterprise licensing available on request.
Disclaimer: This article is based on publicly available information from official company websites and reputable third-party sources as of the time of writing. Product features, pricing models, and capabilities may change over time. Readers should verify details directly with each vendor before making business decisions
How to choose a VPN detection solution
Selecting the right VPN detection tool is about more than identifying anonymized traffic. For fraud and risk leaders, it’s about finding a solution that integrates seamlessly with existing models, minimizes false positives, and maintains compliance without slowing operations. The right platform should enhance your existing fraud strategy by restoring visibility into who’s connecting, how, and why.
Accuracy and coverage
VPN detection accuracy depends on the breadth of signals a tool can analyze. IP reputation databases alone are no longer sufficient. Look for platforms that combine IP intelligence with network, device, and behavioral signals to detect both known and emerging VPN endpoints. Tools that process data from multiple sources, including hosting-provider IP ranges, Transport Layer Security (TLS) fingerprints, and traffic patterns, deliver far higher confidence scores than those that rely solely on static lists.
Context, not just classification
A connection identified as a VPN isn’t automatically fraudulent. The most effective tools go beyond binary classification to provide contextual insight, showing whether a VPN is residential, corporate, or data-center-based, and correlating that with user history or device identity. This level of context allows fraud teams to build nuanced rules that balance security with user experience.
Integration with your fraud stack
Enterprise fraud prevention relies on layered intelligence. VPN detection should feed into existing systems (e.g., device intelligence, behavioral analytics, and machine learning models), rather than operate in isolation. Solutions with flexible APIs, exportable risk scores, and real-time webhooks ensure teams can act on VPN insights without rebuilding their workflows.
Adaptability and machine learning
Static databases quickly become outdated as VPN providers rotate IPs and launch new endpoints. Modern detection tools use adaptive learning models that automatically incorporate new intelligence from recent activity patterns. This ensures detection systems stay current without requiring constant manual updates.
Privacy and compliance
Because VPN detection inherently involves analyzing user connections, compliance matters. The best vendors are SOC 2 Type II, GDPR, and CCPA compliant, using anonymized data collection methods that don’t infringe on user privacy. Enterprise buyers should verify each vendor’s approach to data processing and regional data storage.
Operational fit and scalability
Finally, consider how a solution scales with your traffic volume, response-time requirements, and review workflows. Some tools excel in high-frequency environments (e.g., e-commerce or ad-tech); others are designed for lower-latency use cases (e.g., banking or account verification). Choosing a platform that aligns with your infrastructure will minimize latency while maximizing detection fidelity.
Restoring visibility in the age of anonymization
VPNs are now part of the fabric of online traffic, used daily for privacy, security, and, at times, deception. For fraud and risk teams, the challenge isn’t simply identifying these connections but understanding their intent. The most effective detection tools give teams the insight needed to distinguish legitimate privacy behaviors from hidden threats.
As anonymization grows, so does the need for precision. The next generation of fraud prevention depends on layered intelligence that correlates network signals with device and behavioral data to restore visibility that VPNs obscure. That’s where Fingerprint helps organizations gain the clarity they need to make confident, data-driven decisions.
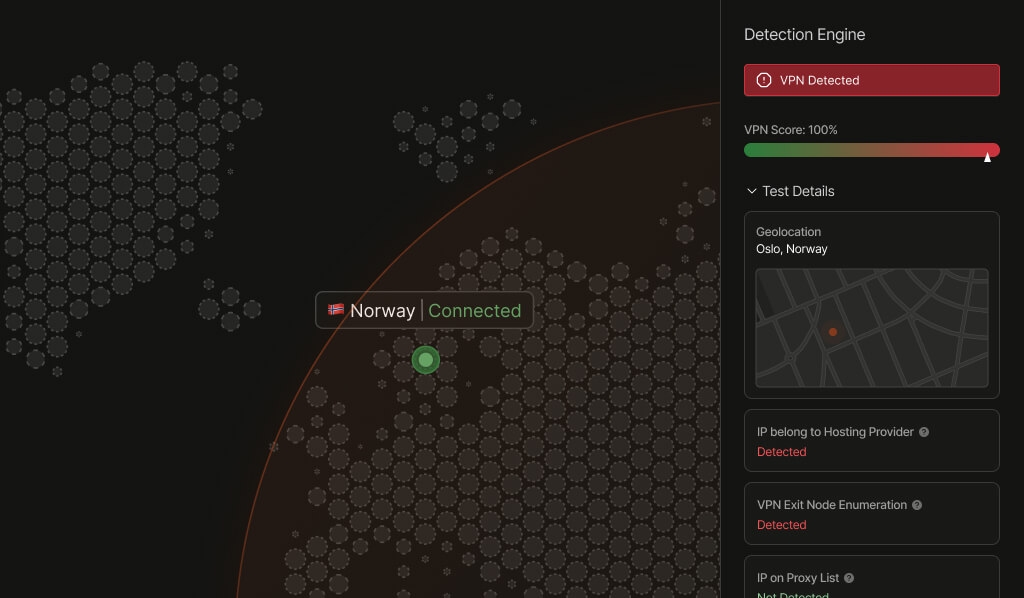
Fingerprint’s VPN Detection Smart Signal identifies anonymized connections in real time, correlating them with over 100 browser, device, and network attributes to uncover hidden risk without penalizing legitimate users. Combined with its persistent VisitorID and privacy-compliant architecture, it equips fraud teams to act decisively and responsibly in a complex threat landscape.
Ready to close the visibility gap in your fraud prevention strategy?
Learn how Fingerprint’s device intelligence platform can help you identify VPN use, reduce false positives, and make every decision count. Start your free trial or connect with our team to learn more.
Ready to solve your biggest fraud challenges?
Install our JS agent on your website to uniquely identify the browsers that visit it.
FAQ
Yes, but only if they’re implemented without context. Modern VPN detection should inform fraud models, not dictate them. The goal isn’t to block all anonymized traffic but to evaluate it alongside other signals such as device consistency, behavioral patterns, and session history. A well-designed system flags potentially risky sessions for deeper analysis or adaptive friction (e.g., step-up verification) while allowing legitimate users to continue seamlessly.
Yes, when implemented responsibly. Compliance depends on how data is collected, processed, and stored, not the detection itself. Vendors that adhere to frameworks such as SOC 2 Type II, GDPR, and CCPA ensure user data is anonymized, encrypted, and handled in accordance with privacy regulations.