Summarize this article with
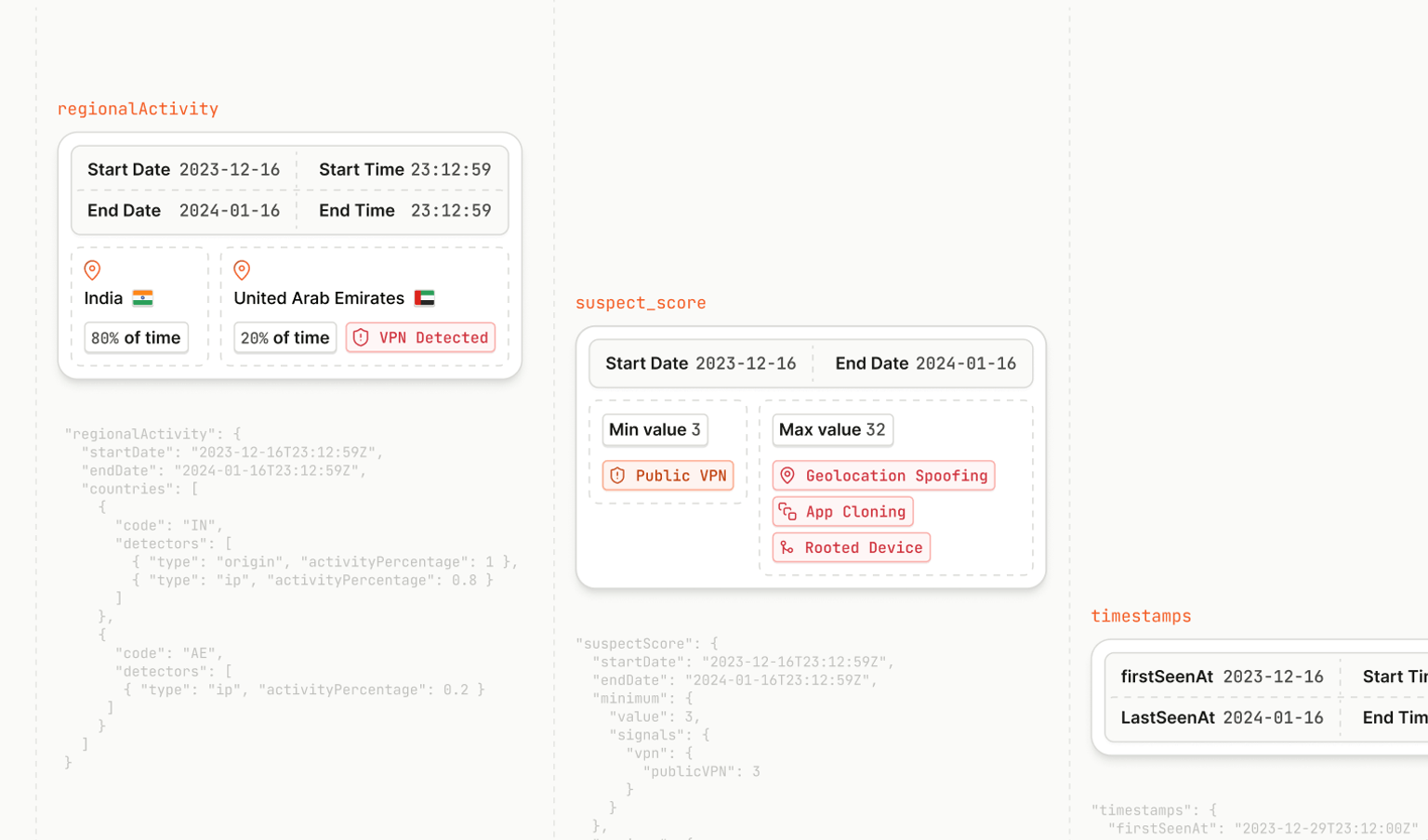
IP geolocation maps a user’s IP address to a physical location, making it easier to catch red flags like impossible travel, mismatched billing addresses, or repeated logins from high-risk regions. When combined with other signals, it becomes a powerful way to detect and stop fraud before it causes damage. Here’s how it works and how to use it effectively.
What is IP geolocation, and why does it matter?
IP geolocation is a method of determining the geographic location of a visiting device by detecting its IP address. Each device connected to the internet is assigned an IP (Internet Protocol) address. This unique identifier works back to its source, providing an approximate location of the device.
Location data helps you answer critical questions:
- Is this login plausible?
- Does it fit the user’s usual patterns?
- Are we seeing a spike in activity from high-risk countries?
While it doesn’t provide an exact address, the information is typically accurate enough to identify a user’s city or region. IP geolocation is generally used with other user identification methods, such as browser fingerprinting or device fingerprinting.
How IP geolocation works
IP geolocation matches an IP address to a physical location using databases that monitor which IP ranges belong to which internet service providers (ISPs) and regions. When someone connects to your site, their device’s IP address is sent with every request. Geolocation APIs look up this IP and return details like country, region, city, and sometimes, latitude and longitude.
Accuracy varies depending on the connection:
- Mobile networks: Often accurate within 5-10 kilometers, but can be thrown off if traffic is routed through distant servers.
- Residential broadband: Usually accurate to the city level.
- Corporate networks: Sometimes show the company’s headquarters instead of the user’s actual location.
- Public Wi-Fi: Reflects the location of the business or institution providing the Wi-Fi.
Geolocation APIs won’t give you a user’s exact street address, but they’re accurate enough to spot most suspicious patterns, especially when combined with other signals.
Key fraud detection use cases for IP geolocation
Impossible travel
Impossible travel detection is a classic. If a user logs in from New York and then appears in London 30 minutes later, you know something’s off. By calculating the time and distance between logins, you can spot “teleporting” accounts that are behaving suspiciously.
Account takeover detection
Fraudsters trying to hijack accounts often use devices or locations the real user has never touched. If a user who always logs in from Seattle suddenly tries to access their account from Eastern Europe, that’s a strong indicator of account takeover. Comparing current and historical login locations helps you flag or challenge suspicious attempts before damage is done.
Regional policy enforcement and high-risk country filtering
Some businesses need to enforce regional restrictions — think online gambling, fintech, or SaaS platforms with export controls. IP geolocation lets you identify visitors from high-risk countries or restricted regions and take appropriate action, like adjusting risk scores, triggering additional verification, or blocking access altogether. Blanket country bans aren’t foolproof and can frustrate legitimate users, but location data is essential for enforcing policy.
Payment fraud detection
For e-commerce and fintech, mismatches between a user’s billing address, shipping address, and IP geolocation can signal fraud. If someone claims to be in California but their IP traces to another country, that’s worth a closer look. Legitimate scenarios like business travel exist, so this should inform risk scoring instead of triggering automatic blocks.
How fraudsters disguise location: VPNs, proxies, and Tor
Fraudsters know all about geolocation checks. They use virtual private networks (VPNs), proxies, and Tor exit nodes to disguise their real locations. These tools can make activity appear to come from anywhere, making plain IP geolocation less reliable on its own.
VPNs route internet traffic through remote servers, masking the user’s actual IP address and location. Proxies act as intermediaries, hiding the original IP. Tor bounces traffic through multiple relays, with the final “exit node” masking the user’s real location. If your fraud prevention relies only on raw IP data, you’re always a step behind.
Spotting location evasion with advanced signals
This is where device intelligence platforms like Fingerprint come in. Instead of just looking at the IP address, Fingerprint uses more than 100 data points from each visitor’s browser and device to build a much richer profile. This includes over 20 Smart Signals designed to see through evasion tactics.
VPN Detection
Fingerprint’s VPN Detection Smart Signal identifies VPN usage by analyzing a combination of indicators. It looks for mismatches between the device’s reported timezone and its IP geolocation, checks the IP address against known VPN provider ranges, detects network signatures commonly associated with VPNs, and flags inconsistencies between the operating system and expected configurations.
Proxy and Tor detection
Fingerprint’s IP Blocklist Smart Signal identifies requests from known proxy providers and Tor exit nodes. By referencing up-to-date blocklists and analyzing network behavior, it flags connections associated with anonymization tools and previous attacks.
Geolocation spoofing
Some fraudsters use apps or browser extensions to spoof their device’s reported location. Fingerprint’s Geolocation Spoofing Detection Smart Signal spots when a device’s reported location doesn’t match its true geolocation, alerting you to possible tampering.
Other signals
Smart Signals like Browser Tampering Detection and Incognito Detection uncover when visitors are using anti-detect browsers or private browsing modes, which are often combined with VPNs and proxies.
By layering these signals, you get a much clearer picture of the intent behind each request.
Building robust fraud risk scoring with device intelligence
Raw geolocation data is useful, but it’s only one piece of the puzzle. The real power comes from combining IP geolocation with device intelligence to build a robust fraud risk scoring system.
Visitor ID
Fingerprint generates a unique visitor ID for every browser or device visiting your site. This identifier stays stable even if cookies are cleared or IP addresses change, making it much harder for fraudsters to evade detection by simply switching networks.
Behavioral patterns and velocity checks
Device intelligence lets you spot patterns like rapid logins from multiple locations, repeated failed attempts, or sudden changes in device or browser configuration. Fingerprint Velocity Signals, for example, can detect when a single device is associated with many IP addresses or countries in a short period — classic signs of automated attacks or location evasion.
Weighted risk scoring
Assign different weights to factors like VPN detection, impossible travel, and new device usage to calculate a dynamic risk score for each action. This lets you tailor your response so you can step up authentication for medium risk, block high-risk activity, and let trusted users breeze through.
Combining these signals means fewer false positives, less friction for good users, and much tougher hurdles for fraudsters.
Best practices for implementing IP geolocation
Ready to plug IP geolocation into your fraud stack? Keep these tips in mind:
- Choose a reliable IP geolocation API: Look for high uptime, frequent updates, and strong coverage of both IPv4 and IPv6 addresses.
- Understand accuracy limitations: Don’t expect street-level precision. Build your risk scoring to tolerate reasonable location variance, especially for mobile and corporate users.
- Handle false positives: Legitimate users travel, use VPNs for privacy, or connect from shared networks. Make sure your system allows for secondary verification and user appeals.
- Stay privacy compliant: Be transparent in your privacy policy about collecting location data. Follow data retention best practices, and give users control where possible.
Measuring the impact of geolocation-powered fraud prevention
How do you know if your geolocation defenses are working? Track these key metrics:
- Fraud rates: Are account takeover and payment fraud attempts dropping after implementing geolocation checks?
- False positive rates: Are legitimate users being blocked or challenged more often? Monitor complaints and support tickets to spot friction.
- Challenge conversion rates: How many users pass additional verification after being flagged for location anomalies?
- User experience: Are trusted users able to log in and transact without unnecessary hurdles?
- Attack patterns: Are fraudsters shifting tactics, such as using more sophisticated VPNs or proxies? Adjust rules and signals as needed.
Regularly reviewing these metrics helps you fine-tune your system and demonstrate ROI.
Real-world implementation: Geolocation and device intelligence in action
Here’s how you might implement IP geolocation fraud detection using Fingerprint’s Smart Signals:
Client-side identification:
const fpPromise = import("https://fpjscdn.net/v3/YOUR_PUBLIC_API_KEY")
.then(FingerprintJS => FingerprintJS.load());
async function checkTransactionRisk(transactionData) {
const fp = await fpPromise;
const result = await fp.get();
const riskAssessment = await fetch('/api/assess-risk', {
method: 'POST',
headers: { 'Content-Type': 'application/json' },
body: JSON.stringify({
requestId: result.requestId,
transaction: transactionData
})
});
return riskAssessment.json();
}
Server-side risk assessment:
const { FingerprintJsServerApiClient, Region } = require('@fingerprintjs/fingerprintjs-pro-server-api');
async function assessTransactionRisk(requestId, transactionData) {
const client = new FingerprintJsServerApiClient({
region: Region.Global,
apiKey: process.env.FINGERPRINT_SECRET_KEY
});
const eventData = await client.getEvent(requestId);
const location = eventData.products.ipInfo.data.v4.geolocation;
const vpnData = eventData.products.vpn.data;
let riskScore = 0;
if (isHighRiskCountry(location.country.code)) {
riskScore += 30;
}
if (vpnData.result) {
riskScore += vpnData.confidence === 'high' ? 50 : 25;
}
return {
riskScore,
location: location,
vpnDetected: vpnData.result,
recommendedAction: riskScore > 70 ? 'block' : riskScore > 40 ? 'challenge' : 'allow'
};
}
Ready to strengthen your fraud defenses?
IP geolocation is a solid foundation for fraud detection, but it’s even more effective when combined with device intelligence. By layering Smart Signals like VPN Detection, Proxy Detection, and Geolocation Spoofing with behavioral analysis, you can outsmart even the most determined fraudsters without making life harder for legitimate users.
Curious to see how this works in practice? Try Fingerprint’s demo environment to explore real-world signals in action. If you want to discuss how to integrate device intelligence and geolocation into your fraud prevention stack, you can contact our team or start experimenting with a free trial.
Ready to solve your biggest fraud challenges?
Install our JS agent on your website to uniquely identify the browsers that visit it.
FAQ
IP geolocation is often used as a supplementary security measure to enhance other practices like two-factor authentication. While two-factor authentication strengthens security by requiring additional user verification, IP geolocation adds another layer by verifying the user’s location.
If a login attempt is made from an unexpected location, it could be flagged as suspicious. However, the specific ways in which IP geolocation interacts with two-factor authentication can vary depending on the systems and protocols in place.
The use of IP geolocation does raise certain privacy concerns. By nature, it involves tracking the geographical location of users, which could potentially be used for intrusive purposes. However, it’s important to note that IP geolocation typically only provides approximate locations and is not usually accurate enough to pinpoint an exact address.
Furthermore, responsible companies using IP geolocation should follow best practices for data protection, including anonymizing data and obtaining user consent where necessary.
Yes, sophisticated fraudsters may attempt to bypass or manipulate IP geolocation, often through the use of VPNs or proxies that can mask or alter the apparent location of an IP address.
However, many IP geolocation services have measures in place to detect such attempts. For example, they may maintain databases of known proxy servers or use advanced algorithms to identify patterns consistent with VPN use. Despite these challenges, IP geolocation remains a valuable tool in the fight against online fraud.