Summarize this article with
Fraudsters love a good disguise. Tor (The Onion Router) is a common tool of choice for fraudsters who want to make themselves invisible and sidestep detection, causing headaches for anyone trying to keep them out. Tor has legitimate privacy uses, but it’s also a magnet for account fraud, payment abuse, and automated attacks. If your platform deals with payments, user data, or anything valuable, ignoring Tor traffic is like leaving your doors unlocked and hoping nobody notices.
Let’s break down how Tor works, why it’s a challenge for fraud prevention, and how you can actually spot and respond to Tor traffic without locking out privacy-minded users who just want to browse in peace.
Why Tor detection belongs in your fraud toolkit
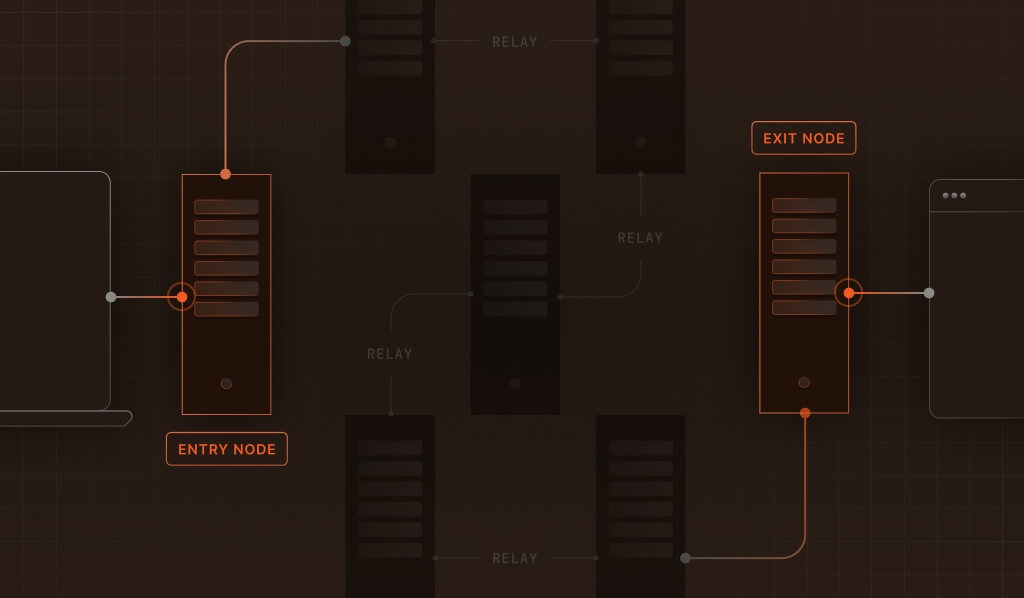
The Tor network routes internet traffic through a chain of encrypted relays. The last relay, called the “exit node,” is what your servers see as the visitor’s IP address. This setup makes it nearly impossible to trace a request back to its true origin. That’s great for whistleblowers, but also for fraudsters who want to cover their tracks.
How fraudsters use Tor to hide
Fraudsters exploit Tor to:
- Evade IP-based blocking: Block one exit node, and they just pop up from another.
- Spoof location: Appear to be logging in from random places worldwide.
- Dodge identification: Pair Tor with browser tweaks to make device identification a nightmare.
- Automate attacks: Launch bot campaigns without exposing their real infrastructure.
Which can be used to execute all kinds of attacks on your infrastructure, such as:
- Account fraud: Dozens of fake accounts, all from “different” places, all controlled by one person behind Tor.
- Web scraping: Scrapers rotate through Tor exit nodes, dodging your rate limits and bans.
- Multi-accounting: Exploiting promotions or voting systems by pretending to be many different users.
- Payment fraud: Testing stolen credit cards or laundering funds, while hiding behind anonymous IPs.
If you value trust and security, you can’t afford to ignore Tor traffic.
Why detecting Tor isn’t as simple as flipping a switch
Tor detection is tricky for a few reasons:
Exit nodes constantly change
Tor’s list of exit nodes is a moving target. New ones pop up, old ones disappear, and attackers can even run their own. Static blocklists go stale fast, and you’ll always be playing catch-up if you rely only on them.
Encrypted, obfuscated traffic
Tor wraps traffic in layers of encryption. All you see is a request from an exit node’s IP with no idea where it really started or who’s behind it.
Not everyone on Tor is a fraudster
Some people just want privacy. Blocking all Tor traffic can frustrate legitimate users, and fraudsters will still find ways around your blocks.
How to detect Tor traffic
No single method catches everything. The best approach is a layered one that combines multiple signals and methods.
Match against known Tor exit node IPs
The obvious move: check incoming requests against a list of known Tor exit nodes. The Tor Project publishes these, and commercial services keep them updated. This catches low-effort abuse. However, exit nodes are constantly changing, and private or new nodes may not appear immediately. Furthermore, determined attackers have the capability to operate their own exit nodes.
Watch for DNS and traffic timing oddities
Tor’s multi-hop routing causes odd delays in DNS resolution and inconsistent latency. If a user’s connection bounces all over the map — latency doesn’t match their supposed location, for example — you might be looking at Tor.
Analyze TLS and connection metadata
While Tor encrypts content, the connection metadata can give it away. TLS handshakes, HTTP headers, and other details sometimes reveal patterns unique to Tor Browser or relay nodes.
Behavioral and velocity analysis
Tor users frequently switch IP addresses rapidly, exhibit nonsensical geographic distribution, and trigger velocity alerts, such as a single device signing up from a dozen countries within an hour. Behavioral analysis is instrumental in detecting these patterns.
Cross-reference device intelligence
This is where device intelligence platforms like Fingerprint shine. Fingerprint uses 100+ signals to generate a unique visitor ID for each device. Even if a fraudster swaps Tor exit nodes every few minutes, their device fingerprint often stays the same. By tying activity back to a persistent identifier, you can spot the same device behind a parade of different IPs.
Combine IP intelligence with environmental signals
Layering IP reputation with environmental data — like timezone mismatches or OS inconsistencies — helps catch fraudsters who try to blend in. For example, if someone claims to be in Berlin but their device clock is set to Bangkok, something’s off.
Use anomaly detection for new or unknown relays
Machine learning models can flag traffic that behaves like Tor, even if the IP isn’t on any list yet. Unusual routing, connection timing, or network signatures can all raise red flags.
Correlate Tor traffic with automation
Tor is often used with bots. If you see headless browsers, rapid-fire requests, or other bot-like patterns coming from Tor exit nodes, you’re probably dealing with automated abuse.
How Fingerprint detects and flags Tor traffic
Fingerprint assigns each visitor a stable visitor ID, even if they change IP addresses, clear cookies, or jump between Tor circuits. This lets you spot the same device behind different Tor nodes and catch abuse that would otherwise slip through. Fingerprint also provides over 20 Smart Signals, including:
- Bot Detection: Flags bots, automated browsers, and scripts.
- Tor Exit Node Detection: Detects if the IP address is a known Tor exit node.
- Privacy Browser Detection: Flags browsers actively fighting fingerprinting and exposing user settings that can randomize and obfuscate signal output.
- VPN Detection: Identifies VPN use, which is often combined with Tor.
- Browser Tampering Detection: Spots anti-detect browsers and manual configuration changes.
- High-Activity Device and Velocity Signals: Detects high activity from a single device, as well as if IP addresses or countries change rapidly.
Additionally, with Suspect Score, Fingerprint aggregates Tor usage, VPN detection, bot activity, and more into a single risk value. No need for binary “block or allow” decisions. You are in full control and can tailor your response to different threat levels. All of these work in the background with no extra friction for legitimate users.
How to respond to Tor traffic without alienating good users
Not every Tor user is a fraudster, so it’s important to handle Tor traffic thoughtfully rather than overreacting. In some situations, blocking Tor outright is warranted, such as when you’re processing high-value financial transactions, operating in a heavily regulated industry, or facing an active attack coming through the Tor network.
In other cases, it’s better to flag and monitor instead of blocking. This applies if your user base includes privacy-conscious communities, if privacy tools are commonly used among your audience, or if your goal is to remain accessible while still watching for signs of abuse.
You can also enhance your fraud scoring by treating Tor usage as one signal among many. Weigh it alongside other risk indicators, adjust scores based on user behavior and context, and trigger extra verification when the overall risk is elevated.
Whenever possible, try to preserve privacy. Allow Tor access for low-risk actions, be transparent about your privacy practices, and offer alternative paths for verification so legitimate users aren’t shut out unfairly.
Detect Tor traffic with Fingerprint
Tor and other anonymity networks aren’t automatically bad, but they do make life easier for fraudsters. Relying on static blocklists or single-point solutions is a losing game. The smarter approach is a layered defense: combine real-time IP intelligence, persistent device identification, and behavioral analysis.
Fingerprint’s device intelligence platform helps you spot Tor traffic and other anonymization tricks before they become problems. By combining real-time IP analysis, stable visitor IDs, and 20+ Smart Signals, you can respond to abuse while keeping things smooth for legitimate privacy-first users.
Ready to stop playing whack-a-mole with Tor exit nodes? See how Fingerprint can help you get ahead of anonymized abuse. You can try it out for yourself with a free trial or talk to our team about how to integrate advanced Tor detection into your platform.
Ready to solve your biggest fraud challenges?
Install our JS agent on your website to uniquely identify the browsers that visit it.