Summarize this article with
Password sharing can be a full-blown revenue leak and a security risk for SaaS companies, streaming services, and subscription platforms. What used to be the digital version of sneaking into a movie with your friend’s ticket has ballooned into a problem that muddles your analytics, drains your revenue, and makes account security a nightmare. The real challenge? Stopping password sharing without treating every user like a would-be criminal.
Let’s examine why password sharing is a problem worth solving, how to recognize it, and, most importantly, how to prevent it without ruining your user experience.
Why password sharing is a bigger problem than you think
Revenue loss: The obvious (and painful) cost
When one paying customer becomes the access point for a handful of freeloaders, you’re just giving away your product. Streaming services and SaaS platforms lose millions every year to shared accounts. For SaaS, a single team license can get stretched to cover an entire department. For streaming, “family plans” morph into “everyone I met at college” plans.
Security and support: More users, more headaches
The more people who know an account password, the more likely it is to end up on a sticky note, in a group chat, or on a breach list. Shared credentials mean more password reset requests, more account lockouts, and more support tickets from confused users who can’t access “their” account. It’s a support team’s worst nightmare and a security team’s open invitation for account takeover attacks.
Analytics: Turning data into noise
When four people share an account, your user data becomes meaningless. You can’t tell if your new feature is a hit or if just one account is being used by four different people in four different time zones. Personalization fails, product decisions become guesswork, and your analytics dashboard turns into a carnival mirror.
How to spot password sharing
You can’t fix what you can’t see. Here’s how password sharing usually shows up:
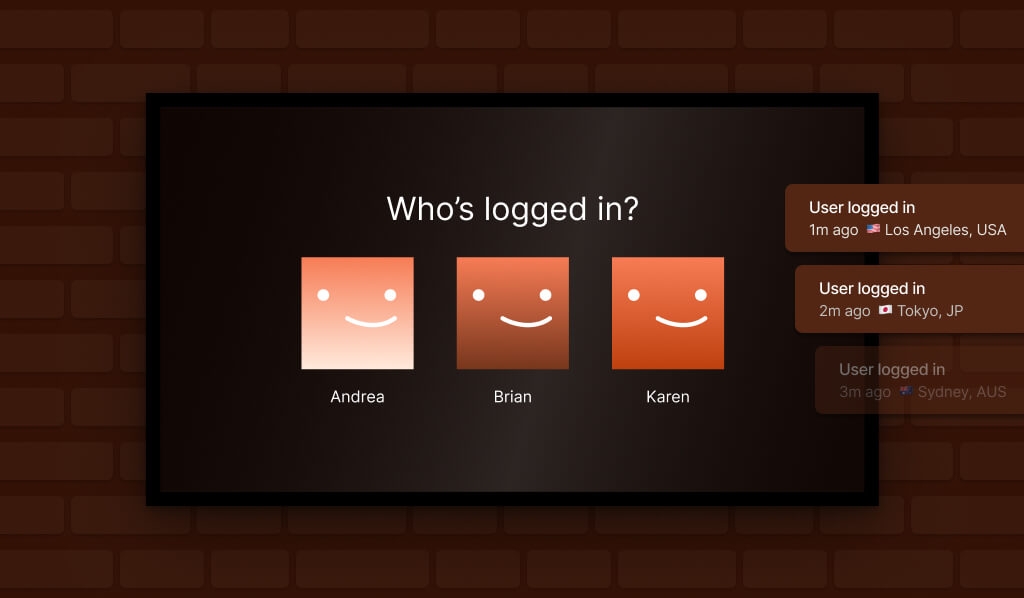
Logins from geographically distant locations
If an account logs in from Los Angeles and then, 30 minutes later, from Tokyo, you’re not dealing with a frequent flyer. That’s classic account sharing, unless someone’s cracked teleportation.
Frequent device or browser switching
Most users stick to a handful of devices: phone, laptop, maybe a tablet. When you see an account bouncing between a parade of devices and browsers in rapid succession, the odds of it being account sharing go up.
Overlapping sessions from different places
If the same account is streaming a movie in Miami and shopping for an item in Berlin at the same time, something’s off. Multiple active sessions from different locations or device types are a big red flag.
Spotting these patterns is the first step to stopping account sharing before it spirals.
Five proven strategies to prevent password sharing
Ready for something more effective than angry emails? Here are five strategies that actually work and don’t punish your real users.
1. Device intelligence for unique device recognition
Device intelligence creates persistent identifiers for every device accessing your platform. Unlike cookies, which can be easily manipulated, device fingerprints remain stable across sessions, even if users clear cookies or use incognito mode. By recognizing which devices regularly access an account, you can spot when new, unfamiliar devices show up or when an account is accessed from too many different devices in a short time.
2. IP intelligence and geolocation analysis
Monitoring IP addresses and their locations helps you catch “impossible travel” scenarios. If someone logs in from New York at 9 a.m. and then from Florida at noon, that’s suspicious. Modern IP intelligence also spots virtual private network (VPN) usage, proxy servers, and data center IPs, making it harder for illegitimate users to hide behind basic tricks.
3. Login velocity monitoring
Velocity monitoring tracks how quickly and how often accounts are accessed from different locations, devices, or IP addresses. High-velocity activity, like logins from five cities in an hour, rarely happens with legitimate use. By watching for these spikes across different time frames (minutes, hours, days), you can spot both casual sharing and more organized abuse.
4. Limiting concurrent sessions
Most individual users don’t need more than a few active sessions at once. By setting reasonable concurrent session limits, you catch obvious sharing without punishing legitimate users. If someone tries to exceed the limit, you can log out the oldest session or prompt them to choose which session to keep.
5. Step-up authentication on suspicious behavior
Don’t go full “access denied” at the first sign of weirdness. Instead, introduce step-up authentication — extra verification like an email or SMS code — when you detect risky behavior. Logins from new devices, distant locations, or after a burst of activity are all good candidates for an extra security check. This approach keeps legitimate users moving while making life harder for account sharers.
Measuring success
You’ll know your password sharing prevention is working when you start to see a reduction in concurrent sessions per account. Fewer simultaneous logins typically indicate that users are no longer sharing credentials. You should also see an increase in subscriptions to multi-user plans, a sign that people are opting for legitimate access instead of sharing a single account.
A decrease in support tickets is another possible signal. Shared accounts often cause confusion, especially around password resets and access issues, so fewer tickets suggest cleaner ownership. Finally, improved user engagement metrics will reflect higher data quality. When accounts aren’t shared, behavioral data is more accurate, leading to better personalization and smarter product decisions.
UX and policy tactics that actually work
Clear, simple terms of service
Spell out what counts as acceptable account use. Use plain language and concrete examples. If you offer a family plan, make it clear who counts as “family.” If team accounts are only for employees, say so. Don’t make users need a law degree to figure it out.
Tiered pricing for multi-user access
Offer legitimate multi-user options at reasonable prices. Family plans, team accounts, and guest access give users a way to share accounts legally. If users have affordable options, they’re less likely to share passwords under the table.
Gentle nudging toward upgrades
Instead of blocking suspected sharing outright, prompt users with a message like, “Looks like you’re signed in from multiple places. Interested in upgrading to a multi-user plan?” Treat sharing as a conversion opportunity, not just a security threat.
How Fingerprint helps stop password sharing
Fingerprint is a device intelligence platform that uses more than 100 signals to create a highly accurate visitor ID for every browser or device accessing your site. This visitor ID persists even when users clear cookies, use VPNs, or switch to incognito mode, so you get a stable foundation for detecting suspicious account activity.
But Fingerprint doesn’t just identify devices. Its 20+ Smart Signals give you real-time, actionable insights into risky behavior. For example, Velocity Signals show when a device is suddenly associated with a flurry of different IP addresses, countries, or accounts in a short period. VPN Detection flags when someone is trying to hide their real location, and IP Geolocation helps you spot impossible travel and location mismatches.
With these signals, you can automate responses like step-up authentication, session limits, or nudges to upgrade to a proper multi-user plan.
Time to take password sharing seriously
Password sharing isn’t going away, but it doesn’t have to be an unsolvable problem. By combining device intelligence, smart session controls, and thoughtful UX, you can reclaim lost revenue and keep your users’ experience smooth and secure.
Start by evaluating your current controls. Are you still relying on basic IP checks or outdated session limits? Modern solutions like Fingerprint provide persistent identification and real-time risk signals, so you can finally get ahead of account sharing without frustrating your legitimate users.
If you want to see what’s really happening with your accounts, try out Fingerprint with a free trial or connect with our team to discuss how device intelligence can protect your business at scale. Your users get a better, more personalized experience, and you get a healthier bottom line.
Ready to solve your biggest fraud challenges?
Install our JS agent on your website to uniquely identify the browsers that visit it.