Summarize this article with
For just $150 per month, a person can buy a subscription to Atlantis AIO, an AI-powered fraud-as-a-service tool for sale on the dark web. It allows the subscriber to quickly test millions of stolen username and password combinations on more than 140 online services, including banks, email, food delivery, streaming, and social media. It’s part of a practice called credential stuffing, and it makes use of the fact that people often use the same password for accounts across many different services. Nor is it that hard for fraudsters to obtain those stolen credentials—email login combinations obtained through data breaches can go for as little as five cents each.
When the tool finds a combination that works, you get an account takeover attack (ATO). This is when a fraudster gains unauthorized access to someone else’s account and uses it to steal money or data, install malware, or launch phishing attacks, for example.
It’s a major issue that is growing worse every year as AI-powered tools make ATO attacks easier to attempt and scale, even with little hacking knowledge. According to Abnormal Security's 2024 State of Cloud Account Takeover Attacks report, 83% of businesses suffered account takeover attacks in the year prior. Per Javelin Strategy & Research, account takeover attacks cost consumers $13 billion in 2023. And unfortunately, ATO is just one type of digital fraud among many.
So what should businesses do? How can you fight back against the tidal wave of AI-powered cybercrime?
The answer involves looking past the digital identity itself to the device that is using it. Unlike that digital identity, there are certain characteristics of a desktop computer or smartphone and the software they run that are extremely hard to change. When this device-specific data tells conflicting stories, you can spot fraudsters that were previously invisible.
That device data can’t just be found easily, however. There’s an art and a science to how it’s procured and analyzed, and it’s called device intelligence.
What is device intelligence?
When humans talk face to face, the words are only a small piece of the information that’s transmitted during the exchange. Facial expression, body language, vocal inflection, style of dress, hand gestures, touch, and physical location are all signals that give clues about how to interpret a conversation. But you won’t notice unless you’re paying attention.
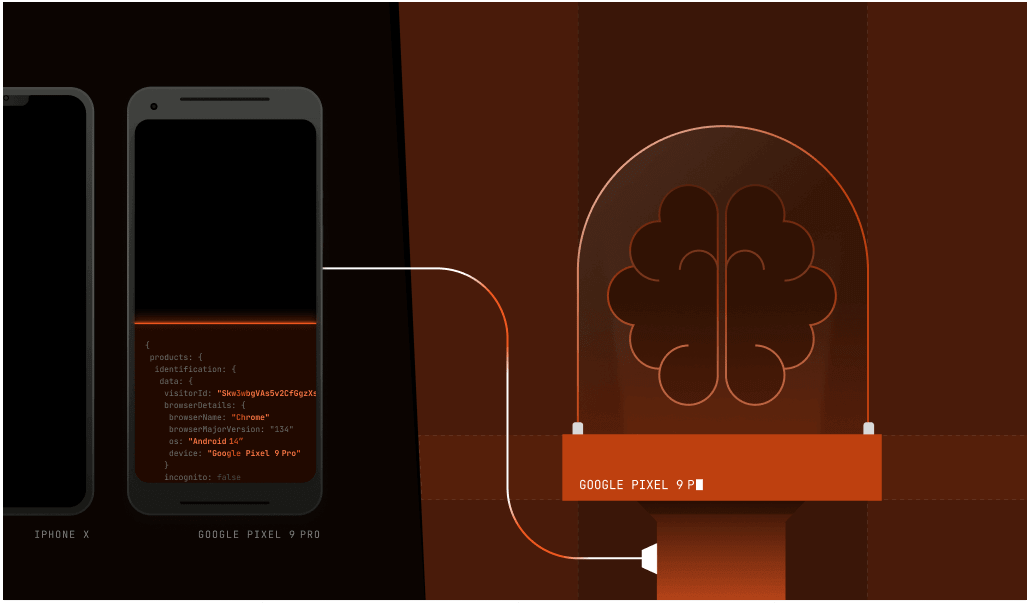
Something similar can happen behind the scenes when your web browser or mobile device talks to the server that hosts the website you want to visit. There’s the part you see, which includes the data the website sends so your browser can display it on the page. But the browser and website sometimes trade data you don’t see. Device intelligence comes from software and hardware configuration data and attributes that the website asks the browser and network to pass along in the background.
You have to ask the browser for this information; it won’t just volunteer. This data, called signals, can be compiled and analyzed to provide a unique profile of the device or browser doing the requesting. Those signals include characteristics such as:
- Browser type, e.g., Safari, Chrome, Firefox
- Operating system, e.g., iOS, Android, Windows, Linux
- IP address
- Keyboard layout
- Installed fonts
- Screen resolution
- VPN or incognito mode usage
There’s also more complex information, like how your browser carries out TLS encryption, processes audio, or renders graphics.
Fundamentally, a good signal must meet two criteria:
- Consistency: The signal should remain consistent over time for the same device, allowing it to be recognized reliably across sessions.
- Variability: The signal should differ enough across a large pool of devices to help distinguish one from another when combined with other data points.
Individually, no one signal is enough. But here’s where device intelligence comes in: when you collate that data (which can include over 100 signals per device), you can start to tell one anonymous device from another, even among billions of them.
Not only that, but you can analyze data from those billions of devices to find patterns. Such patterns provide clues about which devices are being used for good or for ill. In a world where cloud computing, open-source fraud tools, and jailbroken LLMs like GhostGPT have made it easier than ever for bad actors to operate, it’s become tough to fight back without these clues.
What device intelligence is not
Although the term “device intelligence” sounds like it might appear in a Tom Clancy thriller, it’s not spyware. It doesn’t tell you anything about the files, messages, photos, search history, or personal information on a device. It doesn’t give you someone’s email, phone number, or address.
Rather, device intelligence is recognizing the combination of generic signals coming from one device to differentiate it from any other. A system like Fingerprint doesn’t know or care who you are or who anyone else is, but can tell a device apart from billions of others. To cement user privacy, some device signals that Fingerprint collects, such as IP address, can also be hashed to add another layer of anonymization.
Why does device intelligence exist?
Techniques like browser fingerprinting and device fingerprinting evolved in the late 2000s as browsers began exposing more device-specific information through new APIs, enabling the collection of subtle signals that could uniquely identify a device.
These identification techniques gained prominence due to two trends. First, cookies—small text files stored on your device to help a website remember you—began to fall out of use as privacy concerns led browser makers to give people ways to block or erase them.
The growing availability of tools like private browsing modes also made cookies easier to avoid, rendering them less useful for identifying fraudsters. These problems made it clear that any solution to replace cookies couldn’t use data stored on a device, because you could delete that information or block it from being stored in the first place. So researchers began looking for differentiable pieces of data coming from the device itself.
Second, browser APIs became more complex, particularly after HTML5 came out in 2008. HTML5 created many sophisticated new ways for websites to interact with browsers, which in turn called on more resources from the underlying hardware running the browser. To carry out these complex functions, such as rendering 3D graphics or synthesizing sounds, websites had to gather more information about device features, such as GPU, speakers, camera, or graphics card. Each of these bits of information offers a new potential way to tell one device from another. To borrow a metaphor from biology, one tiny signal is just a single gene, but together they can create a unique strand of DNA.
Counterintuitively, this means that as the Internet has gotten more complex and much bigger, instead of making it harder to identify individual devices, in some ways it has made it easier.
On top of that, because these signals derive from client-server JavaScript interactions that take place on 99% of websites, they create a unique identifier that is stable for months or even years. In other words, it’s almost always possible to gather the kind of data needed to distinguish individual devices.
Device intelligence is a more durable technique than other types of identification that rely on a single source. For instance, the widespread use of VPNs and proxy networks lets attackers cycle through fresh IP addresses, making pure IP recognition far less effective. With device intelligence, on the other hand, an IP address is just one variable among hundreds used for identification. You can still anonymously identify devices, even when they’re using a masked IP address.
What is device intelligence used for?
When you can recognize a particular device as unique, you can do two important things:
- See a device’s behavior when it visits your website. This allows you to do things like detect when a single device is trying to log into multiple accounts, or detect when someone is trying out numerous credit card numbers to see if they work (a practice called card cracking).
- Use device signals that help detect when a user may not be who or where they say they are, such as when VPNs are used or browsers have been tampered with, to make a judgment about how you want that user to interact with your site.
Those two fundamental capabilities allow you to do many things. A non-exhaustive list of things device intelligence can help you prevent:
- Account takeovers
- Multi-accounting fraud
- Regional pricing fraud
- Account-sharing fraud
- Return policy fraud
- Coupon and promo abuse
- SMS pumping schemes
- Brute force attacks
- Bot attacks
- Location-spoofing fraud
On the flip side, you can also use device intelligence to recognize good customers and make their user experience easier. Security steps like multi-factor authentication aren’t necessary every single time for trusted returning customers.
How is device intelligence consistent?
All this sounds nice in theory. But what happens when one or more of the signals coming from a device changes, like a browser update or a switch to incognito mode? Can you still tell one device apart from others? The answer is often yes, but it depends on how you balance the signals.
If you throw every signal available into the mix, you get the highest certainty possible about the uniqueness of the device. But a single change eliminates that certainty, and you would lose track of the device. If you use fewer, more immutable signals (like operating system or device type), it’s easier to keep track over time. The trade-off is that fewer signals means it’s more likely one device will match another device with the same signal combination, reducing uniqueness.
This is where the art comes in. Good device intelligence isn’t just about adding more signals. Device intelligence platforms like Fingerprint balances those signals so the identifier assigned to each device will persist over time but be resilient if some of the signals change.
Interested in learning more about how Fingerprint can help you stop fraud? Sign up for a free trial or contact us today for a personalized demo.