Businesses want to be sure that their website users are who they say they are. While it may not be realistic to capture the identity of every single website visitor, there are other ways to learn more about your users while assessing the likelihood of risk.
With a highly accurate identifier, it’s much easier for developers to triage suspicious traffic and restrict access to users attempting to hack into accounts, make fraudulent purchases, or spam your website. The key to identifying those most likely to commit fraud is either by past activity or by associating specific use patterns with a higher likelihood of fraudulence.
In addition to addressing security and fraud prevention, such monitoring tools can also help website owners and administrators localize and tailor their website content to deliver enhanced digital experiences.
What is browser fingerprinting?
Browser fingerprinting is a set of tools and techniques that can capture data through a web user’s browsing activity.
More than just recording which browser is being used, browser fingerprinting can also capture information related to the user’s operating system, installed languages, time zone, keyboard layout, extensions and plugins, browser version, screen resolution, and more. These data points unite to create a unique identity or “fingerprint” of an individual visiting a website.
Browser fingerprinting technologies are a cornerstone for developer-led fraud prevention that cuts through spoofing attempts to identify users accurately. Moreover, it can do this without requiring additional permissions from the user.
Fingerprint’s open-source browser fingerprinting library has over 16,000 stars on GitHub and is used by 8,000+ websites, including 12% of the top 500 by traffic. Fingerprinting techniques on their own are over 90% accurate in correctly identifying a unique user in the browser. Businesses can further improve this accuracy with usage history, fuzzy matching, and probability engines.
Benefits of browser fingerprinting
Collecting website visitors’ fingerprints provides developers and site owners with a level of certainty about the intent of their website traffic. Browser fingerprinting’s unique attributes deliver a highly accurate methodology to protect an organization’s assets while leaving clues as to what users prefer in their online experience.
Fraud prevention
Browser fingerprinting is primarily used to detect and block users engaged in suspicious or fraudulent activities. For example, it can detect multiple attempts by different people using different devices and locations to access a single account that doesn’t belong to any one of the users.
Prioritizing prevention can help businesses avoid costly financial consequences: Cybercrime-related losses totaled $10.3 billion in 2022, bypassing 2021’s $6.9 billion total, according to the FBI Internet Crime Report.
Enhanced security
By stopping fraud in its tracks, browser fingerprinting not only safeguards individual users’ data but also protects the organization’s assets by halting malicious attacks via any individual, single point of entry.
Website optimization
Browser fingerprinting can help hypertarget and hyperlocalize your website traffic. Marketers and advertising technology companies can incorporate browser fingerprinting into their platforms.
The benefit here is twofold: First, it allows you to recognize a user’s fingerprint once they arrive on a web page. Then, almost immediately, it can display an ad most likely to resonate with that user’s behavior profile.
How browser fingerprinting works
Browser fingerprinting works through code embedded in a browser that relays information about the user’s system, session, hardware, and other attributes.
Data collection
First, data is collected via a snippet of JavaScript code. Some of the data is required for connection, such as user-agent strings and HTTP headers, which deliver browser type, version, and installed operating system.
JavaScript can also detect and collect data related to plugins and extensions, screen settings, time zones, and languages.
Combining data points
These attributes combine to create a unique fingerprint for the individual user. To prevent privacy issues, this fingerprint strips out any identifying personal data from the profile by assigning it a hash. Though anonymized, the fingerprint still serves as a unique identifier for a user.
Creating a unique fingerprint
As a benefit for both the user and the site owner, this unique identity doesn’t change as long as the user continues connecting from the same device — even if the user clears their cookie cache. This continuity reassures developers and site owners that normal browsing activity is occurring.
Browsers can capture many signals, including:
- User-agent details (browsers installed and their versions, operating system)
- Hardware details (screen resolution, battery usage, device memory)
- Browser plugins used
- The browser and OS settings
- WebGL parameters
When a visitor lands on a webpage, the fingerprinting function collects signals and compiles them into a hash that can be stored. Then, when visitors return to the website, match any past visit to their current visit to identify suspicious behavior or past fraudulent activity.
The more comprehensive the set of identifiers, the easier it becomes to narrow the list of potential fraudsters.
As an analogy, let's say you're a detective in a large city trying to find a bank robber's getaway car, as captured by a security camera. If the security camera caught some basic details (or signals) about the car, you can narrow your search considerably: model, color, manufacturer, etc.
With these signals, you may be able to uniquely identify the vehicle right away, especially if any of the specifics are particularly rare. However, hundreds of red Ford F-150 trucks may have standard-issue tires in a city with millions of drivers. The more standard the combination of signals, the harder it is to get a unique match.
In those cases, you hope that your camera may have gotten lucky and matched a unique signal about the vehicle: wood paneling, custom decal or logo, body damage, etc.
Fingerprinting works almost the same way: You’re trying to identify a visitor to a web or mobile application (suspect) by capturing signals passed via the visitor's browser or device (car) captured through a fingerprinting function (security camera).
How browser fingerprinting is used
There are several use cases for browser fingerprinting. While most of them are related to mitigating fraud, additional benefits include heightened security, increased privacy, and a better user experience.
When dealing with fraud, it’s important to remember that only a small percentage of visitors are responsible for most fraud cases. Therefore, a developer team aiming to reduce fraud on their website will need to find ways to isolate these visitors, verify their identity through authentication, and block them as required.
However, you’ll want to avoid putting up these roadblocks for the rest of your trusted traffic: Additional authentication can negatively affect the user experience, slowing users' ability to access their accounts, make purchases, and engage with your website.
Identifying bots and fake accounts
Browser fingerprinting helps distinguish real users from bots and identify fake accounts on digital platforms. Since a single fingerprint is associated with a particular device, location, and set of browsing behaviors, browser fingerprinting can detect when a device (perhaps with an unusual configuration or location) attempts to gain access to an account.
- For bot or brute force attacks (one user or a network of bots trying many combinations of usernames/passwords):
- Show a captcha after one unsuccessful login attempt on a fingerprint.
- Lock the user out of attempting login after five unsuccessful attempts on a fingerprint.
- For phished accounts (a user obtained someone else's legitimate login information through a scam or social engineering):
- Require two-factor or email authentication when attempting to log in with a new fingerprint.
- Blocklist specific fingerprinted visitors from your site based on their fingerprint.
In each case, an accurate fingerprint allows your team to pinpoint users attempting fraudulent behavior without affecting your trusted users’ experience.
Account takeover prevention
Account takeover is a common form of fraud where malicious users try to log in to other users' accounts and is an excellent use case for fingerprinting technology. Additional security at login can make account takeover much more difficult — though the type of authentication used may depend on the suspicious behavior your website experiences most often.
It’s also important to note that users intending to commit fraud are much more likely to use techniques to conceal their identity, including using incognito mode, browsing via a VPN, and disabling cookies. That's also where fingerprinting shines, as it can associate these users without needing easily concealed identifiers like cookies and IP addresses.
Two-factor authentication
Browser fingerprinting can enhance existing security measures in place, such as two-factor or multi-factor authentication, by adding another layer of user verification.
In this scenario, if the browser fingerprint doesn’t match the existing one for a user on a particular device, the site can trigger a request for the user to provide additional credentials (e.g., a four- or six-digit code sent to a mobile device or a code provided by an authentication app).
Browser fingerprinting enables you to incorporate the type of authentication needed into your website by using existing workflows without fundamentally changing your site's architecture.
Personalization
With additional information about the user, a website can instantly tailor content or deliver offers most likely to reflect the user’s preferences.
For example, the fingerprint may have captured information that the user has a browser plugin for shopping. The site owner can then populate web pages with content most likely to resonate with that user, such as coupons or discounts.
Why is this so important? Because customers prefer personalized experiences. Research supports this: McKinsey finds that 71% of consumers expect companies to deliver personalized interactions, and 76% become frustrated when this doesn’t occur.
Market research
Browser fingerprinting quietly provides invaluable market research for companies looking for greater customer insights. For example, the fingerprints may uncover a high volume of iOS users — specifically using the Safari browser. A company could then focus its design and development efforts to ensure that its UX is the absolute best it can be on iOS in order to increase engagement or sales.
Achieving high accuracy in fingerprinting: Balancing uniqueness and stability
For a fingerprint to be helpful as a method of identifying visitors, it must have high accuracy. When reducing the likelihood of false positives and negatives, a fingerprint should combine many signals and the right combination of signals that balance uniqueness and stability. For example, a highly unique signal will reduce your chances of a false negative, whereas stable signals will reduce your chances of a false positive.
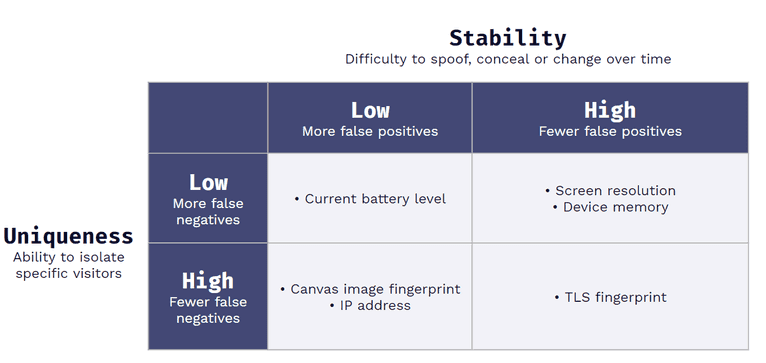
Using this framework, you can remove signals from your fingerprinting function altogether. If a signal has low uniqueness and stability, it is likely to change or be spoofed frequently and doesn't contribute meaningfully to identity.
Take our car example from earlier. In that situation, an attribute that changes might be whether the car has a dirty windshield. Because you can easily clean the windshield, you can’t count on this signal to improve your chances of finding the right vehicle.
In browser fingerprinting, the current battery level is a poor signal because a user can charge their device at any time. So, while that data is accessible, we remove it from our fingerprinting function.
Our Fingerprint Pro tool has an industry-leading accuracy rate: Visitors not correctly identified are either false positives or false negatives.
- False-positive: Multiple unique visitors are associated with the same fingerprint
- False-negative: One visitor over numerous visits is assigned different fingerprints
What is the difference between cookies and browser fingerprinting?
There should be special consideration for perfectly unique identifiers that are not always available.
Cookies store a unique identifier hash in the browser when a visitor first lands on your website. When a visitor has a cookie that matches a previous visit record in your database, you can be confident that these two visitors are the same. However, cookies are a very easy identifier to conceal:
- Users can clear cookies within their browser settings.
- Adblockers can disable cookies by default.
- Visitors can revoke consent for a website to track their cookies as part of GDPR or CCPA.
In these cases, instead of including a cookie as an identifier in your fingerprinting function, it can be more beneficial to use logic to determine when to use cookies as your identifier:
- If a cookie matches a previous record, use a cookie.
- If no cookie matches the previous record, use a fingerprint.
One of the main advantages of fingerprinting is that it’s stateless. A well-implemented fingerprint can remain stable through multiple sessions, incognito browsing, uninstalling or reinstalling apps, or clearing cookies.
For that reason, using both methods together can give a higher accuracy rate than either identification method alone.
One challenge is keeping up with changes in available signals as new browser versions are released. Anytime Chrome or Safari updates, identification techniques need to be re-evaluated to determine if there should be more tweaks to keep accuracy high.
Fingerprint Pro achieves its high accuracy rate by using fingerprinting, cookies, and additional machine learning techniques that incorporate IP address and geolocation. Our team is constantly working on the signals, algorithms, and techniques.
Browser fingerprinting vs. device fingerprinting
Intended for browser fingerprinting, our core Fingerprint library identifies website visitors using all modern mobile and desktop browsers. However, the signals available for mobile app developers differ from those retrieved in the browser and vary between iOS, Android, and other mobile operating systems.
If you want to identify users of a built-in mobile app, we have a few options in our product suite:
- Fingerprint Pro, in addition to browser fingerprinting, includes high-accuracy Android and iOS integrations that allow developers to integrate device identification into native Android and iOS apps.
- Our iOS open-source library
- Our Android open-source library
Protect your business against fraud with Fingerprint
By capturing data related to a user’s browser, device, and usage, browser fingerprinting has become an important tool for developers and site owners. Not only does it help safeguard against fraud and protect critical assets, but it also enhances the overall user experience.
With industry-leading accuracy, Fingerprint Pro incorporates industry-leading technologies to deliver a reliable, trustworthy platform for users and site owners alike.
Want to learn more about how Fingerprint can help your business elevate security and gain valuable customer insights? Contact our team today.
FAQ
Browser fingerprinting uses available device and browser attributed to gather data from web users' activity. It collects information on the operating system, installed languages, time zone, keyboard layout, extensions, plugins, browser version, screen resolution, and more to create a unique "fingerprint" of a website visitor. These technologies are crucial for developer-led fraud prevention, allowing accurate user identification without extra permissions.