Summarize this article with
What is new account fraud?
New account fraud, also called signup fraud, happens when fraudsters create fake or duplicate accounts on a platform, often at scale. It’s rarely just about one fake account. These actors usually run scripts, cycle through email addresses, and use synthetic data to spin up as many new identities as possible.
Some examples of new account fraud include:
- Incentive abuse: Creating fake accounts to repeatedly claim perks meant for new users. This includes things like signing up multiple times for free trials, farming promo codes, or exploiting referral bonuses to rack up rewards.
- Ban evasion: Creating new accounts to return to a platform after being banned for violating the rules. This often shows up in social platforms or marketplaces where banned users come back under a new identity to continue the banned activities they were removed for.
- Spam and manipulation: Spinning up fake accounts to distort perception, rankings, or trust signals. This can involve flooding products with fake reviews, rigging polls, sockpuppeting, or running coordinated campaigns to push specific narratives and spam.
- Limited resource exploitation: Using fake accounts to take up real resources or block access for legitimate users. For example, creating multiple accounts to procure and scalp hard-to-get or limited purchase items like concert tickets or Pokémon cards.
- Outcome rigging: Controlling multiple accounts to manipulate the outcome of games, bets, or competitive systems. This includes tactics like betting against yourself to guarantee a win or boosting rankings by playing against your own fake accounts.
The common thread is that the attacker is pretending to be multiple people, and your platform is footing the bill.
How does new account fraud impact businesses?
Beyond the operational headaches, new account fraud can create serious ripple effects, with one of the biggest impacts being resource drain. Fraudsters spin up endless accounts to milk free tier allowances, signup discounts, or referral programs, costing businesses real money while adding zero long-term value. This behavior not only deprives genuine customers of access but can also throw off inventory forecasting, skew conversion metrics, and inflate usage stats with noise instead of actual demand.
Fake accounts also distort credibility signals across platforms. Reviews, ratings, and poll results can be easily gamed when one person controls dozens of fake identities. Whether it’s downvoting a competitor’s product, rigging a user-voted contest, or unfairly stacking a giveaway, the result is the same: an unfair outcome that damages brand trust and discourages real user participation.
All of this contributes to a degraded user experience. Fraudsters may use fake accounts not only to spam or manipulate content, but to harass users or sow toxicity within communities. Without a reliable way to permanently ban repeat offenders, platforms risk becoming hostile environments where bad actors feel more persistent than the real users they’re driving away.
How do you detect and prevent fake signups?
Preventing fake signups is essential for preserving the integrity and trustworthiness of online platforms. As fraudsters use more sophisticated and automated methods, businesses must adopt robust, multi-layered defenses to secure their websites.
Using a variety of strategies can create multiple reinforcing layers of security. A few examples of these strategies include:
- Require email or phone verification: Email and phone verification add a layer of friction to the signup process by requiring users to confirm ownership of a valid contact method. While this won’t stop more determined attackers, especially those with access to bulk email or SIM services, it’s an effective baseline filter.
- Limit signups by IP: Monitor and restrict the number of accounts created from a single IP address. These restrictions can prevent mass account creation from the same source, though they may not catch fraudsters using VPNs or proxy servers. Additionally, it can inadvertently block legitimate users sharing an IP address, such as those at universities or workplaces.
- Use device and browser fingerprinting: Leveraging device and browser fingerprinting can identify devices, allowing websites to block multiple account creation attempts from the same device. Fingerprinting can repeatedly identify the same device or browser without relying on cookies, making it much harder for fraudsters to abuse signups.
- Look for high-risk signals: Analyze technical and behavioral clues during signup that suggest suspicious activity. These can include using VPNs or proxies, headless browsers, virtual machines, or signs of automation. You can catch fraud attempts early by flagging or blocking signups from environments with risky characteristics.
- Add CAPTCHA challenges: Implement CAPTCHA challenges during signup to block automated bots from creating accounts en masse. Distinguishing between human users and bots can drastically slow fake account creation; however, CAPTCHAs can add a lot of annoyance and friction, degrading the user experience for legitimate users.
Preventing fake signups with Fingerprint
Using device intelligence to spot repeat account creators and detect high-risk devices is a powerful strategy against new account fraud. It analyzes technical details like the operating system, screen resolution, installed fonts, and other browser or device characteristics to assess risk. It can also be used to generate a unique fingerprint or digital identifier. Unlike IP addresses or cookies, which are easy to reset or spoof, device fingerprints provide a more stable and reliable way to recognize returning devices, even across sessions and over time.
Fingerprint is a device intelligence platform that provides highly accurate identifiers for browsers and mobile devices. Our visitor IDs are stable for months, sometimes years. They can accurately recognize a returning browser or device, even when the user uses a VPN, clears cookies, or is in incognito mode.
We also offer Smart Signals that detect suspicious behaviors like browser tampering, VPN use, and automated bots. These signals help businesses identify risky activity early and build more intelligent strategies to keep fraudsters out.
Our Identification API lets you recognize returning devices to check whether they’ve been used previously to create accounts. You can implement this by capturing the visitor ID from Fingerprint during account creation and storing it alongside user data. When a new signup attempt occurs, simply check how many accounts are already linked to that device and decide how to handle it based on your business rules.
Want to see how? The following tutorial provides an example of implementing logic for preventing new account fraud using Fingerprint. You can try the final result on our website. The code snippets in the article are simplified for readability but the full code is open-sourced on GitHub.
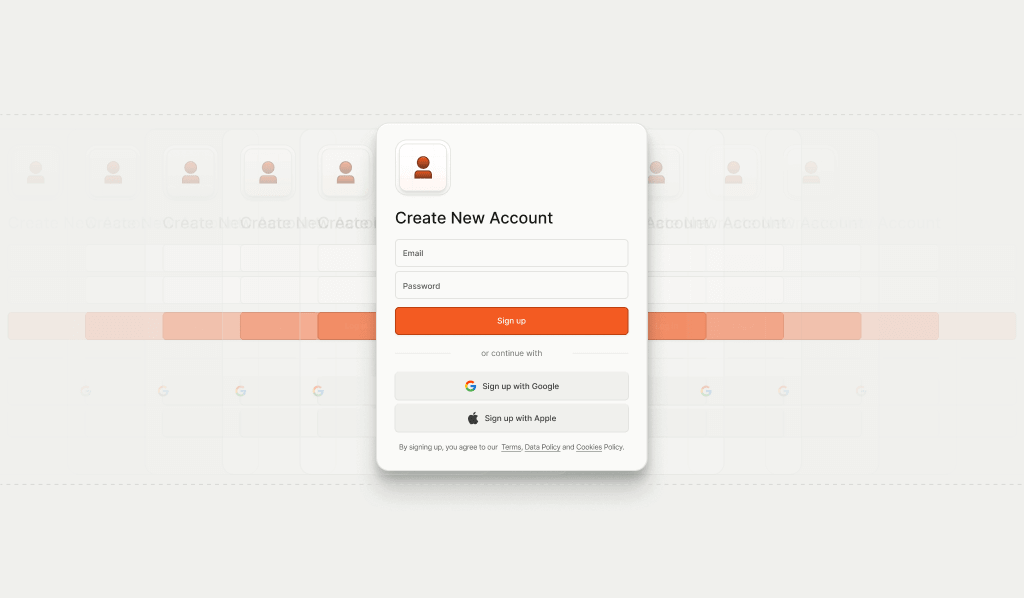
In this tutorial, we will only allow the user to sign-up for one free trial from a specific device. In practice, we recommend using a specific timeframe and a threshold for new accounts that work with your business use case.
1. Obtaining a visitor identifier
You can sign up for a free trial if you don’t have a Fingerprint account. Then you’ll be able to find your API keys in the dashboard.
The first step in preventing new account fraud is to obtain the visitor identifier.
To begin with, incorporate the Fingerprint JavaScript agent into your webpage. Consider using one of our SDKs if your front end uses popular frameworks like React or Svelte.
// Initialize the agent.
const fpPromise = import("https://fpjscdn.net/v3/YOUR_PUBLIC_API_KEY").then(
(FingerprintJS) =>
FingerprintJS.load({
endpoint: "https://metrics.yourdomain.com",
})
);Note: We recommend routing requests to Fingerprint's APIs through your domain for production deployments using the optional endpoint parameter. This routing prevents ad blockers from disrupting identification requests and improves accuracy. We offer a variety of ways to do this, which you can learn more about in our guide on how to protect your JavaScript agent from ad blockers.
Let’s use a trial sign-up page as an example:
When the user attempts to create a trial account, request the visitor identifier. At this time, Fingerprint will analyze over 100 browser and device signals and identify the visitor. You will receive a visitorId which is unique to the visitor and a requestId that is unique to every identification request. Send the requestId with the potential new account details to your server.
// src/app/new-account-fraud/NewAccountFraud.tsx
async function onNewAccountSubmit(submitEvent) {
submitEvent.preventDefault();
// Collect browser signals and request visitor identification
// from the Fingerprint API. The response contains a requestId.
const { requestId } = await (await fpPromise).get();
const formData = new FormData(submitEvent.currentTarget);
const username = formData.get('username');
const password = formData.get('password');
// Send the new account details together with the requestId.
const newAccountData = {
username,
password,
requestId,
};
const response = await fetch("/new-account-fraud/api/create-account", {
method: "POST",
body: JSON.stringify(newAccountData),
headers: {
"Content-Type": "application/json",
},
});
handleNewAccountResponse(response);
}2. Validating the visitor identifier on the server
From here on out, you should perform the following steps in the create account route handler, using the Fingerprint Server API.
To get the full identification event details, use the requestId you received with the Server API /events endpoint. This endpoint allows you to get additional data like whether the user is using a VPN, has tampered with their browser, or is a bot.
// src/app/new-account-fraud/api/create-account/route.ts
export async function POST(req: Request): Promise<Response> {
const { username, password, requestId } = await req.json());
// Get the full Identification result from Fingerprint Server API and validate its authenticity
const fingerprintResult = await getAndValidateFingerprintResult({ requestId, req });
if (!fingerprintResult.okay) {
return NextResponse.json(
{ severity: 'error', message: fingerprintResult.error },
{ status: 403 }
);
}
You can use one of our SDKs if your backend logic uses Node.js or any other popular server-side framework or language.
To access the Server API, you must use your Secret API Key. You can create one from the Fingerprint dashboard at Dashboard > App Settings > API keys. Here is an example using the Server API via the Node SDK:
// src/server/checks.ts
import {
EventResponse,
FingerprintJsServerApiClient,
isEventError,
} from '@fingerprintjs/fingerprintjs-pro-server-api';
export const getAndValidateFingerprintResult = async (
requestId: string,
request: Request,
): Promise<{ okay: boolean; data?: EventResponse, error?: string }> => {
// The Server API must contain information about this specific identification request.
let identificationEvent: EventResponse;
try {
const client = new FingerprintJsServerApiClient({ apiKey: SERVER_API_KEY });
identificationEvent = await client.getEvent(requestId);
} catch (error) {
if (isEventError(error) && error.status === 404) {
return { okay: false, error: 'Request ID not found, potential spoofing attack.' };
}
return { okay: false, error: String(error) };
}
const identification = identificationEvent.products?.identification?.data;
// More checks...
return { okay: true, data: identificationEvent}
}The Server API response will contain information about this specific identification request. If the request for this information fails or doesn't include the visitor information, the request might have been tampered with, and you should not trust this identification attempt. Read our documentation to learn more about how to protect against client-side tampering and replay attacks.
Now that we have access to the visitor ID and Smart Signals we can incorporate them into the new account fraud logic. A common tactic for fraudsters is using an automated bot to try and programmatically create a large amount of new accounts. You can use the Bot Detection Smart Signal to check and block any automated activity.
Here is an example that could be included after the “More checks…” comment above:
// Get the bot detection data from the identification event.
const botDetection = identificationEvent?.products?.botd?.data;
// Block any detected bot activity.
// Potential responses: "bad", "good", "notDetected"
if (botDetection?.bot?.result != "notDetected") {
reportSuspiciousActivity(req);
saveAndBlockBotIp(botDetection.ip);
return { okay: false, error: 'Failed to create new account.' };
}3. Checking for multiple signups
If the device is not high-risk, the next step is to check if this visitor has made multiple new accounts.
Query your data storage for any user accounts associated with the visitor identifier. You can then decide how to handle the new account request, such as denying the creation or requesting additional verification.
In this demo, an account can only be created if the visitor identifier is not already associated with another account. If there is an existing account, we return an error to the user, stating that an account has already been created with this device.
// src/app/new-account-fraud/api/create-account/route.ts
// Get visitorId from the Server API Identification event
const visitorId = fingerprintResult.data.products.identification?.data?.visitorId;
if (!visitorId) {
return NextResponse.json(
{ severity: 'error', message: 'Visitor ID not found.' },
{ status: 403 }
);
}
// Check if an account already exists for this visitorId
const existingAccount = await AccountDbModel.findOne({ where: { visitorId } });
if (existingAccount) {
return NextResponse.json(
{ severity: 'error', message: 'An account has already been created with this device.' },
{ status: 409 },
);
}
}
If the visitor passes all the above validation, continue creating the new account and return a successful response. Make sure to include the visitor ID so you can use it to check against future account creation attempts.
// If not, create a new account
await AccountDbModel.create({
visitorId,
passwordHash: hashString(password),
username,
timestamp: new Date(),
});
return NextResponse.json(
{ severity: 'success', message: 'Account created.' },
{ status: 200 }
);
Key takeaways
Stopping multiple fake account signups is essential for keeping online platforms secure and trustworthy. With defenses against signup fraudsters, companies can retain resources and present a great user experience for their legitimate users.
Determined fraudsters can bypass basic protections like IP blocking and email verification. However, tools like CAPTCHA can be annoying and add friction, frustrating legitimate users. Balancing strong protections with an excellent user experience requires using more sophisticated techniques like browser and device fingerprinting to recognize them accurately and detect high-risk devices.
Contact our team if you'd like to learn more about Fingerprint's highly accurate visitor identification, or start a free trial to see it in action for yourself.
FAQ
It’s when attackers create fake or duplicate accounts to exploit promotions, launder money, exploit platforms, or evade bans. It challenges businesses by skewing metrics, draining resources, increasing fraud, and eroding trust.
Most detection relies on IP addresses, user agents, or cookies, but these are easy for fraudsters to reset or spoof. They can clear cookies, rotate IPs using VPNs or proxies, and even sanitize browser settings. To avoid detection, they often mimic actual user behavior, like typing patterns or click timing, making fake accounts look legitimate on the surface.
Use device intelligence to identify unique devices, even if users clear cookies or use incognito mode. Limit the number of accounts that can be created from the same device or fingerprint. Add verification steps like email or phone confirmation to slow down automated abuse and continuously monitor for devices showing signs of automation or spoofing.