Summarize this article with
Did you know that cyber attacks rarely stop at a single compromised login? Once a fraudster gains access, they often look for ways to move laterally within an organization, allowing them to target additional accounts and company data, and escalate privileges, leaving the door open for future exploitation.
The challenge here isn’t just preventing that first compromise but also in a general lack of visibility. Many teams lack the necessary information to easily connect identity, device, and behavioral data across systems, resulting in blind spots that attackers can exploit.
In this article, I explain how companies can counter these risks by closing the gaps in identity security and access management with real-time device intelligence signals.
How device intelligence helps power identity security & access management
Many identity and access management systems stop at simply verifying credentials. They don’t go deeper into what device they're using or the users' behaviors. Without deeper visibility into the environment behind each login, critical context is lost. As a result, risk and fraud teams wind up making decisions without a complete picture of user or device behavior — especially as new identities like AI agents and third-party integrations are added to the mix.
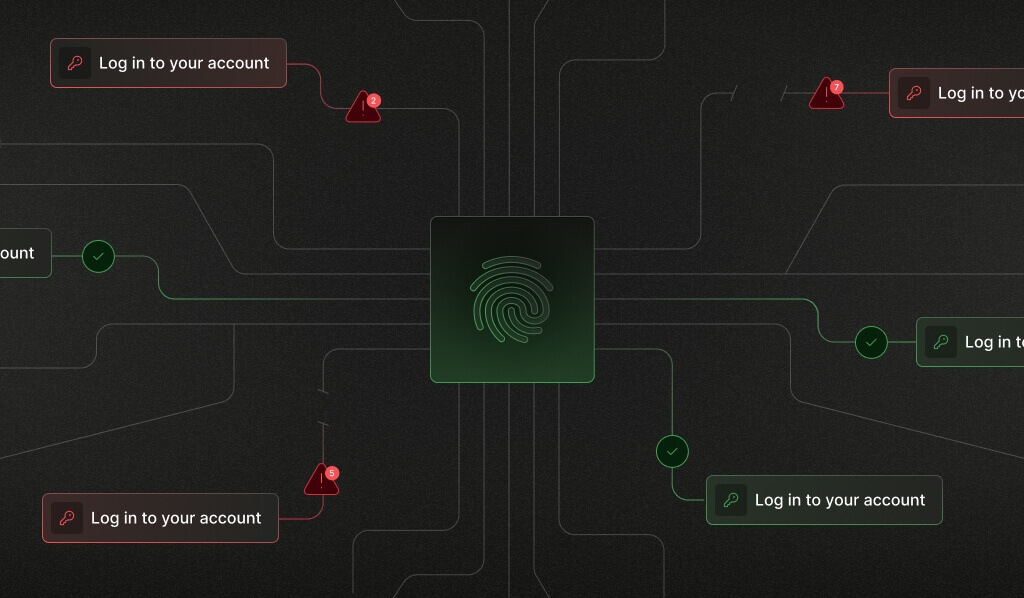
To help close this gap, companies need to adopt an integrated identity security fabric that weaves together identity, device intelligence, and behavioral intelligence so teams can respond to security threats faster and more effectively. By integrating device intelligence as part of the authentication flow, teams can get access to real-time signals that connect the dots between user, session, and device data so they can more accurately assess risk.
For example, when logging in, authentication flows should perform device and behavioral checks when deciding whether to grant or deny access. Device intelligence can run invisibly in the background to provide critical information at multiple points: During the initial sign-in to assess risk (e.g., is this a trusted device or a new one exhibiting suspicious behaviors?) and determine whether step-up authentication like MFA should be triggered, and post log-in for ongoing session monitoring for suspicious activity.
For example, a device intelligence platform like Fingerprint analyzes over 100 signals, including browser attributes, network configurations, and device settings, to generate and assign each visitor a unique visitor ID. This visitor ID persists over months or even years, enabling identity security and access management platforms and workflows to recognize previously vetted visitors and spot potentially suspicious ones in real time.
Fingerprint’s Smart Signals further extend the platform’s capabilities by surfacing nuanced risk factors before and at the moment of login. Signals like VPN and Proxy Detection, Bot Detection, Browser Tampering Detection, and Virtual Machine Detection provide real-time insights into the context of every login attempt. For instance, if a device uses a proxy to obscure its location or if automation tools are present, the corresponding Smart Signal can flag the event as potentially high risk.
Ultimately, integrating device intelligence as part of identity security and access management transforms device data into real-time risk signals that can be used to enhance every login — from the moment credentials are entered to the point access is granted or denied.
Building a secure, user-friendly future for authentication
Modern threats require a new approach to identity security and access management. By adopting a unified identity security fabric that includes device intelligence, organizations can deliver simple and secure user experiences, minimize blind spots, and stay ahead of evolving cyber attack techniques.
If you’re interested in strengthening your authentication flows with industry-leading device intelligence, contact us for a personalized demo.