Summarize this article with
Why account takeover protection needs more than front-end tactics
Account takeover fraud is evolving rapidly. Fraudsters have moved far beyond simple password guessing or brute-force attacks. We now see them leveraging sophisticated malware and tampering browsers to sidestep even advanced security measures.
As developers and security teams, our experience has shown us how these attacks can slip through the cracks when device intelligence is limited to only what happens in the browser. Let’s take a closer look at how these attacks work, where front-end-only solutions break down, and why genuine account takeover (ATO) protection needs a deeper, server-side approach.
How attackers use malware and browser tampering to bypass defenses
Fraudsters today have access to an extensive toolkit. Malware infostealers are engineered to grab everything of value: browser cookies, tokens, browser version, device details, and more. They typically reach victims through phishing emails, malvertising, drive‑by downloads (when malware installs just by visiting a malicious website), or pirated and cracked software bundled with hidden malware.
The stolen data is quickly sent to attacker‑controlled servers, often giving fraudsters everything they need to hijack accounts or bypass basic fingerprinting. The attacker can use tampering browsers like Octo Browser, Indigo Browser, or AdsPower to recreate a nearly identical environment to fool basic fingerprinting.
These tampering browsers go far beyond changing a user agent or spoofing a handful of headers. They can manipulate browser APIs, load stolen cookies, and inject cloned basic browser fingerprints. When an attacker spins up this cloned profile, a site using basic, client-side‑only fingerprinting sees all the same details it remembers from the real user: the same browser version, screen resolution, installed fonts, and even valid session cookies.
From the site’s perspective, this looks like a familiar device returning to log in, not a brand‑new one controlled by an attacker. With stolen credentials, they can bypass MFA, and with a valid session cookie, they may already appear logged in.
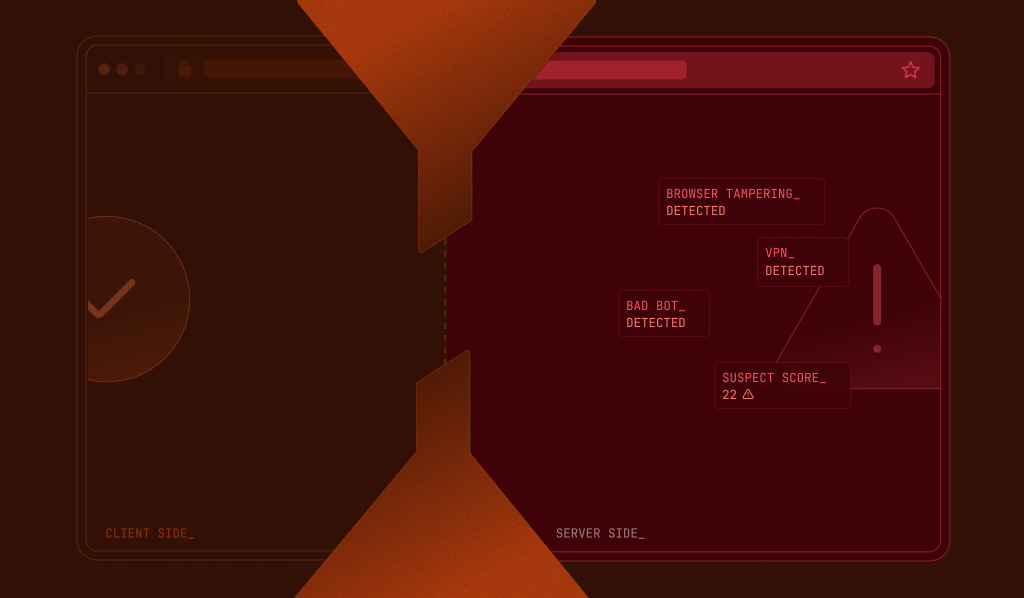
This allows attackers to appear fully authentic, making it nearly impossible for client‑side‑only solutions to tell a legitimate user from a fraudster using stolen data. The sophistication of these tools means that even advanced browser fingerprinting can be bypassed unless results are validated and enriched with server‑side intelligence.
Where client-side-only device intelligence falls apart
Device intelligence tools that operate entirely in the browser are especially vulnerable to these attacks. When all identification logic and signal collection happens on the client side, attackers know exactly what is being gathered and how it is transmitted. With full access to browser data and the ability to manipulate APIs, fraudsters can replay a “safe” device profile or tweak the fingerprint data to match what your checks expect.
Any validation or fraud detection that relies solely on client-side signals can therefore be bypassed. Attackers can replay previously captured fingerprints, modify them, or create entirely new ones before your server ever sees the data. Without server-side signal collection and validation, there is no way to confirm whether the signals are fresh, consistent, or genuine.
This leaves a significant gap in your defenses. ATO attempts can easily slip past front-end protections, putting your users and your business at risk. Even open-source browser fingerprinting libraries, while useful for some scenarios, offer no protection against attackers who can see, modify, and replay all the data in the browser.
How Fingerprint raises the bar for account takeover protection
At Fingerprint, we take a different approach to device intelligence. We combine front-end signal collection with server-side device intelligence to prevent fraud and block account takeover attempts.
When a visitor interacts with your site, our JavaScript agent or mobile SDK gathers over 100 data points and sends them to Fingerprint’s servers, where we perform additional server‑side signal collection and visitor ID generation or retrieval. This step adds data points that pure client‑side fingerprinting can’t see and generates a stable visitor ID. During this process, we also check whether the incoming signal payload is being maliciously replayed. If it is, the attempt is flagged in the response with a replayed boolean.
The response your frontend receives contains either a request ID or an encrypted payload based on your workspace configuration. On your server, you can securely retrieve the full timestamped visitor identification data using the request ID or decrypt the encrypted payload directly. This ensures that identification results haven’t been tampered with in transit and that your backend is always working with verified data.
This multi-layer design prevents attackers from spoofing or replaying fingerprints while giving you access to our 20+ Smart Signals — including Bot Detection, VPN Detection, and Browser Tampering Detection — in a secure, server‑validated workflow. Even if an attacker steals browser data and tries to impersonate a device, the combination of Fingerprint’s server‑side checks and your backend verification makes replay attempts detectable and actionable.
Why free client-side device intelligence isn't really free
It’s easy to be tempted by free device intelligence tools, especially those bundled with other services or available as open-source libraries. But if a solution can’t stop targeted spoofing or sophisticated ATO attacks, it doesn’t provide much value for accounts requiring high security. The true cost of a successful account takeover — lost revenue, damaged customer trust, and the time spent on remediation — quickly eclipses any savings from using a free, front-end-only solution.
Some teams may believe that multi-factor authentication (MFA) is enough to protect against account takeover. However, requiring MFA every time a new cookie or device is detected can frustrate users and degrade the experience. Worse, if cookies are stolen and replayed by an attacker, even MFA can be bypassed. Server-side signal analysis and validation, like the approach we take at Fingerprint, is what makes the critical difference, ensuring that every identification event is genuine and untampered.
Don’t settle for spoofable device intelligence
Modern account takeover attacks are engineered to bypass front-end-only solutions. Fraudsters know how to clone browser environments, replay device profiles, and slip past client-side checks. If you want to keep fraudsters out, you need server-side device intelligence that actually works — even if it means investing beyond free tools.
If you’re interested in strengthening your account security, you can start a free trial with Fingerprint or explore our documentation to see how our technology can help you stop sophisticated ATO attacks before they start.
FAQ
Fraudsters use malware to steal cookies and device data, then recreate these environments using tampering browsers. This allows them to appear as a legitimate returning user.
No. If an attacker steals valid cookies or session tokens, they can bypass MFA. Server-side device validation is needed to confirm that a session is genuine.
Free solutions often rely only on client-side checks, which are easily spoofed. A successful ATO attack can cost far more than investing in robust, server-validated protection.