Summarize this article with
For fraud prevention teams, rooted devices are a pain point that can’t be ignored. They give fraudsters more ways to tamper with your app, bypass security, and compromise sensitive data. If your business handles payments, personal information, or anything else fraudsters find tempting, you need to know how to spot rooted devices and what to do about them.
Let’s dig into what rooting actually means, why it’s risky, how detection works, and how Fingerprint’s Smart Signals make it easier to keep your app, your data, and your users safe.
What is a rooted Android device?
A rooted Android device is one where someone has gained “root” (administrator-level) access to the operating system. Normally, Android puts up plenty of guardrails: system files are protected, dangerous settings are locked down, and apps can’t just do whatever they want. Rooting smashes through these protections. Suddenly, the user and anyone else with access can:
- Install custom versions of Android (custom ROMs)
- Change or delete protected system files
- Run apps that need elevated permissions
- Tweak system behavior in ways manufacturers never intended
Rooting gives users full control, but it also strips away the built-in protections that keep malware, spyware, and sketchy apps at bay. Without those safeguards, even a small mistake can lead to serious security risks.
Why rooting is risky
Rooted devices open the door to a laundry list of fraud and security headaches. Not only are they used by fraudsters, but legitimate users who root their own devices open themselves up to malicious software. Here’s why they matter to anyone who cares about fraud prevention:
Bypassing app security controls
Rooted devices let users and fraudsters run tools that can tamper with your app’s code, intercept sensitive data, or fake their identity. That “secure” login is a lot less secure when someone can mess with the underlying system.
Enabling account takeover attacks
With root access, a fraudster can more easily install keyloggers, modify app logic, or automate attacks to steal credentials. This is a fast track to account takeover attacks, where legitimate users lose control of their accounts.
Data theft and privacy breaches
Rooted devices can grant malicious apps access to protected data — think saved passwords, payment info, or sensitive messages. For industries like banking, payments, and e-commerce, this is a compliance and reputational disaster waiting to happen.
Promotional abuse and fake accounts
Fraudsters love rooted devices for creating and controlling multiple fake accounts, bypassing device-based restrictions, or gaming referral programs.
Undermined device security
Rooting disables many of Android’s built-in defenses, such as verified boot and app sandboxing. Once those are gone, it’s open season for malware and fraud tools.
In short: If you’re serious about fraud prevention, rooted devices need to be on your radar, especially if your business handles anything valuable.
How rooting is detected
Detecting a rooted device isn’t always straightforward because rooting methods keep evolving. Still, there are several signs that fraud teams and security-minded apps can look for:
Root management apps
Tools like Magisk, SuperSU, or KingRoot are used to manage root access. If these are present, the device is almost certainly rooted.
Altered system files
Rooting often involves modifying or replacing key system files. If these files are missing, changed, or have suspicious permissions, it’s a red flag.
Suspicious system behaviors
Rooted devices might show abnormal behaviors, like running processes with elevated privileges, or system binaries that don’t match the official Android build.
Custom ROMs and bootloaders
Devices running unofficial versions of Android or unlocked bootloaders are more likely to be rooted.
Unusual app permissions
Apps with permissions that should be impossible for a normal user to grant (like access to protected system directories) are another warning sign.
No single indicator is foolproof. That’s why layered detection, using multiple signals, is the best approach.
Rooted Device Detection with Fingerprint Smart Signals
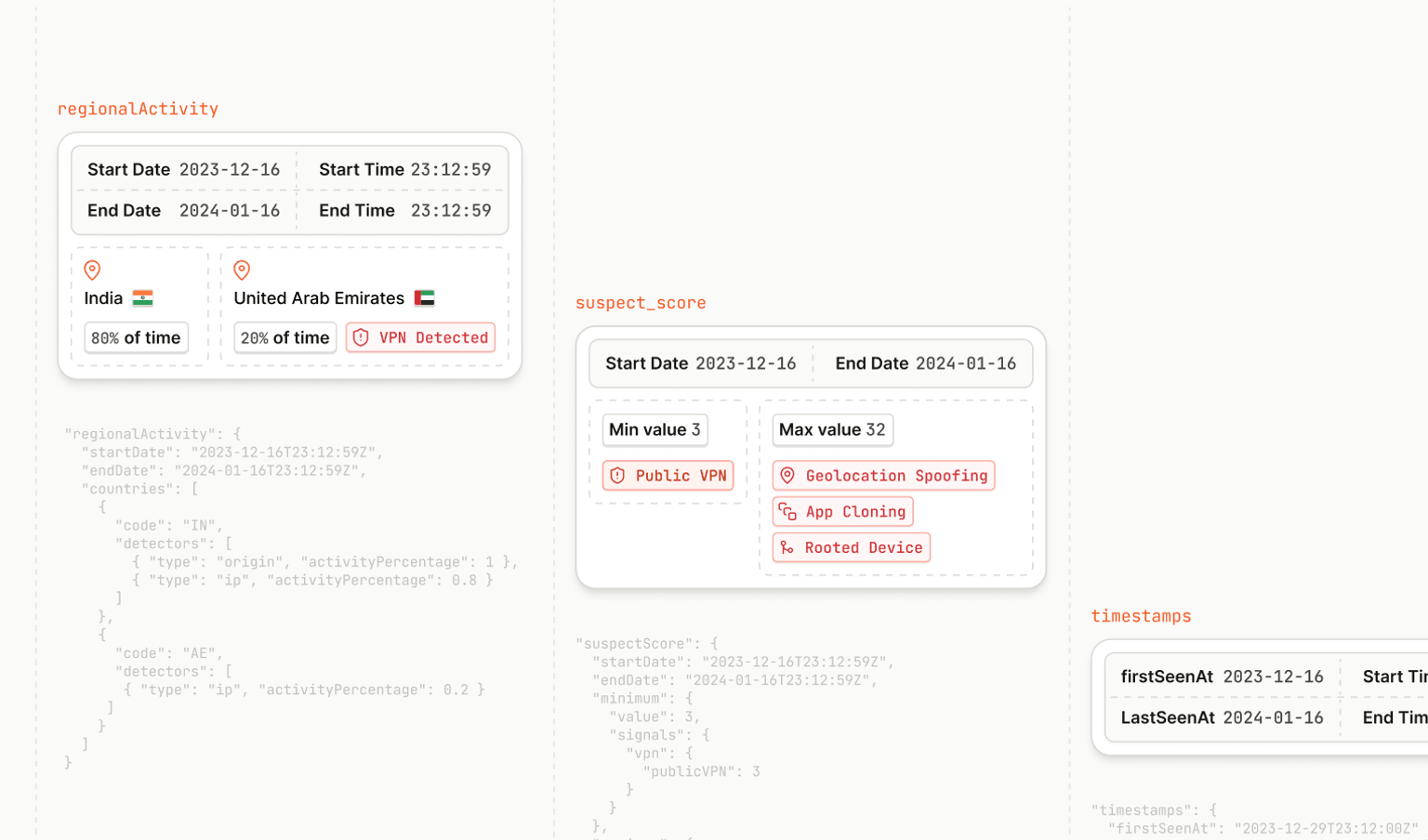
Identifying these signals on your own can be tricky and require constant maintenance, but Fingerprint can help. Fingerprint is a device intelligence platform that uses over 100 device, network, and behavioral signals to identify devices and assess risk. Among its 20+ Smart Signals, Rooted Device Detection is specifically designed to spot Android devices that have been rooted.
How Fingerprint’s Rooted Device Detection works
Fingerprint’s Rooted Device Detection Smart Signal checks for:
- Presence of root management apps (like Magisk)
- System-level indicators of rooting
- Behaviors consistent with root access
The result is delivered as a simple “true” or “false” signal, making it easy to feed into your risk logic. If root management tools are detected, the device is flagged as rooted.
Why this matters for fraud prevention
Accurate rooted device detection lets you:
- Identify high-risk devices before they can cause trouble
- Adjust authentication or restrict sensitive features for rooted devices
- Inform your risk models with real-time device security status
Rooted Device Detection works best as part of a broader device intelligence strategy. Fingerprint also provides Smart Signals for Android Emulator Detection, Cloned App Detection, Factory Reset Detection, Frida Toolkit Detection, VPN Detection, and more. Combining these signals gives fraud teams a much clearer picture of device risk, helping you spot suspicious behavior before it becomes a problem.
Visitor identification and device persistence
When you use Fingerprint’s Android SDK, you get a unique identifier for each device. This visitor ID is persistent across most scenarios:
| Scenario | Same visitor ID? |
|---|---|
| App or device restart | Yes |
| App data/cache cleared | Yes |
| App uninstalled and reinstalled | Yes |
| Device factory reset | Yes (in most Android models) |
| Multiple user profiles on same device | Yes |
This means even if a fraudster tries to wipe their tracks by reinstalling the app or clearing data, you’ll still recognize the device. That’s a huge advantage for fraud prevention.
Best practices for using Rooted Device Detection
Rooted Device Detection is a powerful Smart Signal, but it works best as part of a risk-based approach. Here’s how to get the most out of it:
Use it as one factor in your risk model
Don’t automatically block every rooted device. Some legitimate users root their phones for harmless reasons. Instead, use Rooted Device Detection as one factor in your broader risk assessment. Combine it with other Smart Signals, like Emulator Detection or VPN Detection, to build a clearer picture.
Communicate with your users
If you decide to limit functionality or block access for rooted devices, let users know why. Clear messaging can prevent confusion and reduce support headaches.
Apply graduated responses
Not all rooted devices are equally risky. Maybe you restrict access to sensitive features, require additional authentication, or flag the account for review instead of blocking outright.
Stay up to date
Rooting methods change. Make sure your detection solution is updated regularly to keep pace with new tools and techniques.
How to get started with Fingerprint Rooted Device Detection
Implementing Rooted Device Detection in your Android app is straightforward:
- Integrate the Fingerprint Android SDK
- Process the
rootAppssignal in your risk logic on your backend - Decide how you’ll respond to rooted devices — extra authentication, feature restrictions, or something else
Rooted Device Detection is available as part of Fingerprint’s Pro Plus and Enterprise plans. For more details, check out the Smart Signals reference.
Staying ahead of fraudsters
By understanding what rooting is, recognizing the risks, and using advanced detection like Fingerprint’s Smart Signals, fraud teams can stay one step ahead. Device intelligence is about making smarter risk decisions, faster.
For more information on Smart Signals, including Rooted Device Detection, visit the Smart Signals reference. If you’re ready to see how Fingerprint can help your team spot risky devices and reduce fraud, you can get in touch with our sales team or sign up for a free trial to see it in action.
Ready to solve your biggest fraud challenges?
Install our JS agent on your website to uniquely identify the browsers that visit it.