With 2022 wrapping up, we wanted to feature some of our favorite posts from throughout the year. Catch up on ten of our favorite blog posts below and get to know everything from TLS fingerprinting to audio fingerprinting to how to permanently ban users on your site.
The Top Browser Fingerprinting Techniques Explained
 What is browser fingerprint and how does it work? In The Beginner’s Guide to Browser Fingerprinting for Fraud Detection, we discuss the basics of browser fingerprinting, why accuracy matters for accurately identifying website visitors, and how browser fingerprinting helps detect and prevent fraud.
What is browser fingerprint and how does it work? In The Beginner’s Guide to Browser Fingerprinting for Fraud Detection, we discuss the basics of browser fingerprinting, why accuracy matters for accurately identifying website visitors, and how browser fingerprinting helps detect and prevent fraud.
Life after ANDROID_ID: Android Identification via Device Fingerprinting
 Have you ever wondered how websites and apps identify your smartphone? There is a method called device fingerprinting, which works by using behavioral characteristics unique to your Android device. This technology can be used for security verification and collecting user data to tailor online experiences better. Read Life after ANDROID_ID: Android Identification via Device Fingerprinting to learn more about device fingerprinting, how the Fingerprint Android Library works, and why you should use our library for device identification!
Have you ever wondered how websites and apps identify your smartphone? There is a method called device fingerprinting, which works by using behavioral characteristics unique to your Android device. This technology can be used for security verification and collecting user data to tailor online experiences better. Read Life after ANDROID_ID: Android Identification via Device Fingerprinting to learn more about device fingerprinting, how the Fingerprint Android Library works, and why you should use our library for device identification!
How the Web Audio API is used for audio fingerprinting
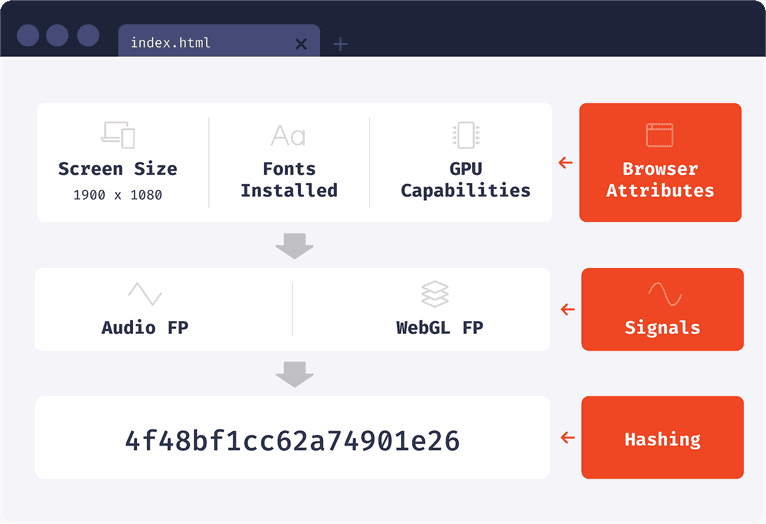 Audio fingerprinting is an invaluable tool for developers who want to add rich audio experiences to their web and mobile applications. With the emergence of Web Audio API, it has become possible to identify audio samples using digital fingerprints created from the captured source signals. In How the Web Audio API is used for audio fingerprinting, we explore how Web Audio API is leveraged specifically for audio fingerprinting and what benefits it offers compared to traditional methods.
Audio fingerprinting is an invaluable tool for developers who want to add rich audio experiences to their web and mobile applications. With the emergence of Web Audio API, it has become possible to identify audio samples using digital fingerprints created from the captured source signals. In How the Web Audio API is used for audio fingerprinting, we explore how Web Audio API is leveraged specifically for audio fingerprinting and what benefits it offers compared to traditional methods.
Demo: Disabling JavaScript Won’t Save You from Fingerprinting
 Have you ever gone online and been intrigued by how popular sites like Google and Amazon know who you are no matter what device or network connection you use? Demo: Disabling JavaScript Won’t Save You from Fingerprinting showcases a demonstration of fingerprinting, a practice where browsers can still recognize users even after disabling JavaScript. We’ll give an overview of what happens during this process and provide visual evidence through screenshots and analysis on which specific elements are relevant when fingerprinting is deployed against web browsing sessions.
Have you ever gone online and been intrigued by how popular sites like Google and Amazon know who you are no matter what device or network connection you use? Demo: Disabling JavaScript Won’t Save You from Fingerprinting showcases a demonstration of fingerprinting, a practice where browsers can still recognize users even after disabling JavaScript. We’ll give an overview of what happens during this process and provide visual evidence through screenshots and analysis on which specific elements are relevant when fingerprinting is deployed against web browsing sessions.
Incognito Mode Detection: Detecting Visitors Who Browse in Private Mode
 Using Incognito Mode detection is an effective tool for detecting and understanding user behavior. This method can give you better user data, allowing you to make smarter decisions when creating content or developing campaigns. With the right strategies in place, Incognito Mode detection can be beneficial as it provides insight into your customers’ behaviors while still offering them anonymity. Read Incognito Mode Detection: Detecting Visitors Who Browse in Private Mode to review four methods of detecting visitors using Incognito mode and discuss which browsers support these methods.
Using Incognito Mode detection is an effective tool for detecting and understanding user behavior. This method can give you better user data, allowing you to make smarter decisions when creating content or developing campaigns. With the right strategies in place, Incognito Mode detection can be beneficial as it provides insight into your customers’ behaviors while still offering them anonymity. Read Incognito Mode Detection: Detecting Visitors Who Browse in Private Mode to review four methods of detecting visitors using Incognito mode and discuss which browsers support these methods.
How Does Canvas Fingerprinting Work?
 Canvas fingerprinting is a form of browser-based tracking that leverages features found on almost every computer made in the last decade: the HTML5 canvas element. Using a combination of fonts, color depths, and other data points unique to each device can generate an “identity" that's nearly impossible to spoof. In How Does Canvas Fingerprinting Work?, we cover how canvas fingerprinting works, what it can (and can't) be used for, and everyday use cases for businesses looking to implement a comprehensive security strategy. Finally, we'll discuss why you should be generating your canvas fingerprints so you are best equipped to protect yourself from malicious users online.
Canvas fingerprinting is a form of browser-based tracking that leverages features found on almost every computer made in the last decade: the HTML5 canvas element. Using a combination of fonts, color depths, and other data points unique to each device can generate an “identity" that's nearly impossible to spoof. In How Does Canvas Fingerprinting Work?, we cover how canvas fingerprinting works, what it can (and can't) be used for, and everyday use cases for businesses looking to implement a comprehensive security strategy. Finally, we'll discuss why you should be generating your canvas fingerprints so you are best equipped to protect yourself from malicious users online.
Six Ways to Permanently Ban Users from Your Website
 As a website owner, one of your most important responsibilities is ensuring you can provide visitors with the best possible experience. One of the challenges is ensuring certain users who may be damaging or detrimental to your content are blocked from accessing it. Thankfully, there are many measures available that you can use to make sure these individuals don't get access by using various unique identifiers. In 6 Ways to Permanently Ban Users from Your Website, we explain how you can use fingerprinting to block specific users from viewing web pages on your site.
As a website owner, one of your most important responsibilities is ensuring you can provide visitors with the best possible experience. One of the challenges is ensuring certain users who may be damaging or detrimental to your content are blocked from accessing it. Thankfully, there are many measures available that you can use to make sure these individuals don't get access by using various unique identifiers. In 6 Ways to Permanently Ban Users from Your Website, we explain how you can use fingerprinting to block specific users from viewing web pages on your site.
What is TLS fingerprinting?
 Do you ever wonder how secure connections between websites and your computer work? TLS (Transport Layer Security) Fingerprinting is essential in securely connecting a web server to its users by verifying that both parties are who they say they are. In What is TLS fingerprinting?, we explore what TLS fingerprinting is and how it works to provide cyber security for individuals and organizations.
Do you ever wonder how secure connections between websites and your computer work? TLS (Transport Layer Security) Fingerprinting is essential in securely connecting a web server to its users by verifying that both parties are who they say they are. In What is TLS fingerprinting?, we explore what TLS fingerprinting is and how it works to provide cyber security for individuals and organizations.
The Top Browser Fingerprinting Techniques Explained
 As technology advances, so does the sophistication of cyberattacks and fraud prevention tools. Browser fingerprinting is quickly becoming integral to detecting unusual activity - whether for user authentication, fraud detection, or personalization purposes. While many are aware browser fingerprinting exists, few know the specifics of how it works and its various techniques. In The Top Browser Fingerprinting Techniques Explained, we explain in detail what browser fingerprinting is, the four primary techniques employed by websites and businesses today, and how these techniques are used for fraud detection and prevention.
As technology advances, so does the sophistication of cyberattacks and fraud prevention tools. Browser fingerprinting is quickly becoming integral to detecting unusual activity - whether for user authentication, fraud detection, or personalization purposes. While many are aware browser fingerprinting exists, few know the specifics of how it works and its various techniques. In The Top Browser Fingerprinting Techniques Explained, we explain in detail what browser fingerprinting is, the four primary techniques employed by websites and businesses today, and how these techniques are used for fraud detection and prevention.
How to Generate A Browser Fingerprint in PHP (with code snippets)
 We all know that security plays an essential role in our digital lives, and with increased online threats, it's more important than ever to ensure the integrity of user data. One way to provide better protection for your website is by implementing browser fingerprinting methods in your codebase. This process securely identifies users through unique characteristics stored in their devices. In How to Generate A Browser Fingerprint in PHP (with code snippets), we look at browser fingerprinting and how it can be generated using PHP code snippets so you can add extra layers of menace-proof protection to your web applications.
We all know that security plays an essential role in our digital lives, and with increased online threats, it's more important than ever to ensure the integrity of user data. One way to provide better protection for your website is by implementing browser fingerprinting methods in your codebase. This process securely identifies users through unique characteristics stored in their devices. In How to Generate A Browser Fingerprint in PHP (with code snippets), we look at browser fingerprinting and how it can be generated using PHP code snippets so you can add extra layers of menace-proof protection to your web applications.
We look forward to 2023 bringing us more content, webinars, and product releases! Stay up to date on the articles we release in 2023, join our newsletter or schedule a demo with our sales team.