Summarize this article with
Introduction
The balance between consumer convenience and security is delicate, especially in a competitive, high-value market. For example, when banks and credit card companies provide online loan applications, they make it convenient for potential customers to get a loan and for identity thieves and hackers.
The amount of money lost may vary, but it raises consumer costs and leads to hefty monetary losses for financial institutions. The most significant channel for fraudsters is the mobile market, as more financial institutions continue to provide services using apps.
Statistics about Loan Fraud:
- In 2021, the National Mortgage Application Fraud Risk Index increased by 15% between the first quarter of 2021 and the first quarter of 2022.
- Credit card fraud skyrocketed by the last quarter of 2021. Fraud affects everyone, from consumers to the banks that approve applications.
What is Loan Fraud?
Loan fraud occurs when an individual or a company misrepresents or omits relevant information with the intent to secure a loan they may not qualify for or on terms they would not receive should the truth be disclosed. Loan fraud manifests in various forms, from income falsification to identity theft. It can also occur through sophisticated scams, including phishing schemes to obtain personal data, which they then use to apply for loans under untrue pretenses.
For example, an applicant might inflate their income on a loan application to meet the lending criteria, effectively misleading the lender regarding their accurate financial stability.
The consequences of loan fraud are far-reaching, impacting financial institutions through monetary loss and innocent victims with compromised personal information and potentially damaged credit scores. Additionally, fraudulent loans can distort a lender's risk assessment, leading to tightened credit markets and increased interest rates for legitimate borrowers.
How Does Loan Fraud Work?
Loan fraud begins with the consumer. The many ways attackers can obtain personal information depend on their vectors. Some attackers use phishing emails and malicious websites. Others use a variety of ways to install malware on a targeted user's local device, and some local thieves steal unshredded paperwork from garbage cans to collect private information.
Identity Theft
An identity thief usually targets many consumers to collect as much information as possible. Their goal is to sell the data, not use it themselves. With enough personal data, an attacker can make a seven-figure return on their investment.
Experian estimates that a social security number is worth $1, but online banking credentials are worth $20-$200 each.
The loan application fraud begins after the buyer obtains personally identifiable information (PII) on darknet markets or other methods. Using a combination of bots, VPNs (virtual private networks), and proxies, the attacker submits loan applications using a victim's information.
The fraudster might be outside of the victim's country, so they get an unsuspecting co-conspirator to use their local country address to have credit cards sent. The co-conspirator then uses the cards to buy products to send to the attacker. The attacker might use the credit cards to purchase products and send the stolen products to a local co-conspirator's address so the co-conspirator can forward the stolen goods to the fraudster.
Credit card fraud isn't the only version of loan fraud. Fraudsters also target mortgages, bank accounts, payday lenders, car notes, and other "buy now, pay later" agreements. Because loans often work with more significant amounts of money and expensive products, it's a high-risk issue for lenders and a long-term credit report issue for consumers.
Loan Fraud + Bot Attacks
To take it a step further, some attackers use scripts to automatically test credentials purchased on darknet markets.
There are two reasons an attacker uses bots:
- To verify stolen credentials and sell them to fraudsters or
- To authenticate a victim's financial accounts and use them to open loans, transfer money, or purchase products using the victim's credit cards.
Every online entity experiences bot traffic, but recent research shows that about 28% of bot activity is from "bad bots." Bots work faster than humans so that attackers can cover many more sites and target victims in a short amount of time.
Specific factors signal that traffic is bot activity, such as unusual user agents, missing headers, and high-speed web activity. However, a good bot creator designs scripts to factor in human elements to bypass simple fraud detection.
You can learn more about bot attacks and how to protect against them in our guide: Bots Are Taking Over The Web - Here's How to Fight Back.
Bot Attack + Account Takeover: Sentry MBA
Consider a popular account takeover tool called Sentry MBA. With software like Sentry MBA, scammers can test millions of usernames and passwords on a targeted site, and because of its availability and ease of use, it's become incredibly popular.
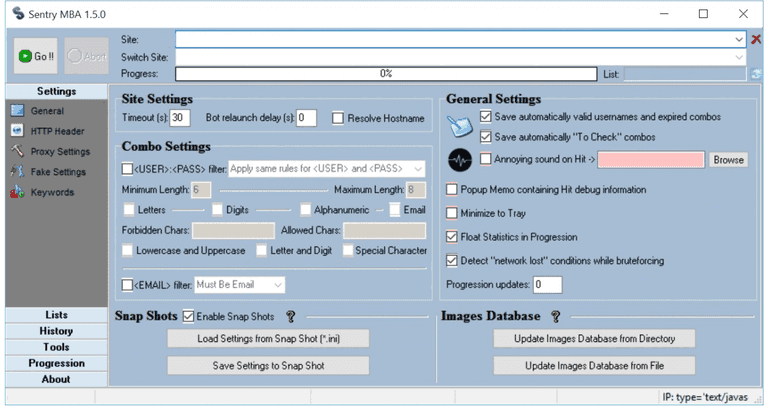
Source: F5 Networks Sentry MBA PDF
The attacker can add timeouts to avoid too many requests quickly. Custom HTTP headers can be added to look like a human user, and various password rules can be set to collect as many cracked accounts as possible. It can even upload images of driver's licenses to a target website. The software enables account takeover fraud, including financial targets.
To combat bot activity, financial institutions need sophisticated bot detection. Determining activity is a bot rather than a human user, which will significantly reduce risks. However, this won't stop manual fraud. It will help prevent more sophisticated collaborative financial fraud efforts.
Preventing Loan Application Fraud
It's impossible to expect every consumer to avoid identity theft. Human error is always an issue for any business, leaving financial institutions responsible for stopping identity theft and fraud. Whether it's bots or human fraudsters, financial institutions or those offering loan application services can take steps to minimize risk.
Third-party identity validation services
Using artificial intelligence and video analytics, users take a picture of themselves or upload a driver's license image. An identity validation service will verify the authenticity of the information using various public databases and machine learning systems.
Micro deposits
For online banks using credit card validation, send two small amounts to the applicant's bank account or a credit card, such as $.01 or $1.00. Then, the applicant must enter both amounts correctly before verifying their account.
Multi-factor authentication (MFA)
Multi-factor authentication can block the completion of the login procedure, stopping the account takeover. As a result, attackers can no longer access an account from a simple credential list and bot program, so they cannot open loans or order credit cards using a stolen consumer account.
MFA push notification authentication
Instead of relying on credentials alone, push notifications can be sent to the account holder's phone. Then, the account owner taps a button to verify the authentication request is valid. This method stops bots and human attackers with stolen credentials.
Video call verification
Some companies use video calls where the user holds their government document (e.g., passport or driver's license) for identification in front of the camera to compare the user's face to the submitted official government documentation.
Using Fingerprint for Fraud Prevention
Standard fraud prevention methods have various bypasses, so just one strategy isn't enough to stop a sophisticated and determined attacker.
Fingerprint is a device intelligence solution that uses machine learning to detect returning users with industry-leading accuracy. Each visitor receives a visitor identifier, generated using various device and browser elements such as the specific browser (e.g., Chrome or Firefox), screen resolution, operating system, and browsing patterns.
Developers can associate previous fraudulent activity with a current session, even when the attacker attempts to conceal their identity. With this information, developers can block loan applications, send a loan application to the fraud department, or display an error message to the viewer.
In addition, using Fingerprint, your developers can customize the loan application process should an ID come up as duplicate or utilize our bot detection solution to detect bot activity better.
FAQ
Lenders can protect themselves from loan fraud by implementing robust identity verification processes, using advanced fraud detection systems that leverage machine learning and AI, and regularly training their staff on the latest fraud tactics and prevention strategies.