Summarize this article with
Account takeover attacks aren’t just a nuisance — they’re a constant threat for security teams, fraud analysts, and anyone responsible for keeping user accounts safe. Credential leaks, phishing, and automation mean even the strongest authentication can be bypassed.
Enter impossible travel detection: a method for catching suspicious logins when a user appears to “teleport” between distant locations at speeds that would make even an astronaut jealous. If you’re building or tuning authentication workflows, impossible travel detection is a must for staying ahead of fraudsters and keeping friction low for real users.
Why impossible travel detection matters
Passwords are weak. Attackers buy or steal credentials and log in from anywhere. Impossible travel detection spots when a login pattern simply doesn’t add up, like a user logging in from Paris and then, 20 minutes later, from Sydney.
Detecting this helps you catch:
- Account takeover attacks, where a fraudster uses stolen credentials from a remote location
- Credential sharing that violates your terms of service
- Automated attacks that use global proxy networks
Impossible travel detection doesn’t just block bad actors. By focusing on patterns that are physically impossible, it also helps you avoid annoying legitimate users with constant, unnecessary step-up authentication.
What is impossible travel detection?
Impossible travel detection is exactly what it sounds like: a system for identifying login events that would require a user to travel at impossible speeds between locations. The core principle is simple: If a user logs in from one country and then logs in from another country thousands of miles away just minutes later, something’s off.
The system compares the time and distance between consecutive login events for the same account and calculates the speed required to make that journey. If the speed is higher than what’s possible for commercial travel (usually around 500–600 miles per hour), the system flags it as suspicious.
Impossible travel detection is especially effective for banking, enterprise logins, or SaaS platforms, but it’s also useful for consumer-facing apps where abnormal activity needs to be caught quickly.
How to detect impossible travel
Impossible travel detection is a sequence of checks that combine location data, time analysis, and a bit of math.
Step 1: Collect location data
Most systems use IP geolocation to estimate where a login comes from. Each login event is tagged with a timestamp and an approximate latitude/longitude based on the IP address.
Step 2: Calculate travel time and distance
For each new login, the system looks at the previous login event for the same account. It calculates the “great-circle” distance between the two locations (the shortest path over the earth’s surface).
Step 3: Compare against realistic travel speeds
The system divides the distance by the time elapsed between logins to get the required travel speed. If that speed is above what’s possible for commercial flights (usually 500–600 mph), it’s considered “impossible travel.”
Step 4: Flag anomalies
When an impossible travel event is detected, the system can trigger an alert, prompt for additional authentication, or temporarily block access, depending on your policy.
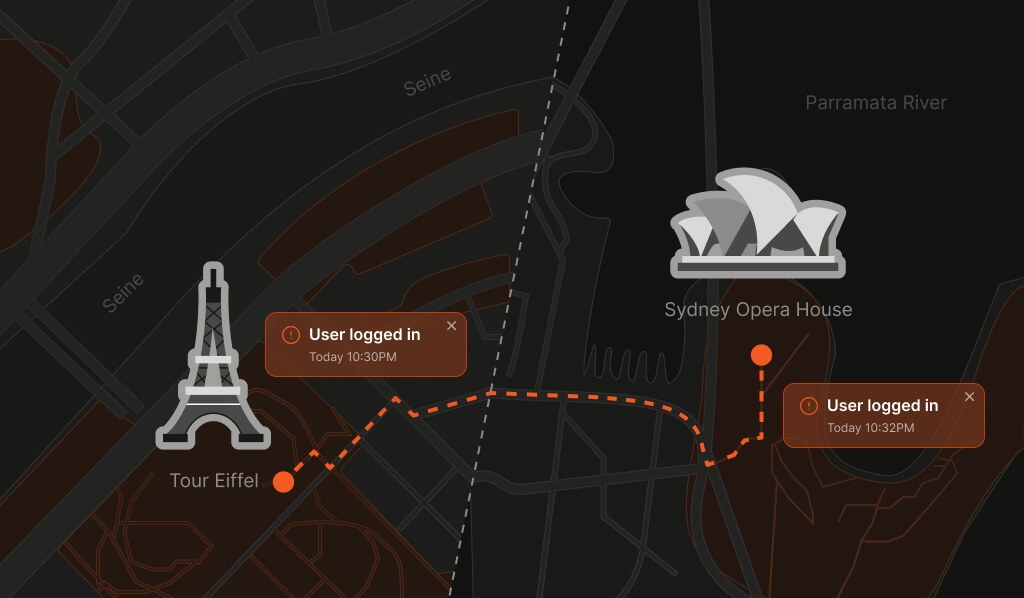
Example
A user logs in from San Francisco at 9:00 a.m., then from Singapore at 9:45 a.m. That’s over 8,000 miles in 45 minutes — an average speed of more than 10,000 mph and a clear sign of compromise.
Caveats
IP geolocation isn’t perfect. Mobile networks, virtual private networks (VPNs), and proxies can make a user appear to jump locations. That’s why impossible travel detection works best when combined with other device and behavioral signals.
How Fingerprint improves impossible travel detection
Impossible travel detection is powerful but not foolproof, and that’s where device intelligence comes in. Fingerprint is a device intelligence platform that uses over 100 device, network, and behavioral signals to assign a unique visitor ID to each user session. This visitor ID remains stable even if the user clears cookies, uses a VPN, or uses incognito mode. By combining impossible travel detection with Fingerprint’s device intelligence, you can dramatically improve accuracy in detecting unusual activity and reduce unnecessary friction for real users.
What does this mean in practice?
- Same device, different locations: If the same visitor ID shows up in two distant locations within minutes, it’s likely a VPN or proxy is involved. You can use this insight to tune your response (for example, prompt for multi-factor authentication instead of blocking access).
- Different devices, impossible travel: If two different visitor IDs are used within an impossible timeframe, it’s a stronger signal of account takeover or credential sharing.
Adding context with Smart Signals
Fingerprint also provides 20+ Smart Signals to help you spot suspicious activity and add context to impossible travel events:
- VPN Detection: Indicates when a login comes from a VPN, which could explain apparent “teleportation.”
- Velocity Signals: Detects when a single device or visitor ID is associated with an unusually high number of IP addresses or locations in a short window.
- Bot Detection: Flags automated browsers and scripts that may trigger impossible travel patterns.
- Browser Tampering Detection: Spots when browsers are manipulated to evade identification.
- IP Geolocation and IP Blocklist: Provides location data and checks if the IP is associated with known proxies or past abuse.
By layering these Smart Signals with impossible travel logic, you can better distinguish between risky events and harmless anomalies. For example, a login from a new country using the same visitor ID and a known device might be legitimate. But if the same account is accessed from two continents, using two different visitor IDs, and one is flagged for bot activity, it’s time to sound the alarm.
Best practices for robust fraud defenses
Impossible travel detection is a key piece of the fraud prevention puzzle, but it works best as part of a layered approach. Here’s how to build a defense that’s both effective and user-friendly:
1. Combine signals
Don’t rely on impossible travel alone. Cross-check with device intelligence, behavioral analytics, and contextual risk signals. This reduces false positives and ensures you’re not locking out legitimate users who happen to be on the move or using privacy tools.
2. Adapt authentication based on risk
When impossible travel is detected, don’t just block access. Prompt for step-up authentication or verify with out-of-band methods. If device intelligence suggests a low-risk scenario (same visitor ID, known device), you can let the user through with minimal friction.
3. Monitor and tune your thresholds
Travel speed thresholds aren’t one-size-fits-all. Analyze your user base, review flagged events, and adjust your logic to fit real-world usage. Regularly update your geolocation data and device intelligence sources for the best results.
4. Integrate with your broader security stack
Feed impossible travel alerts into your fraud analytics and incident response workflows. The goal is to spot abnormal patterns early and act fast.
5. Respect privacy and compliance
Collect and store only the minimum data needed for fraud detection, and make sure your policies align with regulations like the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA).
If you’re evaluating platforms, look for solutions that combine impossible travel detection with device intelligence. Fingerprint’s device intelligence offers this kind of layered approach, giving you the flexibility to adapt responses based on risk, reduce false positives, and keep your users happy.
The future of impossible travel detection
Impossible travel detection is essential for any serious account protection strategy. It flags the telltale signs of account takeover, credential sharing, and automated abuse by catching logins that defy the laws of physics. But on its own, it can’t tell you everything — VPNs, proxies, and mobile networks can muddy the waters.
The best fraud defenses combine impossible travel detection with device intelligence, behavioral analytics, and contextual risk signals. By layering data from Fingerprint’s visitor ID and Smart Signals, you can tune your responses, reduce friction for legitimate users, and catch fraudsters before they do damage.
If you’re ready to see how device intelligence and impossible travel detection can work together, start a free trial below or contact our team to talk through your specific needs.
Ready to solve your biggest fraud challenges?
Install our JS agent on your website to uniquely identify the browsers that visit it.
FAQ
There isn’t a single universal threshold for impossible travel detection, since it depends on how your fraud detection system calculates time and distance between logins. Many systems define a maximum plausible travel speed as the speed of a commercial jet. If the calculated travel speed between logins exceeds that, it’s flagged as impossible.