Summarize this article with
Ban evasion is a persistent challenge. Just when you think you’ve permanently removed a problematic user, they reappear under a new name and with a fresh account. For moderation and fraud teams, this is a direct challenge to your platform’s integrity. If banned users can waltz right back in, what’s the point of having rules in the first place?
Fraudsters don’t just accept bans and move on. They treat bans as puzzles to solve, returning with fresh tricks and more determination. This constant cycle undermines your efforts at deterrence, erodes community trust, and turns moderation into an endless game of cat-and-mouse.
For fraud teams, ban evasion is a technical arms race. Fraudsters evolve fast, so your defenses need to evolve faster. That means moving beyond yesterday’s solutions and building layered, adaptive defenses.
How ban evasion undermines user banning
Ban evaders rarely rely on just one method. They use a mix of tricks, often in combination, to slip past basic defenses. Here are the usual suspects:
IP rotation and VPNs
Changing IP addresses is the classic move. With a virtual private network (VPN) or proxy, fraudsters can appear to connect from anywhere. Some automate IP rotation, cycling through hundreds of addresses.
Device spoofing and browser manipulation
Platforms look for device clues, so evaders get creative. They switch devices, use virtual machines, or run [anti-detect browsers]((https://fingerprint.com/blog/anti-detect-browser-detection) that randomize hardware and software details. Some manually alter browser settings or use extensions to mask their setup. The goal: break any link between their banned account and their new one.
Alternate account creation
Getting banned doesn’t stop a determined fraudster from signing up again. They use temporary email services, create accounts from different locations, or buy “aged” accounts to blend in. Some build networks of “sock puppet” accounts, activating new ones as needed.
Behavioral camouflage
The most persistent evaders know platforms look for behavioral patterns. So they change posting styles, vary activity times, and avoid repeating the mistakes that got them banned. Some even study public discussions about ban evasion to stay ahead of detection.
All these tactics make one thing clear: If you’re only blocking by username, email, or IP, you’re not stopping the determined evaders — you’re just slowing them down.
Why IP blocks and cookies alone don’t stop evaders
Relying on IP addresses, cookies, or basic account blocklists is about as effective as locking your front door and leaving the windows wide open.
IP-based blocks
IP addresses are easy to change. With VPNs, proxies, and mobile hotspots, fraudsters can swap IPs in seconds. Plus, legitimate users often share IPs — think coffee shops, schools, or offices — so blocking by IP can lock out innocent people.
Cookies and local storage
Cookies are fragile. Users can block or clear them, or just use incognito mode. Some fraudsters automate cookie clearing as part of their evasion routine. If your ban system depends on cookies, it’s a single browser reset away from being bypassed.
Simple account blocklists
Email addresses are cheap and disposable. Temporary email services let evaders create dozens of accounts in minutes. Even phone verification isn’t foolproof. Burner numbers and SMS forwarding services are everywhere.
How to detect ban evasion
Detecting ban evasion at scale is a moving target. Fraudsters adapt fast, so your detection systems need to be just as nimble. Here’s how the best teams approach the problem:
Automation and supervised learning
Manual review doesn’t scale. Automated systems flag suspicious behavior based on patterns, like a burst of new accounts from the same device, or unusual navigation flows. Supervised learning models can be trained to recognize subtle signals of ban evasion, improving over time as new data comes in.
Layered detection
No single signal is enough. Effective systems combine device intelligence, behavioral analysis, network signals, and account history. For example, you might flag an account that shares a device fingerprint with a banned user, uses a VPN, and creates multiple accounts in a short period.
Continuous tuning
Ban evasion is a moving target. Detection rules and models need constant updates as fraudsters adapt. That means regular analysis of false positives and false negatives, retraining models, and adding new signals as they become relevant.
Real-world feedback loops
Moderators and fraud analysts need tools to investigate flagged accounts, see linked behaviors, and refine detection criteria based on what actually works. Combining automated detection with human review makes it much harder for evaders to slip through the cracks.
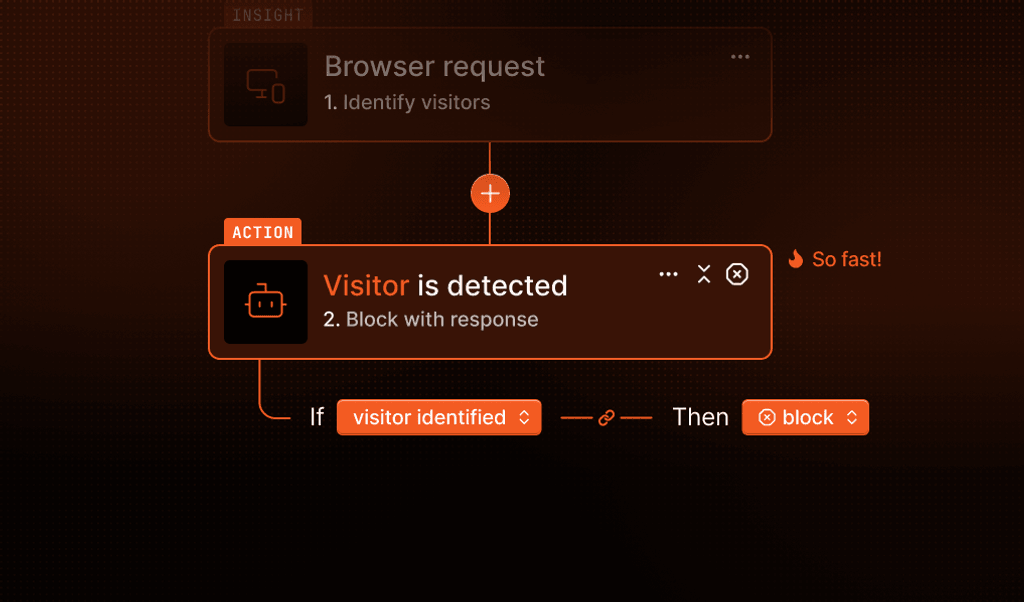
Device fingerprinting: A stronger foundation for user banning
Device fingerprinting offers a way to see past the superficial tricks and focus on the underlying device itself.
How Fingerprint works
Fingerprint is a device intelligence platform that collects more than 100 browser and device signals — everything from installed fonts and hardware specs to rendering quirks and network attributes. These signals are combined to generate a unique, stable visitor ID for each device visiting your website. Unlike cookies or IP addresses, this visitor ID stays consistent even when users clear cookies, use a VPN, or use incognito mode.
Linking new accounts to banned devices
When a new account is created, you can check if the visitor ID matches any that were previously banned. If there’s a match, the platform can flag the account for review or apply additional verification steps. This approach catches evaders who would otherwise slip through by changing superficial identifiers.
Smart Signals: Detecting suspicious behaviors
Device fingerprinting is just the start. Fingerprint provides more than 20 Smart Signals that help flag behaviors commonly associated with ban evasion:
- Bot Detection: Identifies automated browsers like Selenium or Puppeteer, which are often used for mass account creation.
- VPN Detection: Flags when visitors are using VPNs to conceal their true location.
- Browser Tampering Detection: Detects anti-detect browsers or manual changes to browser configuration.
- Velocity Signals: Detects unusually high numbers of IP addresses, countries, or accounts associated with a single device in a short period.
These signals provide context for investigations. If a new account shares a visitor ID with a banned user and is also using a VPN or anti-detect browser, that’s a strong indicator of ban evasion.
Strengthening fraud investigations
Combining visitor ID with Smart Signals lets fraud teams build a layered risk profile for each account. You’re not just asking, “Is this the same device?” but also, “Is this device behaving in ways typical of ban evasion?” This makes it much harder for fraudsters to hide and helps prioritize which accounts need closer review.
Ready to make ban evasion a thing of the past?
Ban evasion isn’t going away, but your detection strategy doesn’t have to be stuck in the past. Relying on IP blocks, cookies, or simple account blocklists is a losing game against determined fraudsters. The most effective teams use a layered approach combining device intelligence, behavioral analysis, and automated detection that adapts as evasion tactics evolve.
Fingerprint’s device intelligence and Smart Signals provide a robust foundation for alternate account detection, linking new signups to banned devices and flagging suspicious behaviors before they become a problem. If you’re serious about stopping ban evasion and protecting your platform, take a closer look at what device intelligence can do for your fraud prevention stack. See how it works for yourself with a free trial or talk through your platform’s specific needs with our team.
Ready to solve your biggest fraud challenges?
Install our JS agent on your website to uniquely identify the browsers that visit it.
FAQ
IP addresses are easy to change using VPNs, proxies, or mobile hotspots. They can also block innocent users who share the same IP, making them unreliable as the sole method of detection.