Summarize this article with
Android is the #1 operating system in the world. While most Android users are legitimate, the flexibility of the Android operating system makes it an attractive target for malicious actors. Unfortunately, when someone first uses your Android app, you often don't know much about them, their historical behavior, or their intent.
But that's about to change! Introducing Fingerprint's Device Reputation Network (DRN), the world’s first developer-centric, self-serve network of device information. Fingerprint identifies millions of Android devices globally every day. When you identify an Android device using the Fingerprint SDK, that device likely has previously already been identified by other Fingerprint customers. Now, you can access all that historical information via Fingerprint's Device Reputation Network (DRN) API.
With Fingerprint's DRN API, Android SDK users can query our network using the visitor ID from an identified device and get globally aggregated Smart Signals, gaining crucial historical insights into that user's prior behavior and characteristics of that Android device.
These insights include information on a device's location history and past suspicious behavior over the last 30 days. By incorporating this data, you can include past behavior in your predictive fraud models and fraud prevention strategies, adding historical cross-network insights to Fingerprint's existing visitor identification and Smart Signals suite for advanced fraud detection.
Fingerprint’s DRN API is especially applicable to markets with a high concentration of Android smartphones. For example, in India, 95% of smartphones operate on the Android platform, meaning that over 700 million consumers in that region alone can engage in online transactions on Android. In countries like Indonesia, Turkey, and Brazil, Android has a market share of over 85%.
The Device Reputation Network is available at no extra charge for all Fingerprint Android SDK customers, whether you are taking advantage of our Pro Plus self-service offering or our Enterprise plans. The DRN API is free to use but rate-limited to prevent abuse. If you'd like to request a higher rate limit, please contact us at drn@fingerprint.com.
Fingerprint’s Device Reputation Network: The technical details
Fingerprint generates and stores an internal unique device identifier every time a visitor ID is generated, along with a collection of Smart Signals for each identified Android device. When we recognize the device again, new Smart Signal data is added to the existing dataset.
To get started, you'll need to integrate Fingerprint with your native Android apps with our Android SDK. The DRN supports three global signals: Regional Activity, Suspect Score, and Timestamps.
Regional activity provides a list of countries where the identified device was active in the last 30 days, along with the activity level in each country. We provide this number for two different "detector types":
- The Origin Detector detects the device's actual location, regardless of the IP address location or attempts to hide the user's location using a VPN. Importantly, the origin detector does not require user geolocation permissions.
- The IP Detector assigns a country code based on the IP address used by the device. If the device uses a VPN, the IP detector will return the VPN exit node country.
Regional activity history can help detect unusual travel patterns, such as travel between high-risk areas and other behaviors that look suspicious for a specific user.
Fingerprint's Suspect Score is a weighted representation of all Smart Signals collected from a device that helps identify suspicious activity. The DRN version extends this knowledge, representing the minimum and maximum Suspect Scores we captured from the identified device in the last 30 days globally across the entire Fingerprint device network. We provide the absolute value, the exact signals that contributed to the score, as well as a zero-excluded percentile, which can take four possible values (0.25, 0.5, 0.75, and 0.95).
For example, suppose the maximum Suspect Score percentile is 0.95. This means that the device was more suspicious than 95% of the other suspicious devices that Fingerprint identified in the same 30-day period. This means that even if the device doesn't display any suspicious attributes when it's using your app, you can still factor in a device’s past behavior and characteristics into your risk models.
Finally, Timestamps provide the exact times when we first and last saw this device on the Fingerprint device network.
Accessing DRN signals
The new DRN signals are accessible via API, similar to how you would access Smart Signals with the Server API, but using the DRN API. First, you need to make an identification request, which will return a visitorId for the device. Below is a Kotlin example using our native Android SDK:
import com.fingerprintjs.android.fpjs_pro.Configuration
import com.fingerprintjs.android.fpjs_pro.FingerprintJSFactory
// Initialize and configure the SDK
val fpjsClient = FingerprintJSFactory(applicationContext).createInstance(
Configuration(apiKey = "YOUR_PUBLIC_API_KEY", region = Configuration.Region.US)
)
// Get a 'visitorId'
fpjsClient.getVisitorId { visitorIdResponse ->
val visitorId = visitorIdResponse.visitorId
// Use the visitorId here
}You can then use that visitorId to make a GET request to the /drn endpoint of the DRN API. This new endpoint takes a visitor ID as a URL parameter and a comma-separated list of signals you want to receive as a query parameter. You will also need to include your secret API key as a bearer token.
curl --request GET \
--url https://drn-api.fpjs.io/drn/{VISITOR_ID} \
--header 'Authorization: Bearer {API_KEY}' \
--header 'X-api-version: 2024-09-01'Now that you have access to the DRN API data in your app, let's break down what data is available and how to use it.
API responses
As of version 2024-09-01, DRN supports three global signals: regional_activity, suspect_score, and timestamps. Let's take a look at the data each one provides and how you can use them.
regional_activity
This signal represents a list of countries where the identified device was active in the last 30 days, together with the level of activity in each country. The level of activity is a number between 0 and 1 and represents the percentage of activity in the country. For example, if a device was active in a specific country 60% of the time, the level of activity will be 0.6. Note that the level of activity is scoped to a detector type.
We support two detector types: originand ip.
The origin detector detects the device's real location, utilizing our originCountry feature of the mobile SDK VPN detection, regardless of the IP address location or attempts to hide the location using a VPN. The origin detector does not require geolocation permissions from the user.
The ip detector detects a country code by the IP address at the moment of making an API call using the Android SDK. If a device is using a VPN, the ip detector will return the VPN exit node country.
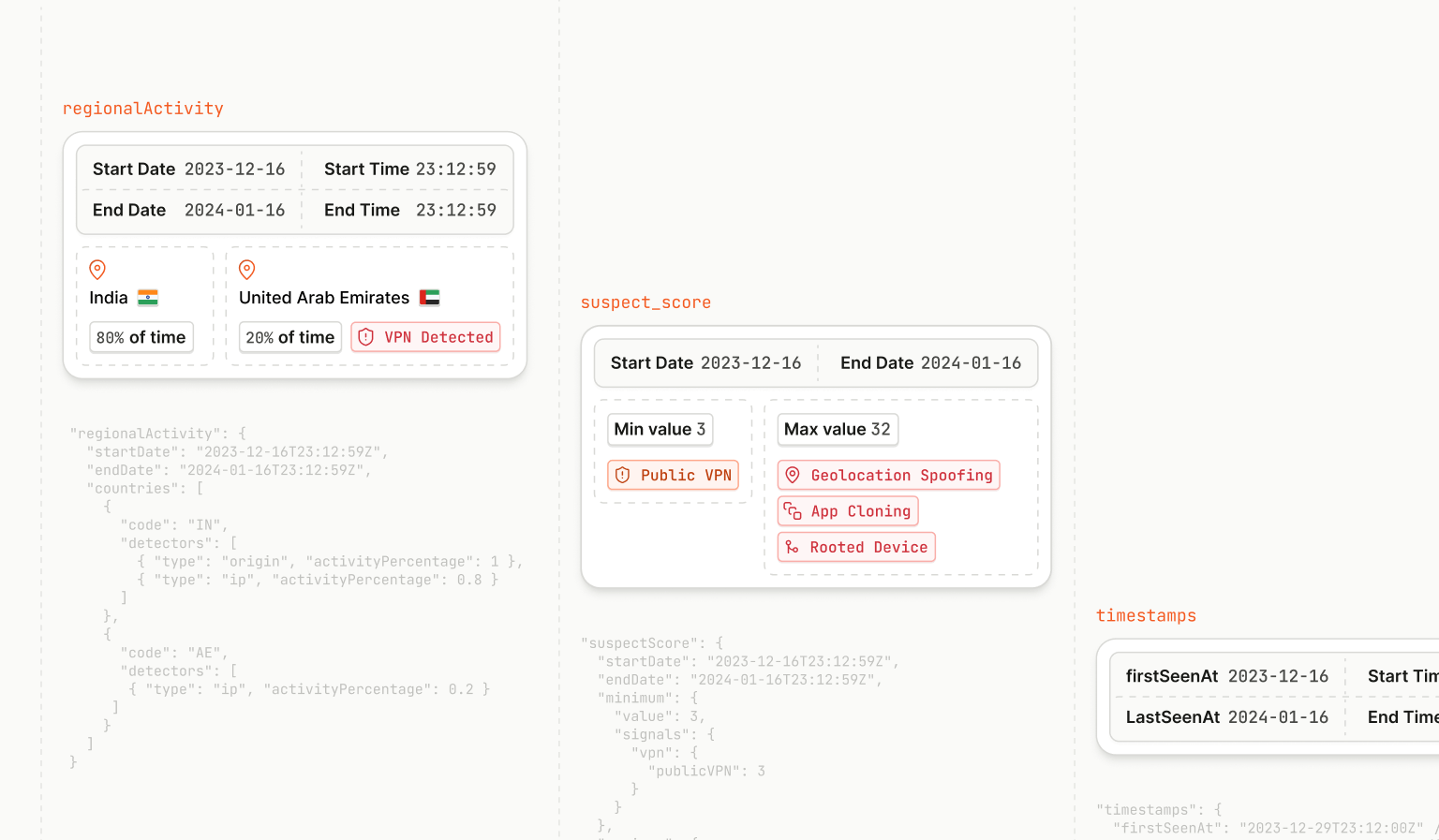
Here’s an example activityPercentage scenario: Let’s say that a device is physically based in India and is also active in the United Arab Emirates (UAE) 20% of the time via VPN. If the device is using the supported version of the Android SDK and the originCountry is available, the response could look like this:
"regionalActivity": {
"startDate": "2023-12-16T23:12:59Z",
"endDate": "2024-01-16T23:12:59Z",
"countries": [
{
"code": "IN",
"detectors": [
{ "type": "origin", "activityPercentage": 1 },
{ "type": "ip", "activityPercentage": 0.8 }
]
},
{
"code": "AE",
"detectors": [
{ "type": "ip", "activityPercentage": 0.2 }
]
}
]
}suspect_score
The Suspect Score is a weighted representation of all Smart Signals collected from a device that helps identify suspicious activity. You can read more in this Smart Signals Guide. The Suspect Score is calculated for each Fingerprint API request that your application makes with the Android SDK.
The DRN version of the suspect_score is powerful, as it represents the minimum and maximum Suspect Scores we captured from the identified device in the last 30 days globally across the entire Fingerprint device network.
The maximum value contains a zero-excluded percentile, which makes it easy to see how suspicious that device was compared to other suspicious devices. For example, if the percentile of the maximum suspect score is 0.95, it means that that device was more suspicious than 95% of other suspicious devices in the same 30-day time period.
Here’s an example response for a relatively suspicious device:
"suspectScore": {
"startDate": "2023-12-16T23:12:59Z",
"endDate": "2024-01-16T23:12:59Z",
"minimum": {
"value": 3,
"signals": {
"proxy": 3
}
},
"maximum": {
"value": 20,
"percentile": 0.75
"signals": {
"ipBlockList": 12,
"vpn": {
"publicVPN": 5
},
"proxy": 3
}
}
}timestamps
The data we provide in the timestamps signal is very straightforward but can be a useful indicator for suspicious activity. For example, if a device that was only seen globally very recently is trying to access a well-established account, this may indicate a potential account takeover attempt. This DRN data is available as firstSeenAt and lastSeenAt within the timestamps property.
"timestamps": {
"firstSeenAt": "2023-12-29T23:12:00Z" // RFC3339 formatted UTC time with minute precision
"lastSeenAt": "2023-12-29T23:12:00Z" // RFC3339 formatted UTC time with minute precision
}Strengthen your defenses with historical device data for Android
With this new global device data for Android, you can get even clearer insights into your visitors, even when they are using your app for the first time. From regional data revealing impossible travel patterns, to aggregated suspicion levels based on prior activity or simply indicating a visitor’s first appearance in our network — our new global insights can help you better detect and prevent fraud. You can find more examples and detailed documentation on our new DRN API here.
FAQ
The Fingerprint Device Reputation Network (DRN) is the world's first developer-centric, self-serve network of device information. With Fingerprint's DRN, Android SDK users can query the network using the visitor ID from an identified device and gain crucial historical insights into that user's prior behavior and characteristics of that Android device.
Insights include information on a device's location history and past suspicious behavior over the last 30 days. The DRN supports three global signals: Regional Activity, Suspect Score, and Timestamps.
The DRN is available at no extra charge for all Fingerprint Android SDK users, whether you're using our self-serve offering or our enterprise plans.