Summarize this article with
Spam accounts can be a direct threat to any platform that relies on real users and clean data. If you run a fintech company, SaaS platform, marketplace, or social network, you know the drill: one day you’re celebrating a surge in signups, and the next you’re buried in fake accounts, fraudulent transactions, and analytics you can’t trust.
The real challenge isn’t just blocking obvious bots. It’s stopping sophisticated spam operations before they slip through and cause real damage. If you care about your platform’s integrity, spam prevention is essential.
The real risks: Fraud, bad data, and platform abuse
Spam accounts are a launchpad for fraud. They’re used to exploit sign-up incentives, test stolen payment methods, and make fraudulent purchases. One fake account can siphon off thousands of dollars. Multiply that by hundreds, and you’re looking at a serious financial mess.
But it’s not just about money. Spam accounts poison your data, making it nearly impossible to tell genuine user behavior from noise. Skewed analytics lead to bad product decisions, wasted marketing spend, and misleading reports to investors or regulators. For regulated industries, fake accounts create compliance nightmares. Know Your Customer (KYC) checks are pointless if anyone can spin up unlimited fake identities. You might even end up dealing with data breach notifications if spam accounts access sensitive info.
And then there’s platform abuse. Spam accounts flood your marketplace with fake listings, manipulate reviews, and launch coordinated attacks that disrupt your service for everyone else.
How spam operators work: Bots, fake emails, and proxies
Today’s fraudsters use automation, clever workarounds, and distributed infrastructure to slip past basic defenses.
- Automated bots: Headless browsers and automation frameworks can complete sign-up forms at scale. Many can mimic human-like behavior — moving the mouse, hesitating before clicking, and even solving CAPTCHAs using cheap third-party services.
- Disposable email services: Fraudsters bypass email verification by spinning up throwaway inboxes in seconds. Some use email aliases or compromised accounts to look even more legitimate.
- Proxies and virtual private networks (VPNs): Routing traffic through residential proxies or VPNs lets fraudsters appear to sign up from anywhere, making it tough to spot suspicious patterns based on IP address alone.
Why traditional defenses fall short
Remember when CAPTCHAs were the gold standard for stopping bots? Those days are over. Modern bots solve CAPTCHAs with cheap services or machine learning. Meanwhile, CAPTCHAs frustrate real users and create accessibility issues.
IP blocking isn’t much better. Fraudsters rotate through proxies and VPNs faster than you can update your blocklist. You might end up blocking legitimate users (think mobile carriers or corporate networks) while the real offenders slip right past.
Email verification used to be a decent filter, but not anymore due to disposable email services and automated inbox checkers. Sophisticated spam operations can automate the entire email confirmation process.
Rate limiting slows down bulk signups from a single source, but it’s not effective against distributed attacks where fraudsters spread requests across dozens of IPs, devices, and time zones. These tools still have a place in a layered defense, but shouldn’t be relied on them alone
Modern spam prevention: What actually works
If you want to stop spam accounts before they cause trouble, you need to move beyond legacy defenses. Here are the eight key techniques that actually work against today’s spam operations:
1. Bot detection
Dedicated bot detection tools can identify scripted signups by analyzing traffic patterns, interaction speed, JavaScript execution, and other signals that reveal automation. These tools are purpose-built to catch bots in real time, even those mimicking human behavior.
2. Email and phone verification
Low-effort spam often uses disposable emails or VoIP phone numbers. Validating email domains, checking for known temporary services, and analyzing phone number metadata (carrier, type, region) can filter out obvious junk. Adding lightweight verification steps, like email confirmation or SMS code entry, adds friction without blocking legitimate users.
3. Device fingerprinting
Device fingerprinting creates a unique identifier for each device based on hardware and software traits like screen resolution, installed fonts, browser plugins, and more. Unlike cookies or IP addresses, this identifier persists even if the user clears cookies, switches to incognito mode, or rotates IP addresses. The result: you can spot when the same device keeps popping up with new signups, even if everything else changes.
4. IP intelligence
Modern IP intelligence goes beyond blocklists. It identifies IP addresses tied to data centers, known proxies, or previous fraud. It can also spot geolocation inconsistencies like a user claiming to be in New York but signing up from an IP in Eastern Europe.
5. Behavioral analysis
Behavioral analysis examines how users interact with your site. Real humans move their mouse in unpredictable ways, make typos, and hesitate before clicking. Bots tend to act with robotic precision. Analyzing these patterns helps you spot automation and suspicious behavior in real time.
6. Signup velocity monitoring
Signup velocity monitoring tracks how quickly new accounts are being created from the same device, IP, or geographic area. If you see a spike in signups from a single device or network, it’s a strong indicator of a spam operation in progress.
7. Real-time risk scoring
Combining multiple signals into a real-time risk score lets you trigger different responses based on threat level. Low-risk users proceed normally, medium-risk users might face additional verification, and high-risk attempts can be blocked on the spot.
8. Machine learning detection
Machine learning models can identify subtle patterns that indicate spam accounts by analyzing historical data on confirmed fraudulent and legitimate accounts. These models continuously improve as they process more data and can adapt to new fraud techniques.
The real magic happens when you layer these techniques. By combining device intelligence, behavioral cues, IP analysis, and velocity monitoring, you can spot and stop spam accounts before they ever get a chance to wreak havoc.
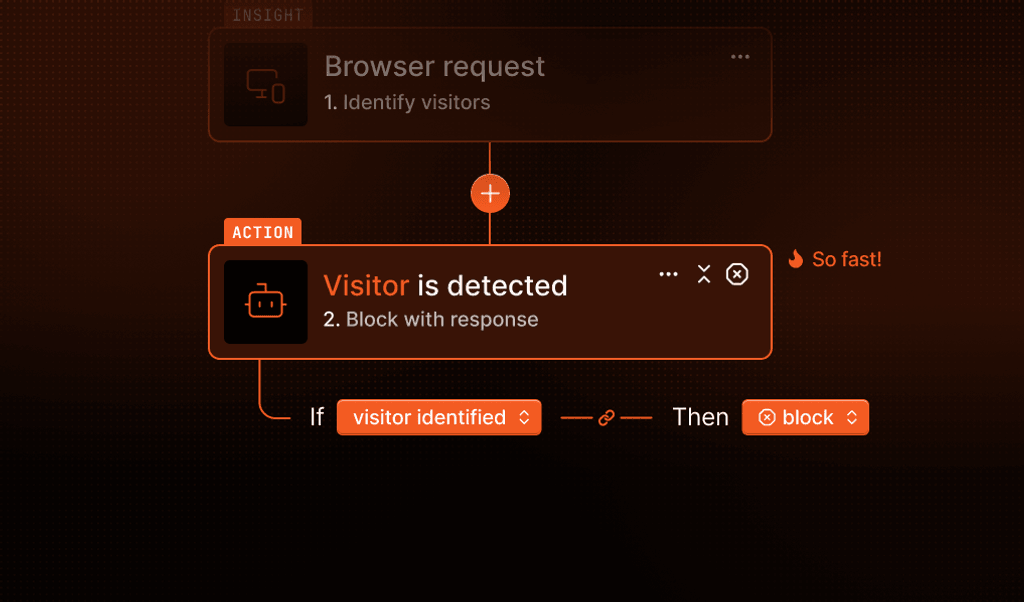
How Fingerprint blocks spam accounts before they start
Fingerprint is a device intelligence platform built for real-time fraud prevention. It uses over 100 signals to generate a persistent visitor ID for each browser or device, giving you a stable way to recognize returning visitors even if they clear cookies, use incognito mode, or use a VPN.
But Fingerprint doesn’t stop at identification. It also offers 20+ Smart Signals that go deeper, including:
- Bot Detection: Flags automated browsers and headless setups all in the background without annoying your users.
- VPN Detection: Identifies when a visitor is behind a VPN, making it harder for fraudsters to mask their true location.
- Browser Tampering Detection: Spots when someone is trying to disguise their environment with anti-detect browsers or manual tweaks.
- Incognito Detection: Reveals when users are trying to fly under the radar in private browsing mode.
- IP Blocklist: Checks if the visitor’s IP is linked to known proxies, Tor nodes, or past abuse.
- Velocity Signals: Highlights devices that are creating accounts at suspicious rates, even if they’re rotating IPs or emails.
Fingerprint works in real time. As soon as a user lands on your signup page, Fingerprint can collect device and behavioral data and provide Smart Signal checks. If something looks off, you can block or challenge the signup immediately.
Here’s a simple example of how Fingerprint can be integrated into your signup flow:
// Initialize the agent.
const fpPromise = import("https://fpjscdn.net/v3/PUBLIC_API_KEY").then(
(FingerprintJS) =>
FingerprintJS.load({
endpoint: "https://metrics.yourdomain.com", // Optional
})
);
// Collect browser signals during account creation
const { visitorId, requestId } = await (await fpPromise).get();
// Send the requestId to your backend for validation
const response = await fetch("/api/validate-signup", {
method: "POST",
body: JSON.stringify({ requestId, email, username }),
headers: {
"Content-Type": "application/json",
},
});
On your server, you can use Fingerprint’s API to check for risky signals:
import { FingerprintJsServerApiClient, Region } from '@fingerprintjs/fingerprintjs-pro-server-api';
const client = new FingerprintJsServerApiClient({
apiKey: 'SECRET_API_KEY',
region: Region.Global,
});
// Validate the signup attempt
const event = await client.getEvent(requestId);
const botResult = event.products.botd?.data?.bot?.result;
const vpnResult = event.products.vpn?.data?.result;
const suspectScore = event.products.identification?.data?.suspect;
// Implement risk-based logic
if (botResult !== 'notDetected' || suspectScore > 50) {
// Block or challenge the signup
return { status: 'blocked', reason: 'High risk detected' };
}Fingerprint’s persistent visitor ID lets you build your own device reputation system over time. If a visitor ID is linked to previous spam or suspicious behavior, you can flag future attempts from that device for extra scrutiny or block them outright. This persistent identification is a game-changer for stopping repeated abuse.
Best practices for spam account prevention
Implementing spam account prevention isn’t a one-and-done project but an ongoing process. Here’s how to get it right:
- Start with monitoring: Before you start blocking, use Fingerprint to collect data and understand your user base. This helps you set appropriate thresholds and avoid false positives.
- Implement graduated responses: Don’t just block suspicious signups. Use a graduated response system: require additional verification, apply account restrictions, or flag accounts for manual review.
- Combine multiple signals: No single signal is perfect. Combine device identifiers, behavioral analysis, IP intelligence, and velocity monitoring for the most effective protection.
- Monitor and adjust: Fraud techniques evolve constantly. Regularly review your detection rates and false positives, and adjust your thresholds as needed.
- Consider user experience: Balance security with user experience. Only add friction when necessary, and provide clear feedback to legitimate users who might get caught by security measures.
Next steps: Build a robust defense
Spam account prevention is an arms race. Fraudsters adapt quickly, but so can you. Start by monitoring device activity and risk signals with a platform like Fingerprint to understand your baseline and spot suspicious patterns. Layer device fingerprinting, IP intelligence, behavioral analysis, and velocity monitoring to build a defense that adapts as threats evolve.
Don’t rely on a single signal. Combine multiple sources of intelligence and adjust your thresholds as you learn more about your users and attackers. When you spot high-risk behavior, respond with graduated measures: challenge, restrict, or block as needed, but always keep the legitimate user experience in mind.
Proactive spam prevention keeps your user base clean, your data trustworthy, and your platform ready for real growth. If you want to see how persistent device intelligence and real-time risk assessment can help, you can start a free trial or get in touch with our team for a deeper look at how these Smart Signals fit into your workflow. Staying ahead of spam isn’t easy, but with the right tools and approach, it’s absolutely possible.
Ready to solve your biggest fraud challenges?
Install our JS agent on your website to uniquely identify the browsers that visit it.
FAQ
Spam accounts can be used to post unwanted content, manipulate systems, or conduct malicious activity such as scams, phishing, or fraud. Spam accounts damage platform trust, skew analytics, and can have significant financial consequences on your business.
Fraudsters often use bots, stolen credentials, disposable emails, VPNs, and device farms to make spam accounts look like legitimate users.