Summarize this article with
Brute force attack prevention is a must-have for any authentication system. If you’re a developer or fraud specialist, you know that logins are a favorite target for attackers, whether they’re guessing weak passwords or running automated credential stuffing campaigns. The consequences? Account takeover, data breaches, and a headache for both your users and your team.
Let’s break down how these attacks work, why they’re so effective, and what layered defenses you actually need to keep them out.
Why brute force attack prevention matters
Leaving your login endpoints unprotected is an open invitation for trouble. Brute force attacks are automated, relentless, and ridiculously cheap to launch — attackers just need a script and a list of passwords. When they succeed, the fallout is ugly, resulting in account takeovers, data theft, fraud, and a mess of regulatory headaches.
Real-world incidents are everywhere. A “next‑level” brute‑force campaign in early 2025 leveraged nearly 2.8 million unique IP addresses every day to target VPN and networking devices from vendors such as Palo Alto Networks, Ivanti, and SonicWall — an attack of unprecedented scale powered by botnets and residential proxies.
The cost of cleaning up after an account takeover goes way beyond lost revenue. You’re risking user trust, your company’s reputation, and potential legal headaches.
The main brute force attack types
Understanding how these attacks work is half the battle. Here are the main types you’ll see in the wild:
Traditional brute force
This is the “try every possible password” approach. Attackers target a single account and hammer away with common passwords like “123456,” “password,” or slight variations. Sadly, many users still pick weak passwords, so this approach works more often than you’d think.
Credential stuffing
Credential stuffing is a more effective cousin of brute force. Attackers grab username and password pairs from previous data breaches and try them on your site. Since many people reuse passwords across multiple sites, this method delivers a high hit rate. It’s fast, automated, and tough to spot unless you’re actively looking for it.
Password spraying
Password spraying flips the script: Instead of targeting one account with thousands of guesses, attackers try a handful of common passwords (like “welcome1” or “password123”) across many accounts. This approach dodges most lockout policies and can sneak past basic rate limiting since you are only testing an account once.
Distributed and automated attacks
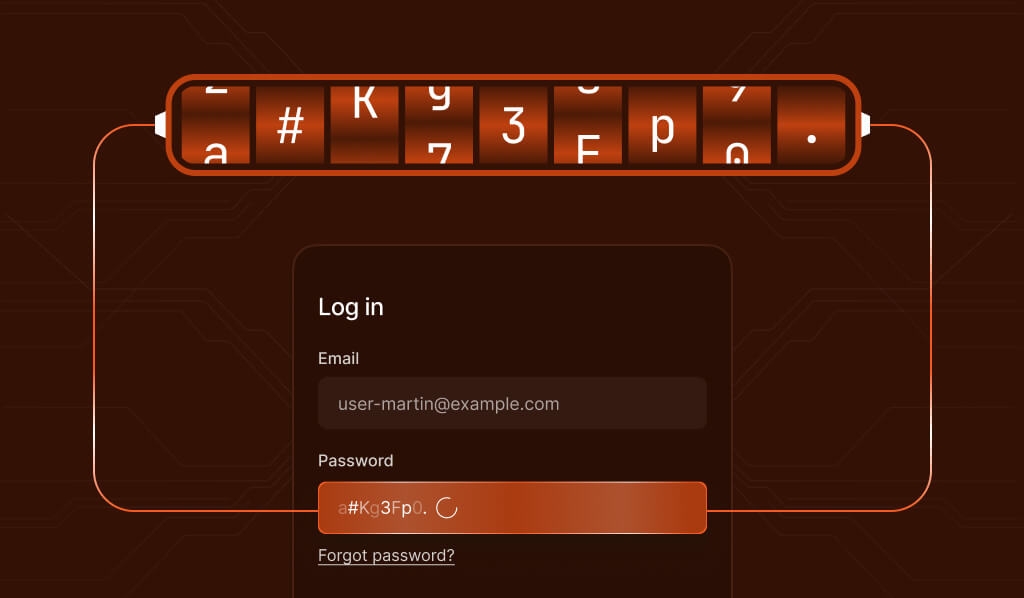
Modern attackers don’t stick to one IP address. Botnets and residential proxy networks let them spread login attempts across thousands of addresses, making IP-based blocking mostly useless. Automation tools can even mimic human behavior, making detection even trickier.
Core brute force prevention techniques
Wishful thinking won’t stop brute force attacks. Here’s what actually works:
Rate limiting
Rate limiting is your first line of defense. By capping the number of login attempts from a single source, whether it’s an IP address, user account, or device, you make large-scale guessing impractical. Progressive rate limiting, where delays increase with each failure, slows attackers even more. Just remember: distributed attacks can get around basic IP-based limits, so don’t stop there. Apply rate limiting at multiple levels:
- Per IP address for basic protection
- Per user account to prevent targeted attacks
- Per device fingerprint to catch distributed attacks using the same automation tools
Account lockout
Temporary account lockouts after a set number of failed logins can slow down attackers, but balance is key. Lock out too quickly, and you’ll frustrate real users who just forgot their password. Lock out too slowly, and attackers get more chances to get in. Progressive lockouts (increasing the lockout duration with each failure) and alerting users when their account is locked strike a better balance.
Multifactor authentication (MFA)
MFA is a brute force killer. Even if an attacker guesses or steals a password, they still need a second factor, like a code from an authenticator app, an SMS message, or a hardware token. MFA can still be bypassed but requires more effort from the attacker.
Password hardening
You can’t control user choices, but you can enforce strong password policies. Require longer passwords, ban the most common choices, and encourage passphrases. Even better, use password breach checks to block credentials known to have been compromised elsewhere.
How to detect brute force attempts in real time
Prevention is great, but you also need to spot attacks as they happen. Here’s what to monitor:
Failed login monitoring
Track failed login attempts per user, IP, and device. A sudden spike in failures is a classic sign of an attack. Don’t just count totals; look for patterns, like many failures for one account or many accounts targeted from one source.
Velocity checks
Velocity checks flag login attempts that happen too quickly to be human. If you see dozens of attempts per second, you’re probably looking at automation, not a forgetful user.
Behavioral analytics
Attackers don’t act like real users. Monitor for suspicious patterns, such as logins from unusual locations, activity at odd hours, or devices that suddenly change characteristics. Combine these signals to spot abuse early.
Layered detection
No single method catches everything. Combine IP intelligence (blocklists and geolocation), device intelligence (fingerprinting to recognize repeat offenders even across IP changes), and behavioral analysis (spotting anomalies in the login flow). This layered approach makes it much harder for attackers to slip through.
Set up automated actions for when thresholds are crossed, like multiple failed logins from a new device or velocity checks that indicate it could be a bot attack. This gives you a chance to respond before attackers succeed.
How Fingerprint strengthens brute force prevention
Traditional defenses are important, but modern brute force attack prevention calls for smarter tools. That’s where Fingerprint comes in.
Fingerprint is a device intelligence platform that helps you recognize visitors and spot suspicious activity, even when attackers use virtual private networks (VPNs), proxies, or incognito mode. Fingerprint assigns a unique visitor ID to each browser, using 100+ signals such as browser configuration, hardware details, and network attributes. This visitor ID is persistent across sessions, making it much harder for attackers to hide behind new IP addresses or just clear cookies.
Fingerprint doesn’t stop at identification. Its 20+ Smart Signals give you real-time insight into risky behaviors, including:
- Bot Detection: Detects automated browsers and headless tools like Selenium or Puppeteer in the background, so real users aren’t bothered with CAPTCHAs.
- VPN Detection: Flags when a visitor is using a VPN to conceal their true location.
- High-Activity Device & Velocity Signals: Spots devices with an unusually high amount of activity and notices impossible travel like changes in their IP or country.
- Browser Tampering Detection: Reveals if someone is using anti-detect browsers or trying to avoid identification.
- Incognito Detection: Indicates when visitors are using private browsing modes.
- IP Blocklist: Checks if an IP is linked to known proxies or attack infrastructure.
By layering these Smart Signals with your existing security stack, you can automatically flag or block high-risk authentication attempts, without adding friction for legitimate users. For example, you can require additional verification only when suspicious devices or behavior patterns are detected, keeping the login process smooth for everyone else.
Building defenses that actually work
Brute force attack prevention isn’t a one-and-done job. Attackers keep evolving, and your defenses should too. Start with the basics: rate limiting, account lockout, strong passwords, and multi-factor authentication. Then layer in real-time monitoring, behavioral analytics, and device intelligence to catch the attacks that slip through traditional nets.
Platforms like Fingerprint make it easier to spot and block automated brute force attempts using persistent visitor IDs and Smart Signals, so you can focus on building great products instead of playing endless games of whack-a-mole with bots. If you want to see how Fingerprint can help protect your authentication endpoints, try it out with a free trial. If you have specific questions about how to integrate advanced device intelligence into your stack, reach out to our team.
Ready to solve your biggest fraud challenges?
Install our JS agent on your website to uniquely identify the browsers that visit it.
FAQ
Attackers can use millions of rotating IPs from proxies, VPNs, and hijacked devices to evade simple IP-based blocks.