Summarize this article with
As fraud tactics grow more advanced, we’ve continued evolving Fingerprint to stay one step ahead. Last quarter, we shipped a wide range of improvements designed to help you detect more fraudsters and identify more returning visitors, and make smarter decisions faster — without adding friction to the user experience.
We released new features to help you:
- Identify more returning users with High Recall IDs
- Detect intercepted mobile app requests using a new Man-in-the-Middle (MitM) Attack Smart Signal
- Detect potential residential proxies
- Accelerate investigations with Smart Signal filtering in the Events API
- Reduce noise and billing impact by filtering out AI bot traffic
- Detect tampered requests using a new Tampered Request Detection Smart Signal
- Adhere to new Apple and Google application requirements with critical updates to our mobile SDKs
Let’s dive into what’s new.
High Recall ID: Recognize more returning users, power better experiences
Fingerprint’s standard browser identification is optimized to minimize false positives — where mistakenly trusting a fraudster is riskier than challenging a legitimate user — making it ideal for fraud prevention.
But for use cases like personalization, many users want to prioritize higher recall, helping them identify more returning, legitimate users, even if their browser environment has changed.
Where & how to use High Recall ID
High Recall ID can be used on its own or alongside the standard visitor ID. Together, they help tailor the user experience based on risk, intent, or behavior.
- Prevent account takeover: Add more friction when both IDs differ; less friction when only the standard ID has changed.
- Detect account sharing: When an account is associated with multiple High Recall IDs, it is a stronger indication of account sharing.
- Enhance personalization: High Recall ID enables you to serve returning users personalized content, offers, or recommendations — even if they’re anonymous.
Availability
We are happy to announce that a beta version of the High Recall ID is available for all Enterprise customers. Please contact your customer success manager to enable it for you.
MitM Attack Detection for Android & iOS
Man-in-the-middle (MitM) attacks are becoming more common, so we’ve launched a new Smart Signal to detect if requests to our servers have been intercepted or modified. The MitM Attack Detection Smart Signal enables you to:
- Detect network interception via tools like Burp Suite, ZAP, and Fiddler
- Flag traffic manipulation or SSL proxying
- Spot tampered mobile sessions in real time
Availability
The MitM Attack Detection Smart Signal is now available for Android and iOS devices. For more information, check out our documentation.
Tampered Request Detection for Android
Fraudsters are always looking for ways to manipulate device signals — and we just made it harder for them.
Our new Tampered Request Detection Smart Signal for Android flags when key device properties in a request appear to be manipulated or malformed, which can prevent accurate visitor ID generation and mask suspicious behavior. This helps your fraud teams detect attempts to spoof devices and bypass fraud controls like promo abuse detection.
Availability
The Tampered Request Detection Smart Signal is now available for Android devices (and coming soon for iOS). For more information, check out our documentation.
Residential proxy detection beta
Residential proxies route traffic through real household devices — like smart TVs or routers — to try to obfuscate a device’s location. So, we’ve enhanced the IP Blocklist Smart Signal to detect residential proxies. This gives you better visibility into advanced proxy-based evasion tactics.
Why it matters:
- Residential proxies are often used for multi-accounting, botting, and regional promo abuse
- They blend in with legitimate traffic and often bypass basic filters
- Detection is now built into your existing integration — no setup needed
This beta feature is live for enterprise Smart Signals customers and coming soon to Pro Plus plans. Log in to start using it today.
Smart Signal filtering in the Events Search API
You can now filter /events/search results by Smart Signals — like VPN, incognito, tampering, emulators, and more.
Why it matters:
- Pinpoint high-risk traffic instantly
- Automate fraud workflows
- Skip log exports and spreadsheets — filter with a single API call
This feature is live for Smart Signals customers. Log in to start using it today.
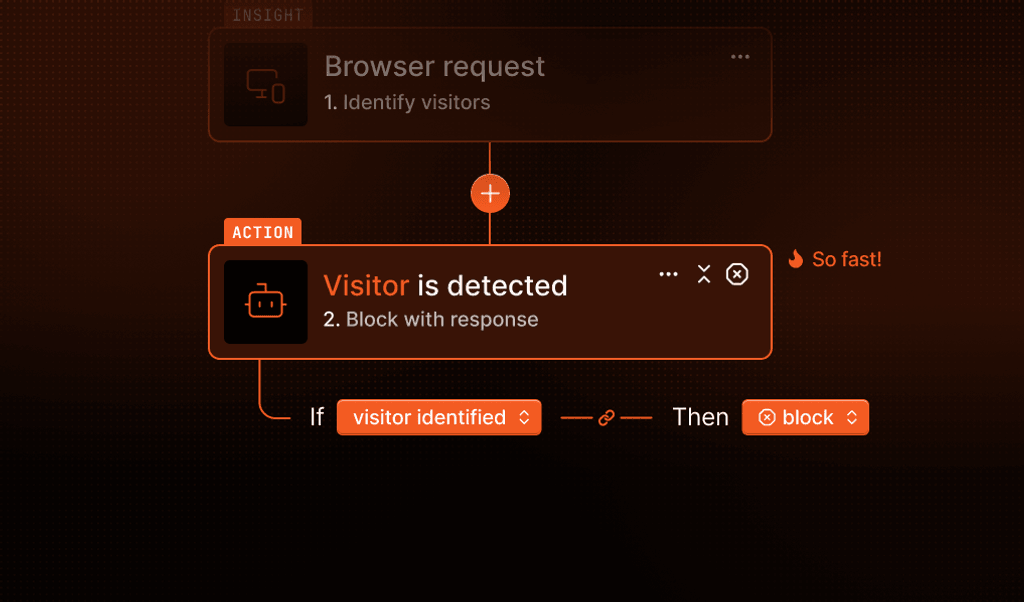
AI bot filtering: Clean up your Fingerprint data
AI bots scraping your site to train language models can flood your session data with irrelevant traffic. Now you can automatically filter out known AI bots from being fingerprinted — preserving your session volume and keeping analytics clean.
Why it matters:
- Remove noise from your data
- Avoid session billing for non-human traffic
- Focus your analysis on real users
This feature is live for all customers.
Updates to Android and iOS SDKs
We've made critical updates to our mobile SDKs to adhere to new Apple and Google application requirements. We strongly urge you to upgrade your apps.
What’s new:
- Detect whether requests from an app were subject to MitM attacks. See MitM Attack Detection to learn more.
- Added support for Open Client Response
For Android: Upgrade to v2.8.0 and follow the instructions outlined in Data Safety Requirements for Google Play to comply with Google’s Play Store requirements. See the full changelog
For iOS: Upgrade to v2.8.2. See the full changelog
That’s a wrap for Q2
Every feature is a step toward making Fingerprint more adaptive, transparent, and powerful for your team.
Need help with any of these features? Contact our team for guidance or book a demo.