Summarize this article with
Fraud evolves faster than traditional software release cycles. When new attack patterns emerge, waiting on backlogs, code pushes, and cross‑team coordination can turn hours into losses. That’s why we’re excited to introduce new no‑code capabilities, now in beta, that make it dramatically easier for fraud, risk, and product teams to understand device risk across their user base and take action at the edge — without adding to engineering burden.
With Fingerprint’s no‑code setup options and a visual Rules Engine, teams can go from visibility to fraud prevention faster and easier than before. Cloudflare customers can deploy at the edge using their existing Cloudflare footprint — and every customer can leverage our JS Agent, mobile SDKs, and Dashboard to explore device risk, build rules, and respond to threats quickly through an intuitive interface.
Key benefits include:
- Speed to action. Visual authoring and edge execution enable two main use cases out of the box: getting the big picture on your visitors' device profiles, and blocking or flagging potentially suspicious devices and bots, such as devices showing evidence of browser tampering or residential proxy use.
- Ongoing autonomy for fraud analysts and teams. Fraud teams can understand the device risk profile of their users, then use that information to implement and iterate on rules.
What’s available now in beta
There are two new capabilities that customers can use today:
- A no-code deployment method for Cloudflare users.
Deploy Fingerprint to the edge in minutes using a wizard that configures credentials and allows you to specify pages to watch — no custom code required. We chose Cloudflare edge deployment first to maximize speed, coverage, and value for a large share of customers. In parallel, we’re investing in an agnostic path through our Server API so you can use the same Rules Engine UI across environments. All users can continue to benefit from Fingerprint’s JS Agent, mobile SDKs, and Dashboard to quickly deploy device intelligence to websites and mobile apps. - A no-code Rules Engine.
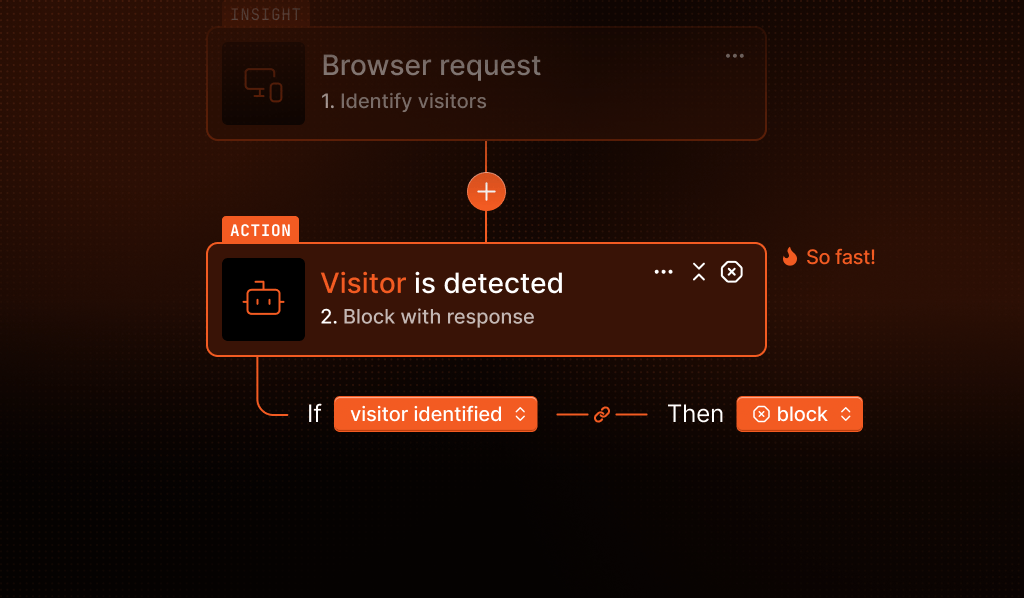
Our no‑code, if‑this‑then‑that rules builder is powered by 60+ real‑time device and browser signals (and growing) such as VPN/proxy confidence, browser tampering indicators, and device reuse patterns. Create rules to block, challenge, or flag suspicious traffic. Deploy changes quickly and iterate based on what you learn.
Learn Fast in Monitoring Mode
With these new no-code features, you can begin mapping device behaviors across your users to understand what’s anomalous (and what’s not) before turning on enforcement.
- Understand your device risk landscape.
See how many visitors exhibit potentially suspicious behaviors, such as leveraging browser tampering or using VPNs and residential proxies, and identify signs of tampering or automation attempts. Use these insights to inform policy — because not every “risky” trait is fraud in your context. One of the most valuable outcomes of device intelligence is knowing your baseline before you block. For example, learning that 90% of your users appear to be on VPNs may argue for a more nuanced approach than a blanket block. - React to emerging threats.
Build a custom rule in the Dashboard, choose the action, and deploy. For Cloudflare users, enforcement happens at the edge close to your users. - Start fast, grow thoughtfully.
Many teams begin in monitoring mode to compare detections with current decision systems before turning on enforcement. The Rules Engine makes that comparison easier and faster by surfacing real‑time detections you can map to your existing flows.
How it works
Ready to get started? Here’s how to get up and running quickly and begin exploring device risk in your own environment.
- Choose your setup path
Deploy quickly using our Cloudflare-based no-code wizard or continue using Fingerprint’s JS Agent and mobile SDKs. Our goal is a setup experience that’s fast today and increasingly agnostic over time. - Understand risk before you enforce
Use the Dashboard to monitor real-time device signals, learn your baseline, and understand how suspicious patterns show up in your traffic before taking action. - Build, deploy, and iterate visually
Create if-this-then-that rules using device and browser signals, choose an action (block, challenge, or log), and deploy updates quickly — with enforcement happening at the edge for Cloudflare users.
For detailed setup instructions and implementation guidance, and important notes and guardrails, see our Rules Engine and No-Code Deployment Setup Path documentation.
The Road Ahead
We’re optimizing propagation reliability, deployment ergonomics, and error transparency through our management APIs and Dashboard. Expect ongoing improvements to logging, rollbacks, versioning, and guardrails.
Get started
From visibility to enforcement, these new capabilities are designed to shorten time‑to‑value and put control in the hands of the people closest to the problem—your fraud and risk teams.
Ready to learn more? Check out our Rules Engine and No-Code Setup Path documentation
If you’d like a walkthrough tailored to your environment, we’re happy to help. Contact your Fingerprint team or use our self-service portal.