Summarize this article with
Staying on top of fraud and user behavior shouldn't require endless log files or reactive dashboard checks. That’s why we’re excited to introduce the Events Search API — a new way to programmatically query and filter event data from Fingerprint.
With this API, you can search historical visitor events by attributes like IP address, timestamp, Smart Signals, and more, all from within your own tools and workflows.
Why we built it
Customers have told us they want more control — not just in the dashboard, but through direct access to the data powering it. The Events Search API was built with that in mind: to support custom workflows, reduce reliance on internal tooling, and unlock deeper integrations with Fingerprint.
By making these search capabilities available via API, we’re continuing to expand our API-first approach, giving you faster access to the data that drives your fraud investigations and product decisions.
How teams are using the Events Search API
The Events Search API is ready to use for all Fingerprint customers, and teams across security, data, and product are already integrating it into their workflows. Here’s how you can start using it today:
- Automate investigations
Security and fraud teams can programmatically search for flagged visitor behavior, correlate traffic by IP, or filter for suspect events — no manual digging required. - Power internal tools
Platform and engineering teams are embedding real-time event search into internal dashboards, giving teams instant visibility into key user activity. - Streamline reporting and enrichment
Data teams can pull structured event data directly into reporting pipelines or enrich user profiles, without needing to store and manage all the raw event logs.
Let’s take a closer look at one of the most common and powerful use cases: fraud investigation.
Investigate fraud with layered filtering
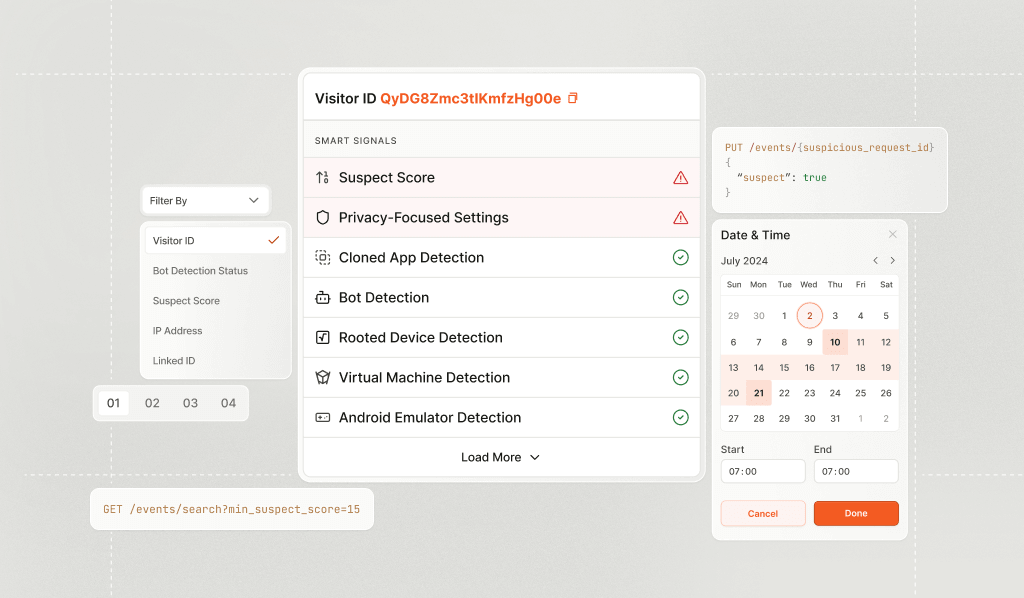
Fraud teams often begin investigations by filtering for events with a high Suspect Score, which is a configurable value based on Smart Signals like VPN usage, anti-detect browsers, or tampering attempts. This makes it easier to surface the riskiest sessions and cut through noise.
Once patterns emerge, teams can narrow the search further by combining multiple Smart Signals to isolate specific attack strategies. For example, if you’re investigating account takeover(ATO) attempts, you might filter for sessions using residential proxies (to mask IPs), anti-detect browsers (to spoof environments), and tampering (to bypass detection). This combination helps pinpoint coordinated ATO efforts designed to appear legitimate while targeting real user accounts.
To support long-term analysis, analysts can flag suspicious events directly via an API. These flagged events can be saved, revisited, or fed into internal tools and models, making future investigations even faster.
This layered approach — from high-level scoring to granular signal filtering and persistent tagging — gives security teams more precision and control in detecting fraud at scale.
Ready to get started?
The Events Search API is now available to all customers so you have more visibility, more automation, and more power in your hands. We can’t wait to see what you build.
Check out the API documentation
Questions or feedback? Reach out to your customer success manager or support team — we’d love to hear how you’re using it!