Many businesses rely on mobile apps to offer convenient and efficient services to customers anytime, anywhere. However, users can clone apps to exploit promotions and engage in fraudulent activities. This type of cloning involves users duplicating apps on their devices, creating multiple fraudulent profiles, and often undermining the app's security and business model. This blog post will explore user-initiated app cloning, its risks, and methods to detect these clones.
What is User-Initiated App Cloning?
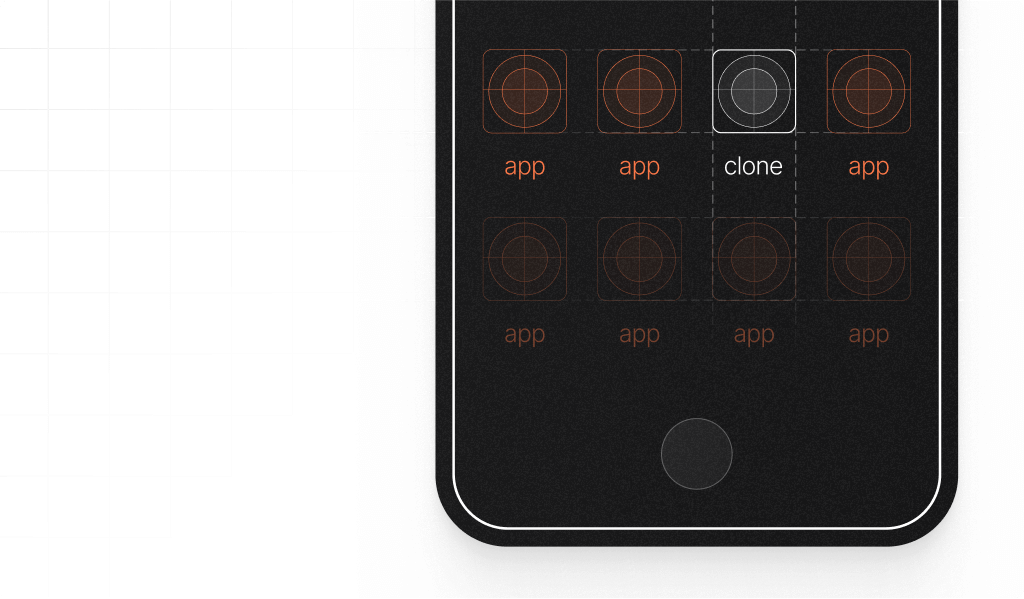
Users can clone apps by creating multiple instances of the same app on their device. This process typically involves downloading app cloning software like App Cloner or Parallel Space. These apps can clone other apps without the bad actor needing root access to their device. They then choose the app they want to clone, and the software makes a clone of the selected app and presents it as a new icon.
Each clone operates independently and can have unique user credentials or settings. From there, users can use the cloned app just like the original but can now log in with a second account they choose.
App cloning is much easier on Android devices, thanks to the platform's open and flexible nature. Many Android OEMs, like OnePlus’ OxygenOS with its Parallel Apps, already offer native app cloning tools, sparing users from needing third-party solutions. Google also experimented with integrating app cloning in the Android 14 beta. While it didn't make it to the final version, this suggests a future where app cloning might be a standard feature across Android devices.
Cloning apps can serve legitimate purposes, such as separating personal and professional profiles within a single app. However, bad actors can also exploit it to take advantage of promotions or attempt to access other user accounts. Using multiple clones, they can repeatedly benefit from offers intended for a single use per user and can also be more challenging for fraud prevention systems to detect.
Types of App Cloning Fraud
When a user clones an app, it operates like an entirely different user, disconnected from their original account. This duplication enables bad actors to engage in fraudulent activities that erode the app's revenue and integrity, harm other users, and diminish trust in the business. Here are some examples of how one can misuse app cloning:
Promotional Abuse
Users who clone apps to create multiple accounts can repeatedly exploit promotions, discounts, or referral bonuses, claiming first-time benefits or referral incentives. This practice causes financial losses for the business, drains resources meant for attracting genuine users, and disrupts marketing strategies.
Bypassing Usage Limits
Users actively get around usage limits set by platforms such as communication or storage tools and generative AI platforms. They alternate between accounts to exploit resources without providing fair compensation. This exploitation imposes undue stress on the application's infrastructure, potentially degrading the quality of service for other users.
Ban Evasion
Cloned apps provide a workaround for users facing bans or restrictions, enabling them to continue using the service under a different account. This evasion undermines the enforcement of app policies and rules, compromising the app's ability to offer a secure and equitable environment, thus degrading the overall user experience.
Vote Manipulation and Gaming the System
Users can misuse app cloning to manipulate votes and create fake reviews for personal gain, skewing data accuracy and public perception. Similarly, in competitive gaming apps, they can exploit the system to gain advantages unfairly, such as competing against themselves or harvesting rewards across multiple accounts. This manipulation leads to unfair personal gains, undermining the app's integrity, leading to potential user distrust and decreased genuine engagement.
Account Takeover
Bad actors may try to use cloned apps in account takeover schemes where they attempt to access other users' accounts. Since each cloned app looks like a new user, it can be difficult for businesses to detect suspicious behavior. Undetected account takeover attempts can result in significant data breaches, eroding user trust and potentially leading to legal repercussions due to compromised user data.
Detecting the Use of Cloned Apps
With the potential risks associated with app cloning, businesses must be able to detect the usage of cloned apps. Various methods can perform this detection, such as checking device identifiers, analyzing app usage patterns, and implementing anti-fraud algorithms. Watching for suspicious app cloning activity with just user device IDs may not be enough. A clever bad actor can use advanced cloner apps that spoof or randomize identifiers like Android ID, IMEI, MAC address, and more. These techniques make their cloned profiles look like separate devices, even if they are not.
How can businesses see through the tricks when cloner apps might be able to emulate some device fingerprints? Discrepancies will inevitably emerge when you correlate multiple device signals rather than relying on a single ID as the source of truth.
Some techniques to counter spoofed IDs:
- Combine multiple device signals into a composite identifier instead of depending on a single device ID. Using more signals to identify a device increases the likelihood of obtaining a stable identifier.
- Analyze app background data, battery, and memory use. These patterns can reveal if the "different" devices exhibit suspiciously similar device usage, which is very hard to fake.
- Monitor activity timing and access patterns. Genuinely different users will behave differently even on the same device IDs. Similarities in usage represent app cloning risks.
With the correlation of device signals, supplemented by user verification and behavioral analysis, you can reliably detect spoofed app clones and control fraud risks.
Leveraging Fingerprint Smart Signals Cloned App Detection
The Fingerprint Device Intelligence Platform offers visitor identification that analyzes over 70 signals to create a stable identifier, making it difficult for cloners to spoof their presence. However, with advanced app cloning software, it is possible to run multiple cloned instances of an app on the same device with potentially randomized signals.
This potential randomization is why Fingerprint Smart Signals offers a cloned app detection flag when users connect to your services. By checking this flag, you can tell if a user has cloned your Android app, allowing you to create strategies to prevent the misuse of your services. When you detect the flag:
- Challenge users with additional authentication steps like one-time passwords or 2-factor authentication. Real users can pass these easily, while it can be difficult for cloners to replicate at scale.
- Raise risk scores in your fraud algorithms for the user and visitor ID. Reduce benefits, promos, or access given to potentially cloned apps.
- Leverage other Smart Signals like factory reset detection, device tampering detection, and IP blocklists to get more data for fraud prevention decisions.
With cloned app detection and other device intelligence signals, Fingerprint empowers you to craft targeted business logic, from soft friction to hard blocking, to control abusive app cloning behavior.
Conclusion
Cloned apps pose a significant risk to businesses that can lead to substantial financial losses, service erosion, and data breaches. With the potential for misuse, promo abuse, manipulation, and account takeover, businesses must be able to detect and prevent the use of cloned apps by bad actors.
Fingerprint offers a practical solution that combines robust device identification and cloned app detection that businesses can use to protect themselves and their users from the negative consequences of app cloning.
Contact our sales team to learn more about how Fingerprint Smart Signals can help you prevent fraud while giving your users a smooth experience.