Frida is an open source dynamic instrumentation tool kit that allows developers and security professionals to inject code into the runtime of applications to monitor and manipulate their behavior.
Frida is widely used in the field of security assessments, penetration testing, and vulnerability research. Security professionals use Frida to identify and exploit security vulnerabilities in applications, making it a valuable tool for enhancing the security posture of software.
Frida also provides debugging and tracing capabilities, allowing developers to trace the execution flow, inspect variables, and debug applications at runtime. This is helpful for diagnosing issues and improving the overall stability of the software.
In this article, you'll learn more about Frida—how it works, what it's used for, and the challenges and ethical considerations to keep in mind.
What Is Frida and How Does It Work?
Frida started through the collaborative brainstorming of Ole André V. Ravnås and Håvard Sørbø, who wanted to transform the tedious process of manual reverse engineering into something more engaging and productive. The first version of Frida was released in 2014.
Today, developers and security professionals use Frida to inject snippets of code—for example, JavaScript or C—into native apps on a desktop, a mobile device, or an embedded system at runtime.
This ability to modify live code makes Frida useful for intercepting and altering function calls in real time as well as for inspecting or modifying the memory of running applications. Frida can also give you insight into how your software operates, help you debug software in real time, and enhance software functionality. These uses make Frida a valuable tool in application security, penetration testing, reverse engineering, and malware analysis.
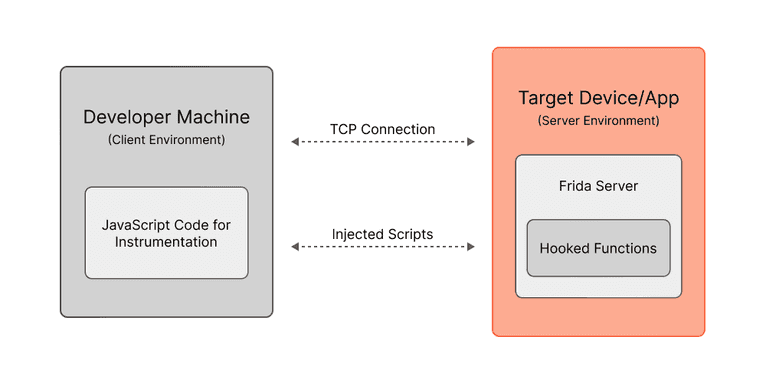
Like most instrumentation tools, Frida operates on a client-server architecture. The server component gets loaded into the target process, which could be any application whose behavior the developers are interested in analyzing or modifying.
The client, on the other hand, is where you, as the developer, write and run the JavaScript code to instrument the target process. This JavaScript code interacts with the Frida server to alter the behavior of the target application at runtime. The communication between the client and server occurs over a transmission control protocol (TCP) connection, which enables the remote instrumentation of the software.
One of Frida's key features is function hooking. It involves intercepting calls to specific functions and modifying the arguments, the return value, or the behavior of the function itself by rewriting the machine code of the target function at runtime. The hooking is orchestrated by Frida's JavaScript API, which provides a variety of powerful primitives to inspect and modify the runtime of the application. This capability allows you to use Frida for real-time analysis and manipulation of software systems.
Frida has extensive cross-platform support that covers Windows, macOS, Linux, iOS, Android, and QNX, and it supports a wide range of architectures like x86, x86_64, ARM, and ARM64. The tool kit also provides bindings for various languages like Python, .NET, Swift, and Q, which makes Frida an adaptable choice for developers and security experts with diverse language preferences. A user-friendly API makes Frida even more accessible.
Why Use Frida?
As mentioned, Frida is primarily used for application security, penetration testing, reverse engineering, and malware analysis.
In application security, Frida's ability to inject code into a running application and alter its behavior allows security professionals to perform real-time vulnerability assessments and remediation. Security professionals can observe how the application behaves under unexpected or malicious conditions. This might include testing how the application handles corrupt inputs or observing whether injected code can trigger unintended behaviors.
Frida's function hooking mechanism also makes it useful for penetration testing and vulnerability assessment. Testers can use Frida to intercept and modify function calls to uncover potential vulnerabilities in the software. For example, Frida can be used to bypass security checks, alter control flow, or even reveal sensitive information that might be processed within the application. Such dynamic analysis provides a deeper understanding of how the application behaves to identify vulnerabilities in an application that are not always apparent through static analysis.
Frida also plays an important role in reverse engineering and malware analysis. Because Frida enables analysts to interact with an application in real time, it helps them understand the app's behavior and internal processes better.
Some of the most important use cases in reverse engineering and malware analysis are listed below:
- Dynamic analysis of malware: Injecting code into the malware process at runtime allows you to monitor its behavior and trace its execution to understand how it works and its impact.
- Reverse engineering: Frida's ability to intercept and modify function calls can be used to identify proprietary algorithms, undocumented code, or hidden functionalities.
- Penetration testing: Frida's function hooking mechanism allows penetration testers to bypass security checks, alter control flows, and reveal sensitive information processed in an application.
- Debugging and tracing: Injecting code into a running application allows developers to identify bugs, performance bottlenecks, or unexpected behavior in real time.
- Automated testing: Frida's scripting capabilities can be used to create custom testing scripts that interact with the application at runtime.
- Intercepting API calls: Frida's function hooking allows you to intercept and modify API calls to understand how an application interacts with external systems and libraries to identify potential security risks during the API call process.
- Network traffic analysis: By hooking into the network-related functions of an application, Frida can be used to monitor, analyze, and manipulate network traffic to identify potential data leakages and test the response of the application to various network conditions.
Challenges Using Frida
Using Frida is not without challenges, though. To use Frida effectively, it's important to understand and know how to overcome these hurdles.
Platform and Architecture Compatibility
Even though Frida has broad compatibility, it's not equally effective across platforms and architectures. Some features of Frida might work with no problem on a common platform or architecture, but they can exhibit different behaviors on less common or older platforms and architectures.
For example, using Frida with devices on older Android versions may cause the system to crash when launching the app. But a user also reported an issue when running frida-server on a rooted Samsung Galaxy S21 Ultra with Android 11, even though the same frida-server ran without errors on a rooted Galaxy S8 with Android 9. This suggests that even new versions of an operating system may sometimes have compatibility issues.
Compatibility issues can also arise because of variations in operating system implementations or hardware configurations.
Ensuring Frida's compatibility and effectiveness on certain specialized platforms or for certain hardware configurations may require customization. This, in turn, requires diving deep into the documentation, engaging with the community for insights, and coming up with your own solutions, all of which take time and effort.
For example, patching memory in Frida is dependent on the platform and architecture. To ensure that Frida is compatible with the specific architecture of the target device (eg ARM, X86, AArch64, or MIPS) for this use case, the user must select the correct code generation writer.
Script Complexity
Writing effective Frida scripts requires a good understanding of the target application's architecture, function call conventions, memory layout, and more. The complexity increases if the application is more complex or more sophisticated security measures are used.
Performance Overhead
Dynamic instrumentation means an extra layer of code execution and more performance overhead, which can increase CPU use and memory consumption and make an application less responsive. The degree of overhead depends on the complexity and frequency of the instrumentation tasks that are being performed.
If you're using Frida for real-time analysis or modifying an application, keep these performance implications in mind. If the target application is performance-sensitive or must respond in real time, even a slight delay because of Frida's performance overhead can cause undesirable behavior or a degraded user experience.
For instance, using Frida on a mobile game for real-time analysis or to modify the game could increase CPU usage and memory consumption so much that the user experiences a reduced frame rate. In a game that requires fast reactions, even slight delays would worsen the gaming experience.
Rooting or Jailbreaking Requirements
The usual security measures on mobile platforms like Android and iOS restrict unauthorized access to system processes and resources. Using Frida to inject scripts into processes and perform dynamic analysis requires privileges that you can only achieve by rooting or jailbreaking the device.
Rooting (on Android) or jailbreaking (on iOS) can be a challenging task, especially if you're not well-versed in mobile operating systems. The availability and effectiveness of rooting or jailbreaking solutions also vary between different device models and operating system versions.
Besides these technical challenges, rooting or jailbreaking a device usually voids the warranty of the device. It can also violate the terms of service or even certain legal regulations, depending on the jurisdiction you're in.
Alternatively, if you are the application owner and you can make changes to the source code, you can embed Frida’s Gadget, a shared library that allows you to use Frida for analysis when using injected mode isn’t possible. Embedded mode means you no longer need a jailbroken device.
Anti-Frida Countermeasures
As Frida has become more popular and since it can be used for malicious purposes, applications increasingly use anti-Frida techniques to detect or prevent Frida's presence and operations.
Anti-Frida techniques include checks for known Frida signatures and monitoring for unusual activity that might indicate Frida's operation—such as unexpected memory accesses or function hooks, or techniques that make it harder to understand and instrument the application code.
Anti-Frida measures hinder the ability to hook certain functions or cause the application to crash or behave unpredictably when Frida is detected.
Security Concerns and Ethical Considerations
As mentioned above, Frida's capability to modify the runtime behavior of applications can be exploited maliciously to bypass security checks or extract sensitive data. Using it ethically means you need to get proper authorization before analyzing or modifying software you do not own or are explicitly permitted to test.
Potential malicious use also means you need to implement detection measures and obfuscation techniques to secure your applications against unauthorized dynamic instrumentation using Frida or similar tools. It's especially crucial if your app handles sensitive or valuable information—such as financial transactions, personal data, or proprietary code—that could lead to fraud, data breaches, or intellectual property theft.
Services like Fingerprint's Frida Detection enhance the resilience of your app by helping to identify and mitigate attempts to instrument your app using Frida and similar tools.
Alternatives and Complementary Tools
There are several alternatives to Frida as well as complementary tools to facilitate dynamic instrumentation of software. Here are some noteworthy ones:
- Xposed Framework (Android) allows users to modify the behavior of the Android system or apps. While Frida is designed as a dynamic instrumentation framework focusing on code injection, Xposed is more suitable for permanent modifications of an app.
- Drozer (Android) is an extensive security audit and analysis framework for Android that's best used for automating vulnerability detection in Android apps and devices.
- Cycript is an alternative to Frida that lets you explore and modify running applications on either iOS or macOS. Like Frida, it offers capabilities for dynamic analysis, manipulation, and exploration of running applications.
- GDB (GNU Project Debugger) is a portable debugger that supports many languages and platforms. Its functionalities in traditional debugging tasks—such as step-by-step code execution, inspecting variables, and analyzing core dumps, all of which are important for static analysis and understanding the structure of the program—make it complementary to Frida.
- IDA Pro is a reputable disassembler and debugger used for reverse engineering of binary programs. It can be seen as complementary to Frida: while IDA Pro is well suited for in-depth static analysis, Frida is better suited for dynamic analysis.
- Wireshark is a network packet analyzer that captures and analyzes network traffic. Wireshark is best used for network-level analysis, monitoring, and troubleshooting, while Frida is more suitable for application-level debugging.
Conclusion
Frida is a dynamic instrumentation tool kit that allows you to inject code into running applications to monitor and manipulate them in real time, which is useful for application security, penetration testing, reverse engineering, and malware analysis.
Using Frida does come with some challenges related to platform compatibility, script complexity, and potential performance overhead, though. The need for rooting or jailbreaking in some cases and Frida's potential misuse for malicious purposes such as fraud also pose legal, ethical, and security concerns.
To use Frida legitimately, make sure you have permission to analyze or modify any software you use it on. And to protect your application from malicious Frida use, consider services like Fingerprint's Frida Detection.
If you're curious to know more about Frida, feel free to visit its official documentation and GitHub repo. For more detailed insights into application and code-level instrumentation under Frida, check out the Frida HandBook.